CrowdStrike
Version: 2.0.0
CrowdStrike Falcon Host uniquely combines an array of powerful methods to provide prevention against the rapidly changing tactics, techniques and procedures (TTPs) used by adversaries to breach organizations - including commodity malware, zero-day malware and even advanced malware-free attacks.
Connect CrowdStrike with LogicHub
- Navigate to Automations > Integrations.
- Search for CrowdStrike.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- API ID: API ID of your CrowdStrike instance.
- API Key: API Key of your CrowdStrike instance.
- After you've entered all the details, click Connect.
Actions for CrowdStrike
Get Detection Details
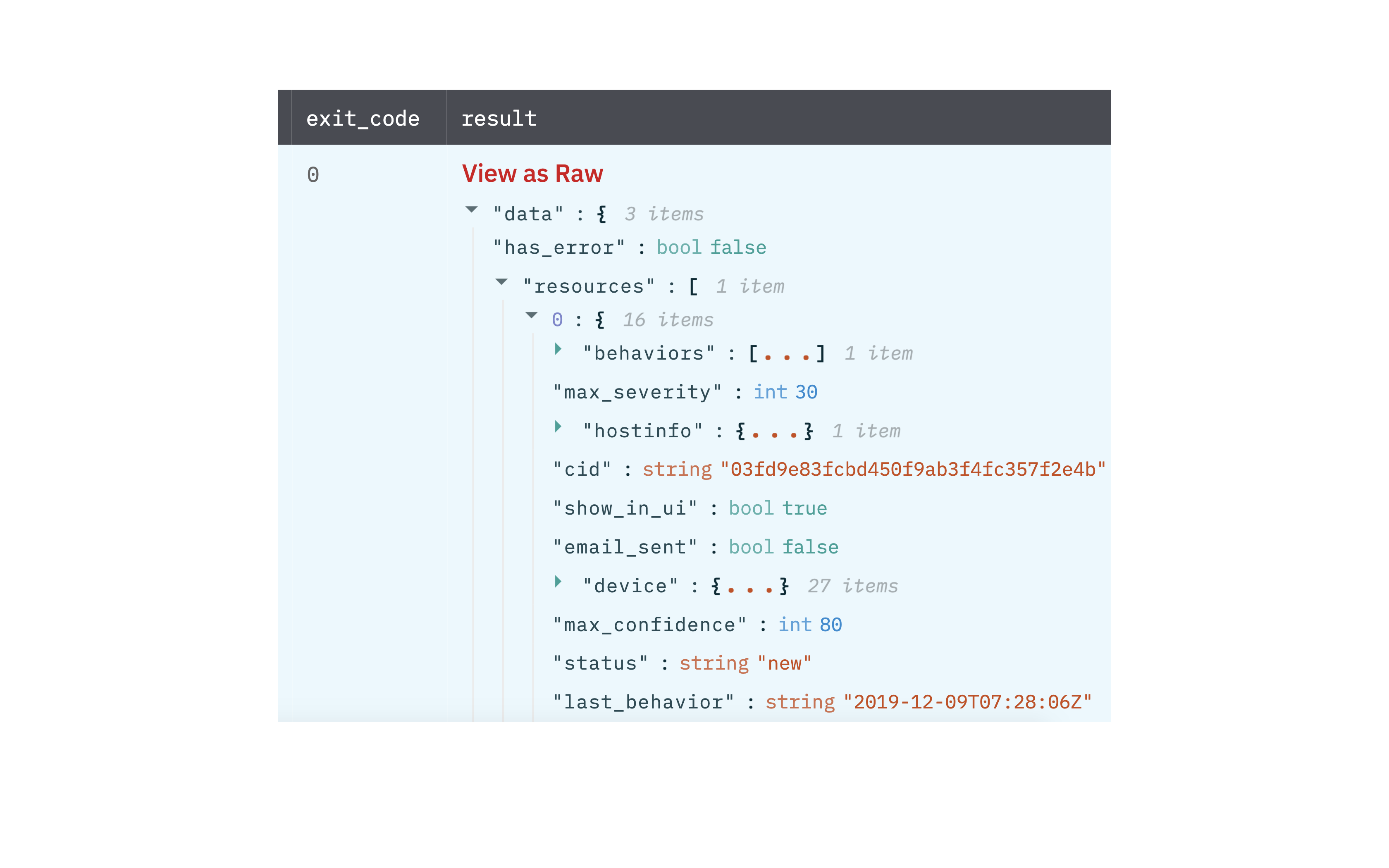
Get detection details action allows you to view details for specific detections given one or more detection IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Detection ID Column Name | Column name from the parent table to lookup value for detection ID. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Detection details
Get Device Details
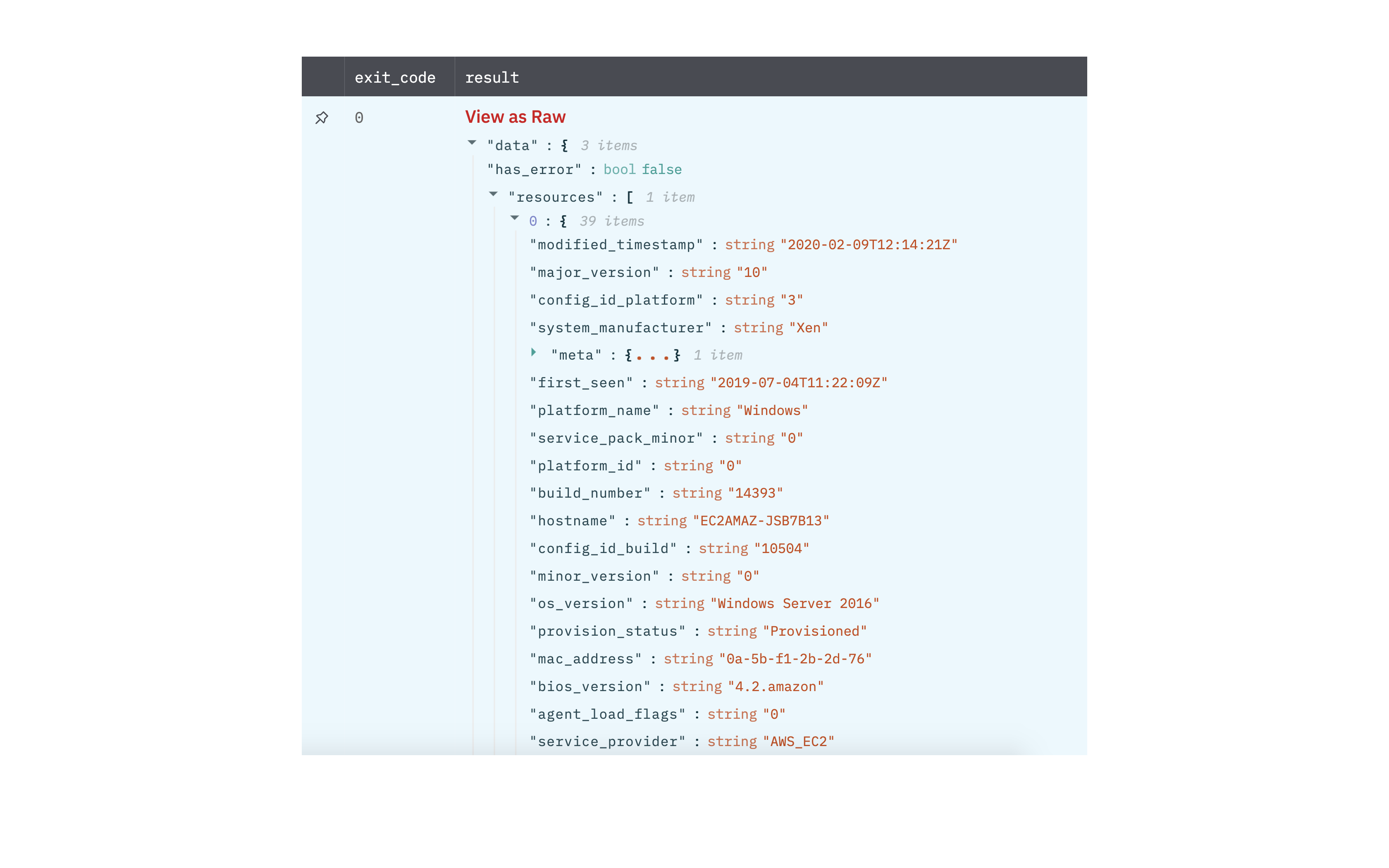
Get device details action allows you to view details for specific devices given one or more device IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Device ID Column Name | Column name from the parent table to lookup value for the device ID. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Device details
Get Process Details
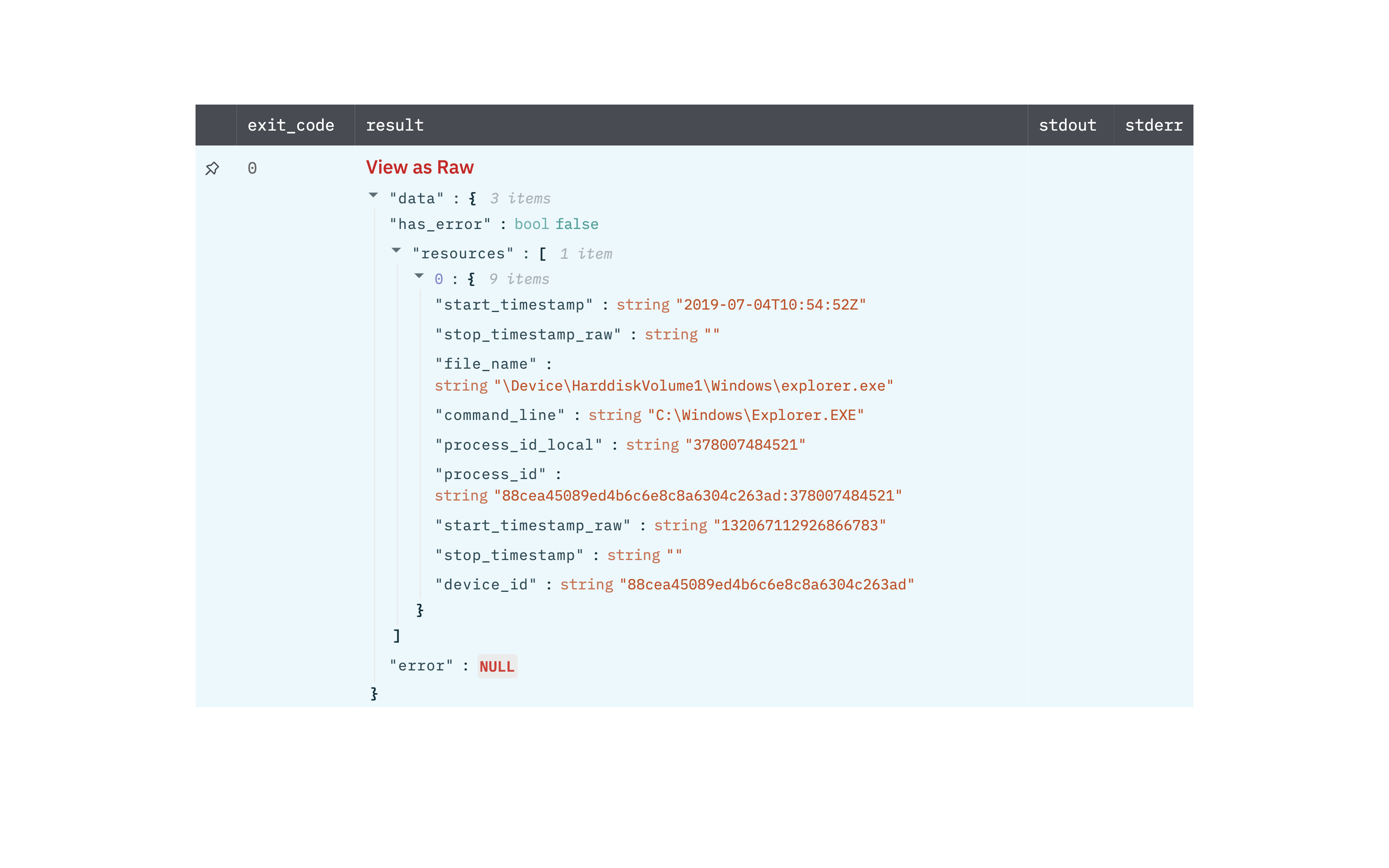
Retrieve the details of a process that is running or that previously ran, given one or more process IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Process ID Column Name | Column name from the parent table to lookup value for process ID. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Process details
Search Devices
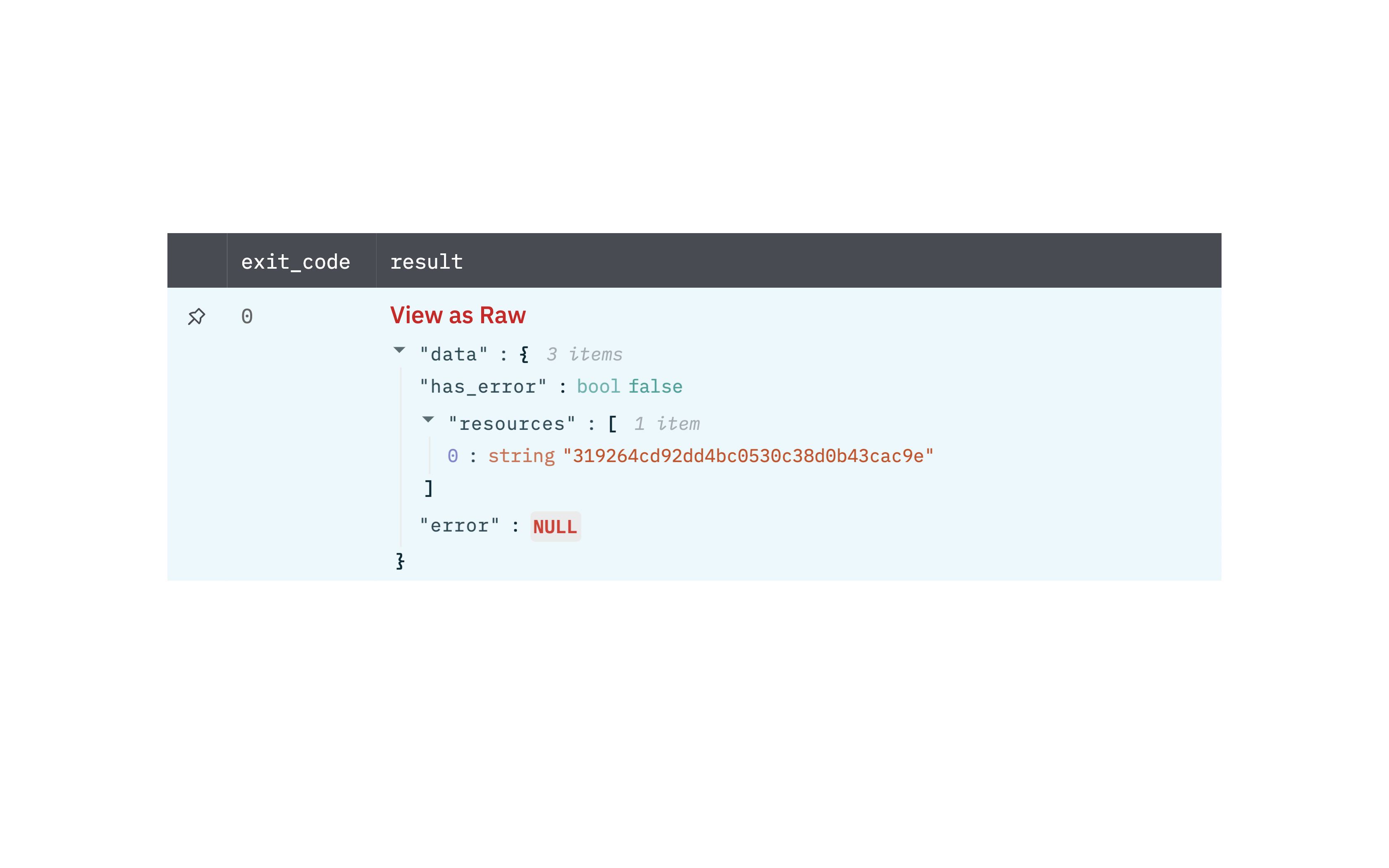
Search for devices based on a filter.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Devices Filter Template Column Name | Jinja2 template for the device filter. Following are a few examples. Find more on falcon API documentation. 1. To find devices with host name hostname: '{{host_column}}' 2. To find devices based on prefix or suffix use wildcard ' ' (supported by few fields) hostname: '{{host_prefix_column}}' 3. To find devices with local IP local_ip: '{{ip_column}}' 4. To find devices which matches both hostname and platform '+' operator is used Example: hostname: '{{host_column}}' + platform_name:'{{platform_column}}' 5. To find devices which matches either hostname or platform name ' , ' operator is used. Example: hostname: '{{host_column}}' , platform_name:'{{platform_column}}' | Required |
| Max Number of Results | Number of results to fetch. (Default is 100 results). | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Device details
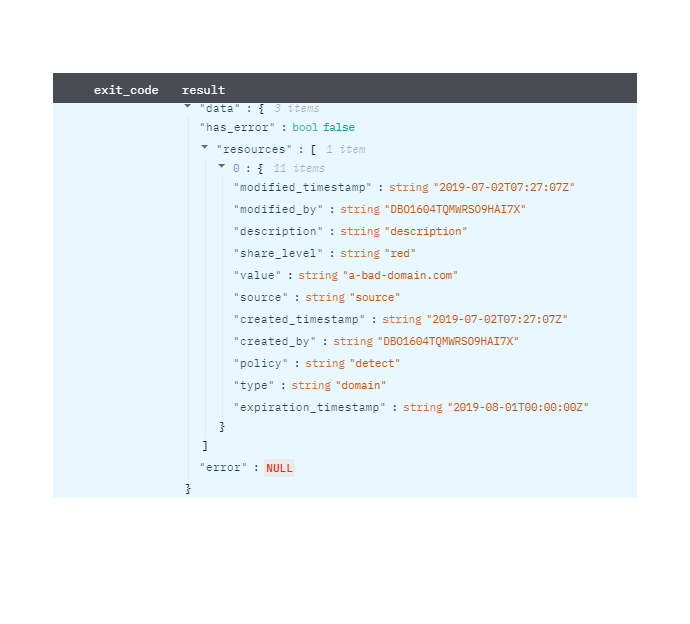
Get IOC Details
Get IOC (Indicators of Compromise) details based on value and type.
Input Field
| Input Name | Description | Required |
|---|---|---|
| IOC Type | Select the value of IOC Type. | Required |
| IOC Value Column Name | Column name from parent table that contains IOC value. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: IOC details
Release Notes
v2.0.0- Updated architecture to support IO via filesystem
Updated over 2 years ago