Stream and Baseline Specific Actions in Batches
Stream Specific Actions in Batches
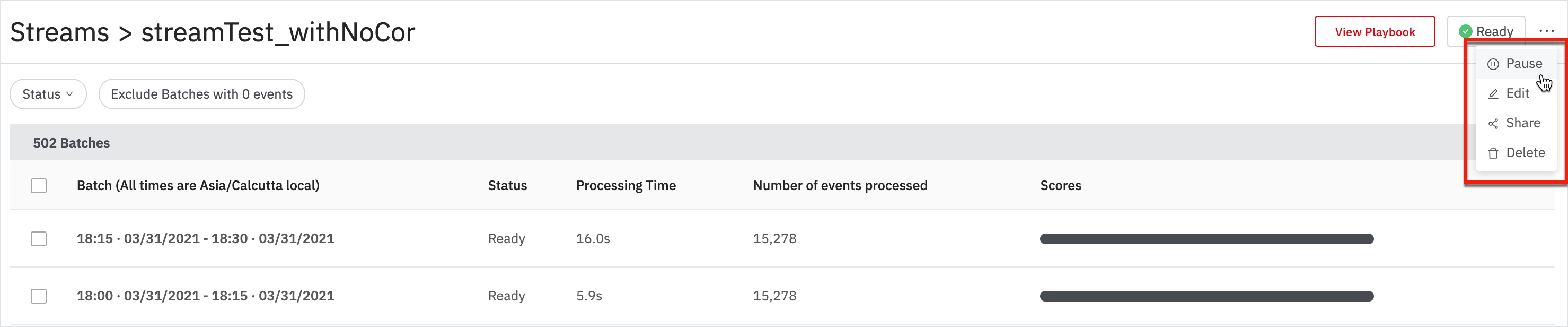
Streams allow you to perform Pause, Edit, Share, and Delete actions in the batches page for a selected stream.
Baseline Specific Actions in Batches
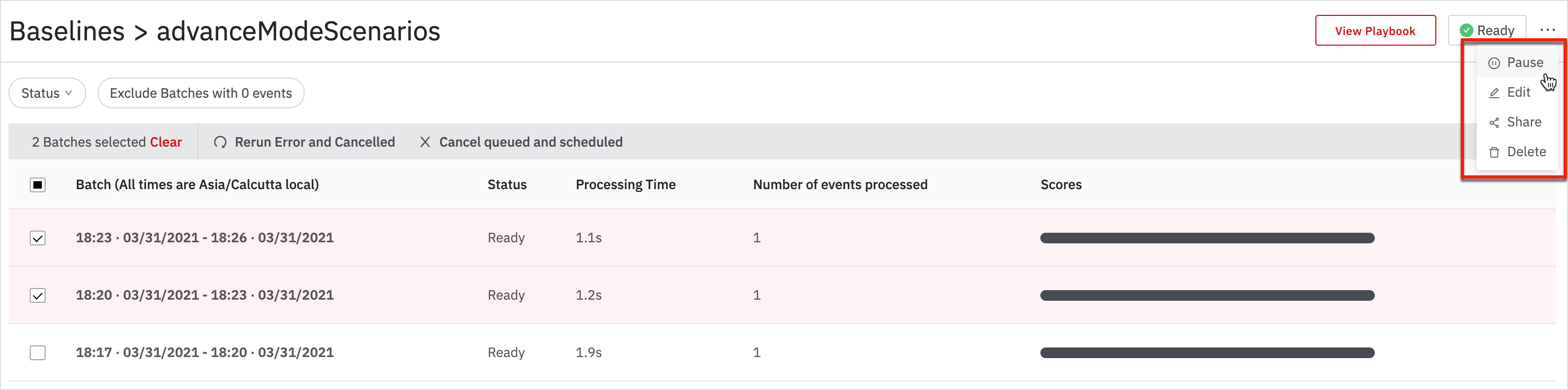
Baselines allow you to perform Pause, Edit, Share, and Delete actions in the batches page for a selected Baseline.
Updated over 2 years ago
What's Next