Flashpoint
Version: 2.0.0
Flashpoint is the globally trusted leader in risk intelligence for organizations that demand the fastest, most comprehensive coverage of threatening activity on the internet
Connect Flashpoint with LogicHub
- Navigate to Automations > Integrations.
- Search for Flashpoint.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- URL: URL to your Flashpoint instance. Example: https://fp.XXXX/api/v4.
- API Key/Token: API Token to Authenticate Flashpoint.
- After you've entered all the details, click Connect.
Actions for Flashpoint
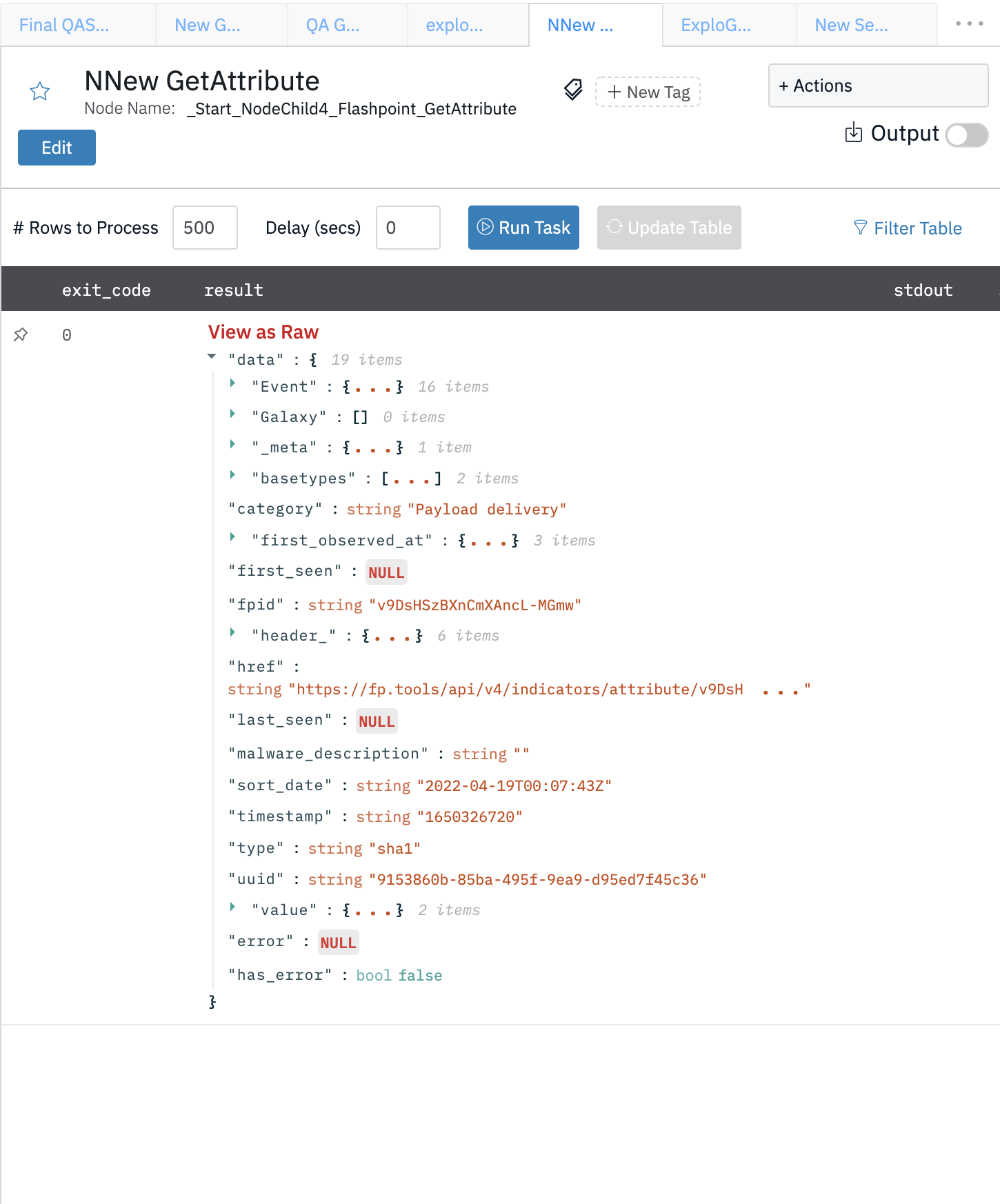
Get Attribute
This action is used to gather an attribute from the indicators API.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Attribute ID | Jinja-templated text containing the UUID or FPID that identifies a particular attribute. | Required |
| Format | Jinja-templated text containing the format that is supposed to be displayed. Accepted values are FP, MISP, or CSV. Note: Attribute endpoint currently only accepts FP format | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- response: SUCCESS
Get Attributes
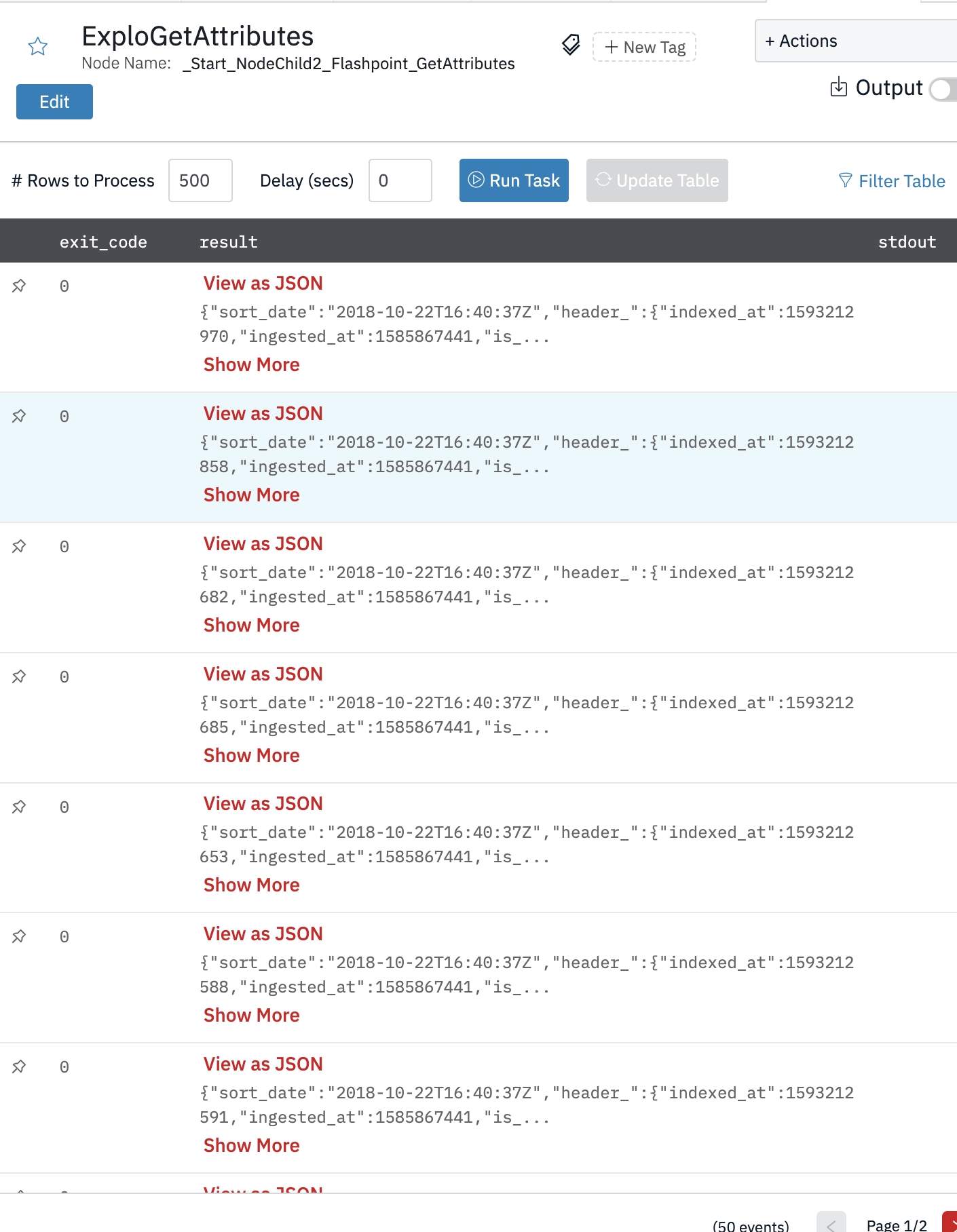
Method to gather attributes from the indicators API. This method is used to retrieve a list of indicators of compromise (IOCs) that occur in the context of an event.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Explode Results | Explode each result in a separate row. (Default is Yes) | Optional |
| Limit | Number of results to fetch. (Default is 1000) | Optional |
| Format | Jinja-templated text containing the format that is supposed to be displayed. Accepted values are FP, MISP, or CSV. Note: Attribute endpoint currently only accepts FP format | Optional |
| Start Date | Jinja-templated column name from the parent table that contains start date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| End Date | Jinja-templated column name from the parent table that contains end date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| Updated Since | Jinja-templated text containing the values created after the specified date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| Updated Till | Jinja-templated text containing the values updated or created until the specified date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| Search Tag | Jinja-templated text containing the Search for a keyword inside the Tags. Can have multiple keywords in a list, such as malware, ransomware. | Optional |
| Search Field | Jinja-templated text containing the Search specific value types. This should be a string of the format a=something, b>10 for each comparison. | Optional |
| Attack IDs | Jinja-templated text containing a comma-delimited list of MITRE ATTACK ids to filter events by. | Optional |
| Sort Timestamp | Jinja-templated text containing the Sort by the timestamp, either asc or des | Optional |
| Report | Jinja-templated text containing the items related to a specific report, identified by its FPID. | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- response: SUCCESS
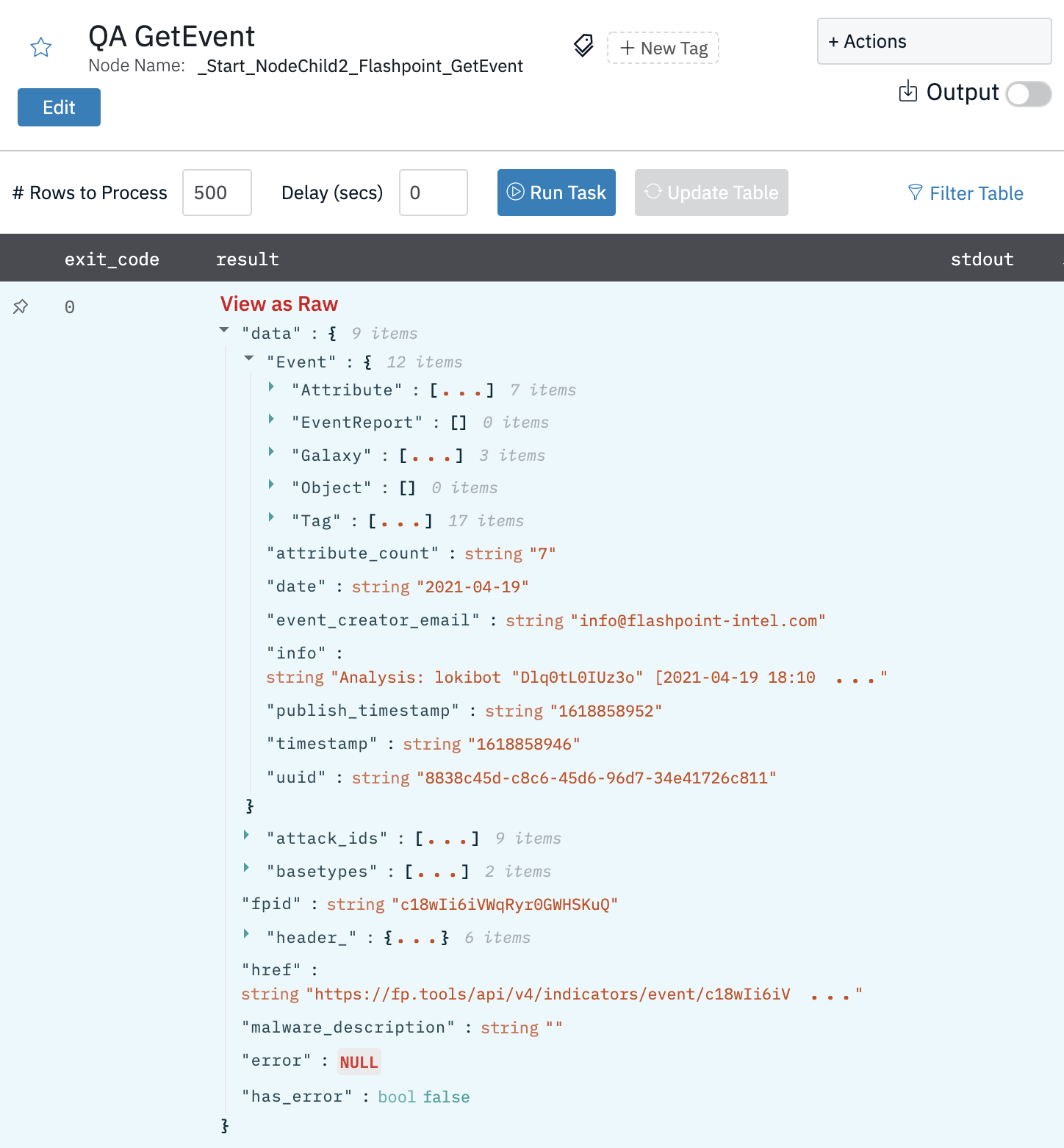
Get Event
Method to gather an event from the indicators API.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Event ID | Jinja-templated text containing the UUID or FPID that identifies a particular event. | Required |
| Format | Jinja-templated text containing the format that is supposed to be displayed. Accepted values are FP, MISP, or CSV. Note: Attribute endpoint currently only accepts FP format | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other JSON fields of each model
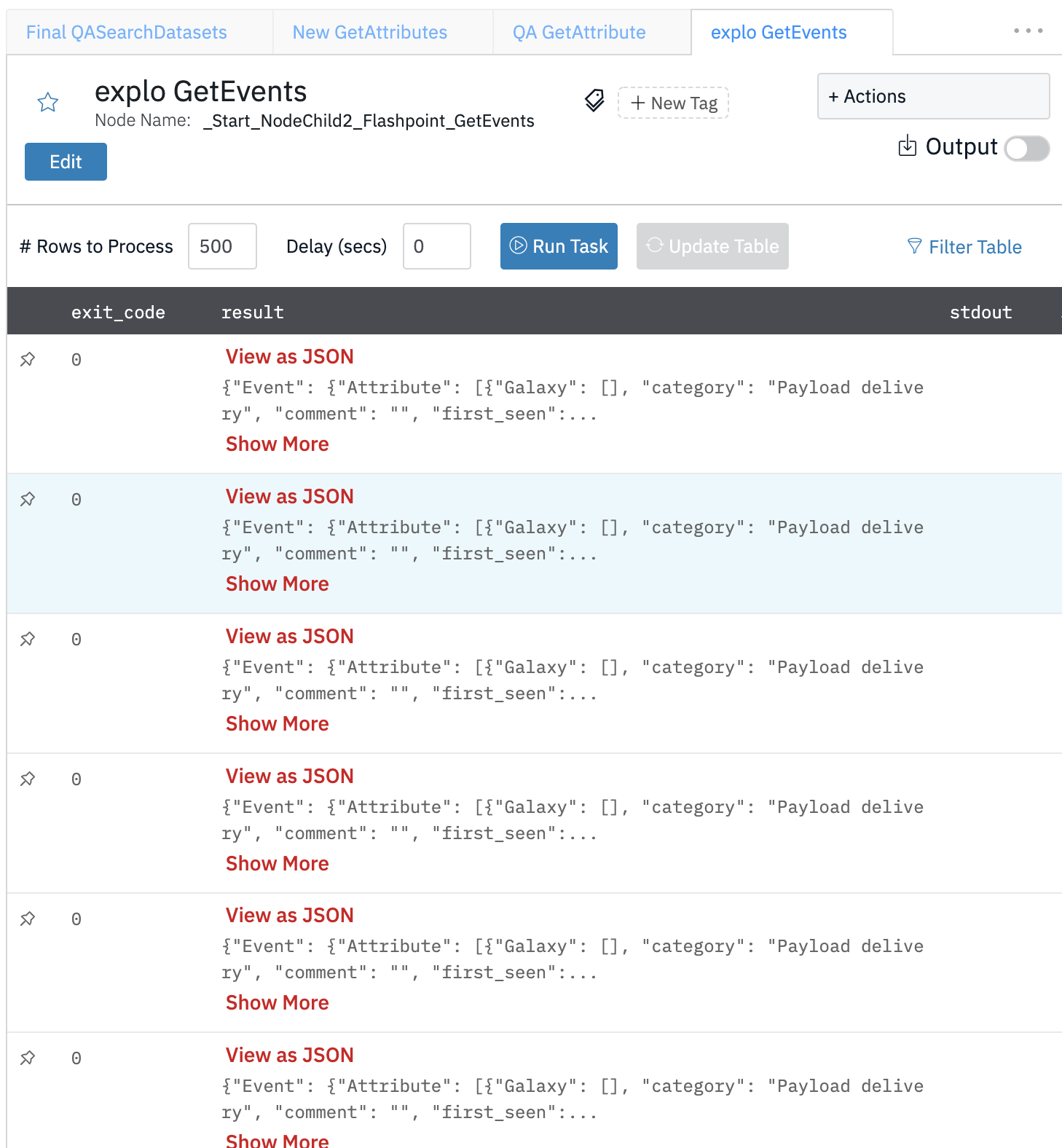
Get Events
Method to gather events from the indicators API. This method is used to gather a list of events. Events are groupings of different indicators of compromise that contain metadata about the situation where these indicators have been observed.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Explode Results | Explode each result in a separate row. (Default is Yes) | Optional |
| Limit | Number of results to fetch. (Default is 1000) | Optional |
| Format | Jinja-templated text containing the format that is supposed to be displayed. Accepted values are FP, MISP, or CSV. Note: Attribute endpoint currently only accepts FP format | Optional |
| Start Date | Jinja-templated column name from the parent table that contains start date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| End Date | Jinja-templated column name from the parent table that contains end date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| Updated Since | Jinja-templated text containing the values created after the specified date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| Updated Untill | Jinja-templated text containing the values updated or created until the specified date. Date format is in UTC and follows ISO_8601 or relative values. Example: YYYY-MM-DD or 30s, 5m, 2h, 3d, 2w, 3M, 2y | Optional |
| Search Tag | Jinja-templated text containing the Search for a keyword inside the Tags. Can have multiple keywords in a list, such as malware, ransomware. | Optional |
| Search Field | Jinja-templated text containing the Search specific value types. This should be a string of the format a=something, b>10 for each comparison. | Optional |
| Attack IDs | Jinja-templated text containing a comma-delimited list of MITRE ATTACK ids to filter events by. | Optional |
| Sort Timestamp | Jinja-templated text containing the Sort by the timestamp, either asc or des | Optional |
| Report | Jinja-templated text containing the items related to a specific report, identified by its FPID. | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other JSON fields of each model breach
Search Datasets
General search method. This method is used to execute queries against the Flashpoint Search API. It accepts a variety of keyword arguments corresponding to the Search API parameters. It also accepts a basetypes parameter to easily run broad queries on specific basetypes.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Explode Results | Explode each result in a separate row. (Default is Yes) | Optional |
| Basetypes | Jinja-templated text containing a list of basetype strings. The module fp_sdk. basetypes exists to assist with using basetypes. Example: ["conversation", "chat", "telegram", "container"] | Optional |
| Query | Jinja-templated text containing the Free text search query using ES URI search. Either query or q parameter is required. If both are provided the query takes precedence and q is ignored. | Required |
| Limit | Number of results to fetch. (Default is 1000) | Optional |
| Sort | Jinja-templated text containing a list of field:order pairs to sort the results by. Example: [“created_at:desc”, “author:asc”] | Optional |
| Source | Jinja-templated text that return _source object from returned hits | Optional |
| Fields | Jinja-templated text containing a list of fields to search against. Applies to query terms that don’t have fields names explicitly set in the query string. | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other JSON fields of Breach ID details
Release Notes
v2.0.0- Updated architecture to support IO via filesystemv1.0.1- Added 5 new actions.
Updated over 2 years ago