Playbooks
A playbook (formerly called a flow) codifies a security analyst's intelligence on how to analyze the imported data sets. A playbook incorporates the analyst's expertise in a logical process to take multiple inputs and apply data reduction and advanced correlation techniques to generate a single score or ranking as the output for each event. The playbook results in a decision for each event about whether it is acceptable or suspicious.
Playbooks and Permissions
To view or work with playbooks, you must be in a group that has Playbook permission. For more information, see Manage Users.
A playbook usually consists of multiple types of LogicHub entities, including the playbook itself, event types, connections, and so on. Your ability to include different entities in a playbook depends on whether you have access to those entities. A playbook that you have access to will execute even if you don't have access to all the entities that it includes.
Starting a Playbook
A playbook can begin with an event type or other automation that ingests data. In the graphical playbook creation process, you create steps based on the actions you want to perform and can view the results of each step and of the overall flow of the playbook. The playbook codifies the logic, and the playbook output is the ranking.
LogicHub offers two different playbook editors. You can switch between the two at any time.
- Easy Mode (default, recommended) allows you to create playbooks easily by selecting automation for steps without directly entering LQL (SQL) code.
- Advanced Mode provides direct control over all the details of the LQL code.
Steps
A playbook consists of steps (also called nodes) that perform functions that include ingesting data, executing automations, and doing calculations, tasks, scoring, and other operations.
- In the Easy Mode UI, all steps are set up as automations. They provide access to external systems, tools, and other functions that have been packaged as automations for ease of use.
- In the Advanced Mode UI, a step refers specifically to automation from the LogicHub automation library. Other types of steps, such as calculations and scoring, are labeled based on their function.
In Advanced Mode, you can use the Step option to create a diagram or summary of the playbook that you want to build, where each element is a defined automation. After creating the step, you can specify the type of automation: module or integration.
Module
A module is a step that automates a particular function, such as formatting output, parsing a string, or downloading emails. Modules are available in Easy Mode and Advanced Mode.
Integration
Integration is a step that interacts with other systems or tools to bring in external information about threats. Integrations are available in Easy Mode and Advanced Mode.
Computation
A computation step in Advanced Mode specifies a query that allows you to extract results from the data source. You can enter your own custom query, or select from a set of query operators or user-defined functions (UDFs). For example, you can add a computation step to a playbook to add a dimension to your dataset using LogicHub Query Language (LQL).
A computation step is shown with a green header.
Task
A task step in Advanced Mode uses a runSearch operator to run a search or a callScript operator to execute a script.
A task step is shown with a gold header.
Scorer
A scorer step in Advanced Mode is a mechanism to apply manual feedback from an analyst so that individual events can be scored higher or lower on an exception basis.
A scorer step is shown with a purple header.
Examples
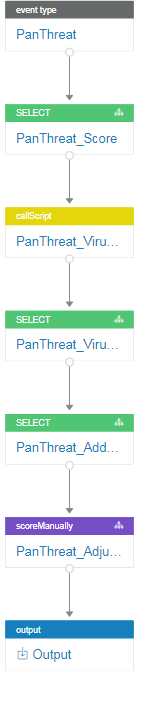
The following playbook flags suspicious URLs from a set of alerts.
Although the examples in this topic use Advanced Mode, you can create most playbooks using Easy Mode.
|
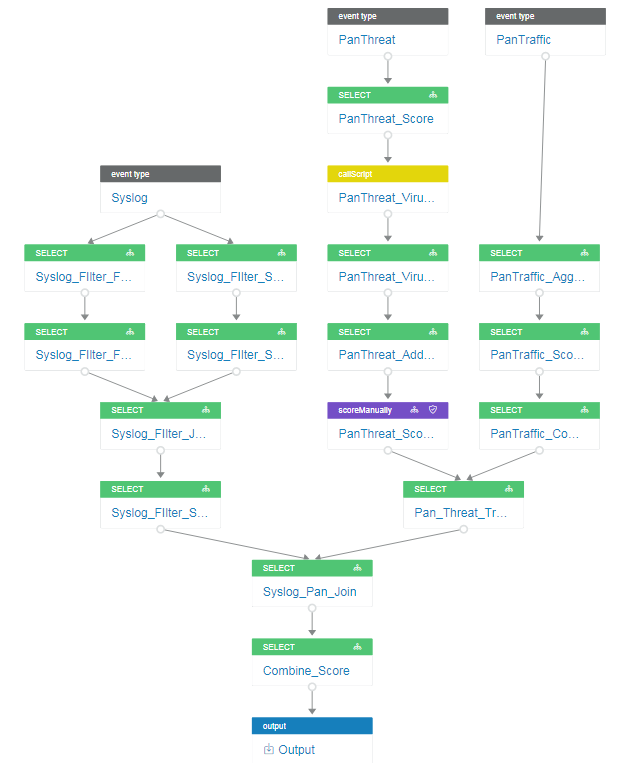
Playbooks can be much more extensive with multiple event types and interrelated actions. The following playbook extends the analysis of the previous example by adding additional event types for traffic and syslog messages for filtering, aggregation, and scoring.
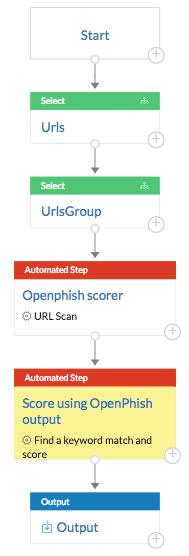
The following playbook includes steps that are shown with red headers. Each step contains a module or integration. A module automates a particular function, and an integration interacts with other systems or tools to bring in external information about threats.
This playbook takes a set of URLs as input and groups them to get a set of unique URLs. It then uses an OpenPhish integration to compare the URLs against known threats. Finally, it uses a module to parse the results and produce a score for each URL.
You're now ready to build a playbook. The easiest way is to use Easy Mode.
Updated over 2 years ago