Integrations
Integrations allow you to exchange data with third-party applications. With the integrations feature, you can set up a connection to a third-party application and then call that connection from your playbook.
To add an integration, click on Automations > Integration on the left navigation. The Automation Library pops-up that lists all the available integrations. To know more about how to add integration, see Add an Integration Connection.
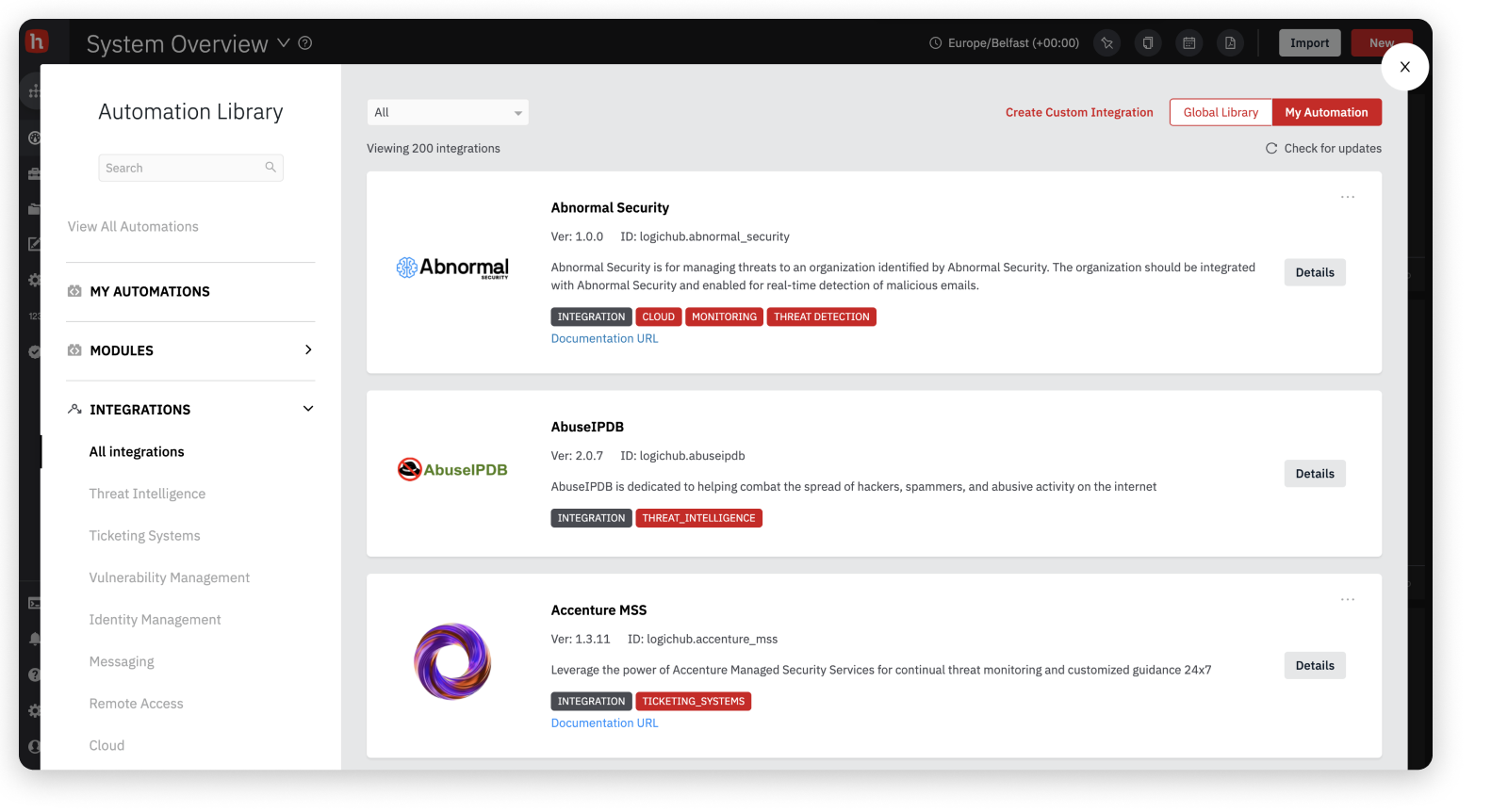
Integration Details
The integrations contains the following details categorized in each tabs:
-
Connections: This tab details the area list all of the connections for the integration, with an alert indicator for any that have errors.
To add a new connection for the integration:- Click + in the connections tab.
- Enter the configuration information, which depends on the selected integration, and click Save.
-
Actions: This tab lists the actions that can be selected when the integration is added to a playbook. Each integration in the respective category contains a set of predefined actions that you may want to add to your playbook based on your needs. To know more, see How to Add an Integration.
-
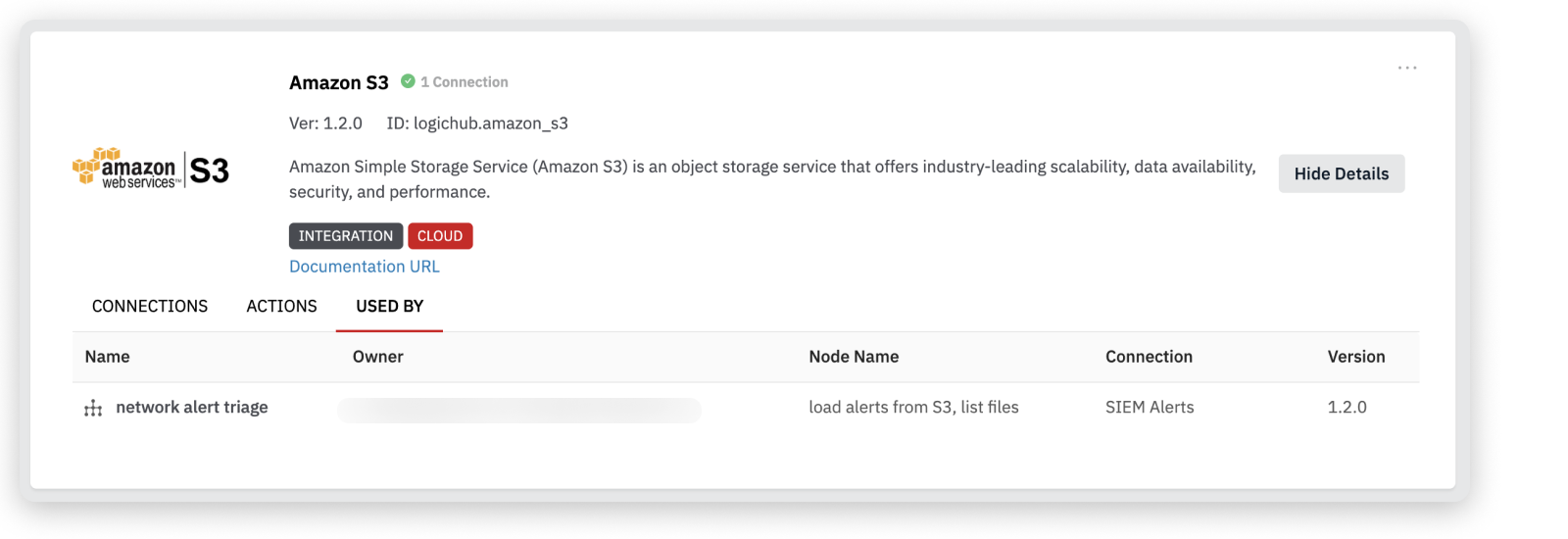
Used By: This tab lists all the playbooks that currently use the selected integration.
All Integrations
LogicHub offers a library of out-of-the-box integrations for your playbooks. To know more about each integration, click on its name.
| Integration | Description |
|---|---|
| Abnormal Security | Abnormal Security is for managing threats to an organization identified by Abnormal Security. The organization should be integrated with Abnormal Security and enabled for real-time detection of malicious emails. |
| Absolute | The Absolute® Platform leverages a cloud-based, highly-available and secure multi-tenant architecture that is available across different regions. It’s comprised of a variety of foundational components that power Absolute product features that are being leveraged by the company’s enterprise customers and ecosystems partners alike. |
| AbuseIPDB | AbuseIPDB is dedicated to helping combat the spread of hackers, spammers, and abusive activity on the internet. |
| Accenture MSS | Leverage the power of Accenture Managed Security Services for continual threat monitoring and customized guidance 24x7 |
| Active Directory | Active Directory is a directory service that Microsoft developed for Windows domain networks. |
| Akamai | Akamai secures content, data, and applications across all your data centers and cloud providers, so you can harness the power of a multi-cloud world while maintaining governance and control. |
| Akamai API Gateway | The Akamai API Gateway governs your API traffic by authenticating, authorizing, and controlling requests from API consumers. |
| Alexa Web Information Service | The Alexa Web Information Service API makes Alexa's vast repository of information about the web traffic and structure of the web available to developers. |
| AlienVault OTX | AlienVault unifies all of your essential security tools in one location and combines them with real-time threat intelligence. |
| AlienVault USM | AlienVault USM is a SaaS security monitoring platform designed to centralize threat detection, incident response, and compliance management of cloud, hybrid cloud, and on-premises environments from a cloud-based console. |
| Amazon AWS | Amazon Web Services (AWS) is a subsidiary of Amazon.com that provides on-demand cloud computing platforms to individuals, companies, and governments, on a paid subscription basis. |
| Amazon EC2 | Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides secure, resizable compute capacity in the cloud. |
| Amazon EC2 (Assumed Role) | Amazon Elastic Compute Cloud (Amazon EC2) is a web service that provides secure, resizable compute capacity in the cloud. |
| Amazon S3 | Amazon Simple Storage Service (Amazon S3) is an object storage service that offers industry leading scalability, data availability, security, and performance. |
| Anomali | Anomali is a Threat Intelligence Platform that enables businesses to integrate security products and leverage threat data to defend against cyber threats. |
| Anomali Match | Anomali Match is a Threat Detection Engine purpose-built to automate and speed time to detection in your environment. Anomali Match correlates twelve months of metadata against active threat intelligence to expose previously unknown threats to your organization. |
| Anyrun | Anyrun is a service that allows cybersecurity specialists to detect, analyze, and monitor cybersecurity threats. It is the interactive online malware analysis sandbox, where the user controls the flow of the analysis. |
| Apache Kafka | Apache Kafka is a stream-processing software platform that aims to provide a unified, high-throughput, low-latency platform for handling real-time data feeds. |
| Apility | Apility.io can be defined as Threat Intelligence SaaS for developers and product companies that want to know in realtime if their existing or potential users have been classified as 'abusers' by one or more of these lists. |
| Apivoid | Apivoid provides JSON APIs useful for cyber threat analysis, threat detection and threat prevention, reducing and automating the manual work of security analysts. |
| Arbor Sightline | Arbor Sightline provides robust capabilities from network-wide capacity planning, to identifying and managing the mitigation of threats to the network. |
| Area 1 Security | Area 1 Security offers Application Programming Interfaces (APIs) to expose our phishing campaign rulesets. These APIs both aid research and provide a set of indicators to block using network security edge devices. |
| ARIN Whois | ARIN Whois is a directory service for accessing registration data contained within ARIN's registration database. |
| ArcSight ESM | ArcSight Enterprise Security Manager sits centrally within an organization, collecting and analyzing events from across systems and security tools. It detects security threats in real time so that analysts respond quickly, and it scales to meet demanding security requirements. |
| Attackforge | AttackForge is used for penetration testing management and reporting platforms. |
| AWS CloudTrail | AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. |
| AWS CloudWatch Logs | CloudWatch Logs enables you to centralize the logs from all of your systems, applications, and AWS services that you use, in a single, highly scalable service. |
| AWS EKS | Amazon Elastic Kubernetes Service (AWS EKS) is a managed service that you can use to run Kubernetes on AWS without needing to install, operate, and maintain your own Kubernetes control plane or nodes. |
| AWS EKS (Assumed Role) | Amazon Elastic Kubernetes Service (AWS EKS) is a managed service that you can use to run Kubernetes on AWS without needing to install, operate, and maintain your own Kubernetes control plane or nodes. |
| AWS IAM | AWS Identity and Access Management (IAM) is a web service for securely controlling access to AWS services. With IAM, you can centrally manage users, security credentials such as access keys, and permissions that control which AWS resources users and applications can access. |
| AWS IAM (Assumed Role) | AWS Identity and Access Management (IAM) is a web service for securely controlling access to AWS services. With IAM, you can centrally manage users, security credentials such as access keys, and permissions that control which AWS resources users and applications can access. |
| Axonius | Axonius is a cybersecurity asset management solutions that offers a comprehensive IT asset inventory and network security policy enforcement. |
| Azure Compute | Whether you are building new applications or deploying existing ones, Azure compute provides the infrastructure you need to run your apps. |
| Azure Monitor | Azure Monitor maximizes the availability and performance of your applications and services by delivering a comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments. |
| Azure Security Center | Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers and provides advanced threat protection across your hybrid workloads in the cloud. |
| Azure Sentinel | Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution. |
| Azure Storage | Azure Blob storage is Microsoft's object storage solution for the cloud. Blob storage is optimized for storing massive amounts of unstructured data. |
| Beyond Trust | Beyond Trust is the worldwide leader in intelligent identity and access security. That protect identities, stop threats, and deliver dynamic access. |
| Bitdefender | Bitdefender provides anti-virus software, internet security software, endpoint security software, and other cyber security products and services. |
| Blameless | Blameless is the end-to-end SRE platform, empowering teams to optimize the reliability of their systems without sacrificing innovation velocity. |
| Box | Box is a platform for Secure Content Management, Workflow, and Collaboration. That focuses on cloud content management and file sharing service for businesses. |
| C1fapp | C1fApp is a threat feed aggregation application, providing a single feed, both Open Source and private. |
| CA Service Desk | CA Service Desk Manager is a cloud-based IT service and support management solution. Primary features include change management, incident management, automation support, self-service, predefined services, and workflows and reporting. |
| Carbon Black Response | Carbon Black Response is a highly scalable, real-time EDR with unparalleled visibility for top security operations centers and incident response teams. |
| Carbon Black Response v2 | Carbon Black Response is a highly scalable, real-time EDR with unparalleled visibility for top security operations centers and incident response teams. V2 version is developed for Carbon Black Response API's latest version. |
| Case Management | An Integration to manage LogicHub Cases. It can create new cases, get all cases, get a specific case's details and update or delete a case. |
| Censys | Censys is a platform that helps information security practitioners discover, monitor, and analyze devices that are accessible from the Internet. |
| CheckPhish AI | CheckPhish uses deep learning, computer vision, and NLP to mimic how a person would look at, understand, and draw a verdict on a suspicious website. |
| Checkpoint Firewall | Checkpoint firewall features centralized management control across all networks and cloud environments, increasing operational efficiency and lowering the complexity of managing your security. |
| ClickSend | ClickSend is a cloud-based service that lets you send and receive SMS, Email, Voice, Fax, and Letters worldwide. |
| Cloudflare | Cloudflare provides content delivery network services, DDoS mitigation, Internet security, and distributed domain name server services. |
| Computer Incident Response Center (CIRCL) | CIRCL is a government-driven initiative designed to gather, review, report, and respond to computer security threats and incidents. |
| Confluence | Confluence is a collaboration tool used to help teams to collaborate and share knowledge efficiently. |
| Cisco AMP | Cisco AMP is an intelligence-powered, integrated, enterprise-class advanced malware analysis and protection solution. |
| Cisco Ironport | The Cisco IronPort Hosted Email Security solution cleans up all inbound mail by using industry leading anti-spam, anti-virus, and other rules. This ensures that the mail traffic that reaches the customer premises is free from email malware. |
| Cisco FirePower | Cisco FirePower delivers an integrated threat defense across the entire attack continuum - before, during, and after an attack. It combines the proven security capabilities of the Cisco ASA Firewall with industry-leading Sourcefire threat and advanced malware protection features in a single device. |
| Cisco Secure Endpoint | Cisco Secure Endpoint offers cloud-delivered next-generation antivirus and advanced endpoint detection and response. |
| Cisco Stealthwatch | Cisco stealthwatch is a network analysis tool built to protect your cloud assets and private network. |
| Cisco Stealthwatch Enterprise | Cisco Stealthwatch Enterprise drastically enhances threat defence by giving detailed network visibility and security analytics. |
| Cisco Talos | IP Reputation center. |
| Cisco ThreatGrid | Threat Grid combines advanced sandboxing with threat intelligence into one unified solution to protect organizations from malware. With a robust, context-rich malware knowledge base, you will understand what malware is doing, or attempting to do, how large a threat it poses, and how to defend against it. |
| Cisco Umbrella | Cisco Umbrella is a cloud security platform that provides the first line of defense against threats on the internet wherever users go. By learning from internet activity patterns, Umbrella automatically uncovers current and emerging threats. |
| CMDBuild | CMDBuild is an open source web enterprise environment to configure custom applications for asset management. |
| Cortex XDR | Cortex XDR stitches together data from the endpoint, network, and cloud in a robust data lake. Applying advanced machine learning and analytics, it identifies threats and benign events with superior accuracy and gives analysts contextualized information, simplifying and accelerating investigations. This integration supports 'public_api/v1' endpoint. |
| CrowdStrike | CrowdStrike Falcon Host uniquely combines an array of powerful methods to provide prevention against the rapidly changing tactics, techniques and procedures (TTPs) used by adversaries to breach organizations - including commodity malware, zero-day malware and even advanced malware-free attacks. |
| CrowdStrike Falcon Host (OAuth Based) | CrowdStrike Falcon Host uniquely combines an array of powerful methods to provide prevention against the rapidly changing tactics, techniques and procedures (TTPs) used by adversaries to breach organizations - including commodity malware, zero-day malware and even advanced malware-free attacks. |
| CRXcavator | CRXcavator is an automated Chrome extension security assessment tool that assigns risk scores to extensions based on an objective set of criteria. |
| Cuckoo | Cuckoo is an open-source automated malware analysis system. It's used to automatically run and analyze files and collect comprehensive analysis results that outline what the malware does while running inside an isolated operating system. |
| Cyberark EPM | CyberArk Endpoint Privilege Manager provides holistic endpoint protection to secure all endpoints and enforce least privilege without disrupting business. |
| Cybereason | The Cybereason Response Interface enables security teams to quickly respond to detected threats by killing processes and isolating machines. |
| Cylance | Cylance is revolutionizing cybersecurity with AI based solutions that predict and prevent execution of advanced threats and malware at the endpoint. |
| Darktrace | Darktrace's Enterprise Immune System uses proprietary machine learning and AI algorithms to build a so-called "pattern of life" for every network, device, and user within an organization. It then employs correlation techniques to classify and cross-reference these models, establishing a highly accurate understanding of 'normal activity' within that particular environment. |
| Demisto | Demisto is a leading Security Orchestration, Automation, and Response (SOAR) platform that helps security teams accelerate incident response, standardize and scale processes. |
| Datadog | Datadog is the essential monitoring and security platform for cloud applications. It brings together end-to-end traces, metrics, and logs to make your applications, infrastructure, and third-party services entirely observable. These capabilities help businesses secure their systems, avoid downtime, and ensure customers are getting the best user experience. |
| Devo | Devo delivers real-time operational and business value from analytics on streaming and historical data to operations, IT, security and business teams. |
| DNS | Delivers various actions related to DNS. |
| DomainTools | DomainTools is a leading provider of Whois and other DNS profile data for threat intelligence enrichment. It is a part of the Datacenter Group (DCL Group SA). DomainTools data helps security analysts investigate malicious activity on their networks. Using IOCs (Indicators of Compromise), including domains and IPs, analysts can build a map of connected infrastructure. Those connections inform risk assessments, help profile attackers, guide online fraud investigations, and map cyber activity to attacker infrastructure. |
| Dropbox | Dropbox is a file hosting service, that offers cloud storage, file synchronization, personal cloud, and client software. |
| Duo Security | Duo security is a user-centric access security platform with two-factor authentication to protect access to sensitive data for all users, devices, and applications. |
| Elasticsearch | Elasticsearch is a search engine based on Lucene. It provides a distributed, multitenant-capable full-text search engine with an HTTP web interface and schema-free JSON documents. |
| Emerging Threats | Emerging Threats delivers the most timely and accurate threat intelligence. Our fully verified intel provides deeper context and integrates seamlessly with your security tools to enhance your decision-making. |
| Exchange (EWS) | Microsoft Exchange Server is a mail server and calendaring server developed by Microsoft. This integration relies on EWS being enabled for the server. |
| Exchange (Quarantine Messages) | Microsoft Exchange Server is a mail server and calendaring server developed by Microsoft. This integration relies on EWS being enabled for the server. |
| Exchange Online (Graph API) | Microsoft Exchange Server is a mail server and calendaring server developed by Microsoft. This integration relies on EWS being enabled for the server. |
| Expel | Expel is a SOC-as-a-service platform that provides security monitoring and response for cloud, hybrid, and on-premises environments. |
| Falcon Sandbox | Falcon Sandbox performs deep analysis of evasive and unknown threats, enriches the results with threat intelligence and delivers actionable indicators of compromise (IOCs), enabling your security team to better understand sophisticated malware attacks and strengthen their defenses. |
| Farsight Security DNSDB | Farsight Security's DNSDB is a Passive DNS historical database that provides a unique, fact-based, multifaceted view of the configuration of the global Internet infrastructure. |
| Fidelis | Fidelis Elevate is a complete network and endpoint automated threat detection and response platform that improves SOC effectiveness and efficiency. It delivers comprehensive visibility, alert validation, and increased speed to a response by applying industry-leading threat intelligence (Fidelis Insight) to real-time and historical data. |
| File Tools | Manipulating files through the file integrations API |
| FireEye ETP | FireEye Email Threat Prevention (ETP Cloud) is a cloud-based platform that protects against advanced email attacks. |
| FireEye Helix | FireEye Helix is a security operations platform that makes it simple to deliver advanced security to any organization. It surfaces unseen threats and empowers expert decisions with frontline intelligence to take back control of your defenses and capture the untapped potential of your security investments. |
| Flashpoint | Flashpoint is the globally trusted leader in risk intelligence for organizations that demand the fastest, most comprehensive coverage of threatening activity on the internet |
| Flashpoint Ignite | Flashpoint Ignite is a threat intelligence platform that provides security teams with data, intelligence, and analytics to help them identify and respond to cyber threats, vulnerabilities, and physical security risks. |
| FortiSIEM | FortiSIEM provides organizations with a comprehensive, holistic and scalable solution, from IoT to the Cloud, with patented analytics that are actionable to tightly manage network security, performance and compliance standards, all delivered through a single pane of glass view of the organization. |
| Freshservice | Freshservice is a cloud based IT service management software for service desk with an automation tool to manage incidents, assets and other facilities. |
| GitHub | GitHub provides an action to get the list of organization-public activities performed by a user. |
| Google Bigtable | Google Bigtable is a distributed, column-oriented data store created by Google Inc. to handle very large amounts of structured data associated with the company's Internet search and Web services operations. Bigtable was designed to support applications requiring massive scalability; from its first iteration, the technology was intended to be used with petabytes of data. The database was designed to be deployed on clustered systems and uses a simple data model that Google has described as "a sparse, distributed, persistent multidimensional sorted map." Data is assembled in order by row key, and indexing of the map is arranged according to row, column keys and timestamps. Compression algorithms help achieve high capacity. |
| Google Calendar | Google Calendar is a time-management and scheduling calendar service developed by Google. |
| Google Cloud Storage | Google Cloud Storage is a RESTful online file storage web service for storing and accessing data on Google Cloud Platform infrastructure. |
| Google Compute | Google Cloud Engine (GCE) is an Infrastructure as a Service (IaaS) offering that allows clients to run workloads on Google's physical hardware. Google Compute Engine provides a scalable number of virtual machines (VMs) to serve as large compute clusters for that purpose. |
| Google Gemini | Gemini can enhance SOAR by providing natural language understanding and generation capabilities for automating incident response, threat hunting, and report generation, significantly improving efficiency and accuracy. |
| Google Safebrowsing | Safe Browsing is a Google service that lets client applications check URLs against Google's constantly updated lists of unsafe web resources. |
| Google Sheets | Google Sheets is a spreadsheet program included as part of the free, web-based Google Docs Editors suite offered by Google. |
| Google Stackdriver | Google Stackdriver is a monitoring service that provides IT teams with performance data about applications and virtual machines running on the Google Cloud Platform and Amazon Web Services public cloud. Google Stackdriver performs monitoring, logging and diagnostics to help businesses ensure optimal performance and availability. The service gathers performance metrics and metadata from multiple cloud accounts and allows IT teams to view that data through custom dashboard, charts and reports. |
| GRR Authentication Information | GRR Rapid Response is an incident response framework focused on remote live forensics. |
| Have I Been Pwned? | Have I Been Pwned? is a website that allows internet users to check if their personal data has been compromised by data breaches. |
| HCL BigFix | HCL BigFix provides system administrators with remote control, patch management, software distribution, operating system deployment, network access protection and hardware and software inventory functionality. |
| Humio | Humio is a live observability platform that enables data aggregation, exploration, reporting and analysis from a range of sources. The purpose-built logging tool features innovative data storage and in-memory search/query engine technologies. |
| Hybrid Analysis | Hybrid Analysis is a free malware analysis service for the community. |
| IBM OMNIbus via postemsg | Use IBM's "postemsg" binary to post an event to OMNIbus using non-Tivoli communication. |
| IBM QRadar | IBM® QRadar® Security Information and Event Management (SIEM) helps security teams accurately detect and prioritize threats across the enterprise, and it provides intelligent insights that enable teams to respond quickly to reduce the impact of incidents. |
| IBM X-Force | IBM X-Force Exchange is a cloud-based threat intelligence sharing platform enabling users to rapidly research the latest security threats. |
| IMAP | Internet Message Access Protocol is a standard protocol used by e-mail clients to retrieve messages from a mail server over a TCP/IP connection. IMAP is defined by RFC 3501. |
| Intezer | Intezer is a platform built to analyze and investigate every alert like an experienced security analyst and reverse engineer. |
| IP Quality Score | The IPQualityScore fraud detection API suite features a variety of different risk analysis APIs designed to Proactively Prevent Fraud™ with industry leading accuracy to identify fraudulent users, suspicious payments, and abusive behavior. |
| IPStack | IPStack offers one of the leading IP to geolocation APIs and global IP database services worldwide. |
| JAMF | With Jamf, IT and security teams are able to confidently manage and protect the devices, data and applications used by their end-users without getting in the way of the intended Apple experience. |
| JDBC | Connects to database using JDBC. Supports connection to Postgres via postgreSQL-42.5.3. |
| Jira | Jira provides bug tracking, issue tracking, and project management functions. |
| JoeSecurity Sandbox | Joe Sandbox is a multi technology platform which uses instrumentation, simulation, hardware virtualization, hybrid and graph - static and dynamic analysis. Rather than focus on one technology Joe Sandbox combines the best parts of multiple techniques. This enables deep analysis, excellent detection and big evasion resistance. |
| JumpCloud | JumpCloud's revolutionary directory unifies device and identity on Windows, Mac, and Linux with cloud based SSO, MDM, MFA, PAM, and more. |
| KnowBe4 | KnowBe4 is the world’s largest integrated platform for security awareness training combined with simulated phishing attacks. |
| Lastline | Lastline offers network-based security breach detection and other security services. |
| Logentries | Logentries is an easy-to-use, self-hosted log management and analytics service for teams of all sizes. |
| LogRhythm | LogRhythm is an enterprise-class platform that seamlessly combines SIEM, log management, file integrity monitoring and machine analytics with host and network forensics in a unified Security Intelligence Platform. |
| MalShare | The MalShare Project is a collaborative effort to create a community driven public malware repository that works to build additional tools to benefit the security community at large. |
| Malware Domain List | Malware Domain List provides a public of domains that host malware. |
| Mandiant | Mandiant Solutions brings together the world’s leading threat intelligence and frontline expertise with continuous security validation to arm organizations with the tools needed to increase security effectiveness and reduce business risk. |
| MaxMind | MaxMind is an industry-leading provider of IP intelligence and online fraud detection tools. |
| McAfee ATD | McAfee Advanced Threat Defense enhances protection from the network edge to the endpoint and enables investigation. |
| McAfee ePO | McAfee ePolicy Orchestrator provides a web application programming interface (API) that allows you to script and automate common management activities. |
| McAfee ESM | McAfee Enterprise Security Manager is a security information and event management (SIEM) solution that delivers actionable intelligence and integrations to prioritize, investigate, and respond to threats. |
| Metadefender | Metadefender is a powerful and flexible security solution for ISVs, IT admins, and malware researchers, providing simultaneous access to data sanitization (CDR), vulnerability assessment, multiple anti-malware engines, heuristics, and additional threat protection technologies residing on a single system. |
| Micro Focus ArcSight Logger | ArcSight Logger delivers a universal log management solution that unifies searching, reporting, alerting, and analysis across any type of enterprise machine data. |
| Microsoft 365 Defender | Microsoft 365 Defender delivers XDR capabilities for identities, endpoints, cloud apps, email and documents. |
| Microsoft Azure NSG Flow Logs | NSG flow logs are stored in a storage account in block blobs. Block blobs are made up of smaller blocks. Each log is a separate block blob that is generated every hour. New logs are generated every hour, the logs are updated with new entries every few minutes with the latest data. |
| Microsoft Cloud App Security | Microsoft Cloud App Security is a Cloud Access Security Broker (CASB) that operates on multiple clouds. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all your cloud services. |
| Microsoft Defender for Endpoint | Microsoft Defender for Endpoint is a platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. |
| Microsoft Graph | Microsoft Graph is the gateway to data and intelligence in Microsoft 365. Microsoft Graph provides a unified programmability model that you can use to take advantage of the tremendous amount of data in Office 365, Enterprise Mobility + Security, and Windows 10. |
| Microsoft Identity And Access (Graph) | Microsoft Identity And Access (Graph) is the gateway to access Azure Active Directory (Azure AD) resources to enable scenarios like managing administrator (directory) roles, inviting external users to an organization. |
| Microsoft SQL Server | Microsoft SQL Server (MSSQL for short) is a relational database management system developed by Microsoft. |
| Microsoft Teams | Microsoft Teams is a unified communication and collaboration platform that combines persistent workplace chat, video meetings, file storage (including collaboration on files), and application integration. |
| Mimecast | Mimecast is an cloud-based email management service for security, archiving, and continuity services to protect business mail. |
| Minerva Labs | Minerva Labs is cyber security company that offers a unique low footprint endpoint prevention platform. |
| MISP | A threat intelligence platform for gathering, sharing, storing and correlating Indicators of Compromise of targeted attacks, threat intelligence, financial fraud information, vulnerability information or even counter-terrorism information. |
| MistNet | MistNet provides a machine learning (ML)-driven network threat detection and response solution and a built-in MITRE ATT&CK™ Engine that eliminates blind spots and monitors your organization’s network in real time. |
| MongoDB | MongoDB is a free and open-source cross-platform document-oriented database. |
| MxToolbox | MxToolbox is an online MX record and all-inclusive DNS tool. |
| Myip.ms | Myip.ms is the #1 World Live Whois IP Source. |
| MySQL | MySQL is the world’s most popular open source database. With its proven performance, reliability, and ease-of-use, MySQL has become the leading database choice for web-based applications. |
| Naverisk | Automating IT Services. Naverisk has been helping MSPs and IT Pros deliver first-class IT services. |
| Nessus | Nessus is a remote security scanning tool, which scans a computer and raises an alert if it discovers any vulnerabilities that malicious hackers could use to gain access to any computer you have connected to a network. It does this by running over 1200 checks on a given computer, testing to see if any of these attacks could be used to break into the computer or otherwise harm it. |
| NetBIOS | NetBIOS is an OSI Session Layer 5 Protocol and a service that allows applications on computers to communicate with one another over a local area network (LAN). It is a non-routable Protocol and NetBIOS stands for Network Basic Input/Output System. |
| Netskope | Netskope, a global cybersecurity leader, is redefining cloud, data, and network security to help organizations apply zero trust principles to protect data. |
| Netwitness | NetWitness is an Evolved SIEM and Open XDR platform that accelerates threat detection and response. |
| Neutrino | Neutrino API launched back in 2013 on a mission to fix those inherently complex problems which crop up on almost all software projects. The Neutrino API platform provides a highly available, performant global network that lets developers focus on their product and not on building and maintaining complex in-house tools not relevant to their core business. |
| Nexpose | Nexpose, Rapid7's on-premise option for vulnerability management software, monitors exposures in real-time and adapts to new threats with fresh data, ensuring you can always act at the moment of impact. |
| NinjaRMM | NinjaRMM provides intuitive endpoint management software to managed service providers (MSPs) and IT professionals. |
| Nmap | Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection. |
| Obsidian | Obsidian is the cloud detection and response solution that delivers unified visibility of users, privileges and activity in SaaS, allowing you to detect and investigate breaches, uncover insider threats, and secure SaaS apps without affecting productivity. |
| Okta | Okta is an integrated identity and mobility management service. Built from the ground up in the cloud, Okta securely and simply connects people to their applications from any device, anywhere, at anytime. Okta integrates with existing directories and identity systems, as well as thousands of on-premises, cloud and mobile applications, and runs on a secure, reliable and extensively audited cloud-based platform. |
| OpenPhish | OpenPhish identifies phishing sites and performs intelligence analysis in real time without human intervention and without using any external resources, such as blacklists. |
| Opensearch | OpenSearch is a scalable, flexible, and extensible open-source software suite for search, analytics, and observability applications licensed under Apache 2.0. |
| OpsGenie | Opsgenie ensures you will never miss a critical alert. With deep integrations into monitoring, ticketing, and chat tools, Opsgenie groups alerts, filters out the noise, and notifies you using multiple channels, providing the necessary information for your team to immediately begin resolution. |
| Oracle | Oracle Database is a proprietary multi-model database management system produced and marketed by Oracle Corporation. It is a database commonly used for running online transaction processing, data warehousing and mixed database workloads. |
| OTRS | OTRS is a modern, flexible ticket and process management system. |
| PagerDuty | PagerDuty is an operations performance platform delivering visibility and actionable intelligence across the entire incident lifecycle. |
| Palo Alto Panorama | Panorama is the centralized management system for the Palo Alto Networks family of next-generation firewalls. It provides a single location from which you can oversee all applications, users, and content traversing your network, and then use this knowledge to create policies that protect and control the network. |
| RiskIQ PassiveTotal | RiskIQ PassiveTotal expedites investigations by connecting internal activity, event, and incident indicator of compromise (IOC) artifacts to what is happening outside the firewall-external threats, attackers, and their related infrastructure. |
| Perforce | Perforce Software provides enterprise-scale development tools. This includes version control, application lifecycle management, agile planning, and static analysis. |
| Phish.AI | Next-Generation Anti-Phishing Platform Powered by AI & Computer. |
| PhishTank | Analyze suspicious files and URLs to detect types of malware including viruses, worms, and trojans. |
| Postgres | PostgreSQL is a powerful, open source object-relational database system that uses and extends the SQL language combined with many features that safely store and scale the most complicated data workloads. |
| Power BI | It is a collection of software services, apps, and connectors that work together to turn your unrelated sources of data into coherent, visually immersive, and interactive insights. |
| Powershell | Windows PowerShell is a Windows command-line shell designed especially for system administrators. |
| Proofpoint TAP | Proofpoint TAP (Targeted Attack Protection) detects and prevents threats in email. |
| Protectwise | Protectwise provides Cloud-Powered Network Detection & Response (NDR). |
| Qualys SSL | Verify the reputation of a URL's SSL certificates. |
| Qualys Vulnerability Management | Qualys VM is a cloud-based service that gives you immediate, global visibility into where your IT systems might be vulnerable to the latest Internet threats and how to protect them. It helps you to continuously identify threats and monitor unexpected changes in your network before they turn into breaches. |
| Randori | Randori recon provides a continuous view of your external perimeter to reduce the risks of shadow IT, misconfigurations, and process failures. |
| Rapid7 Insight VM | Rapid7 InsightVM is a data-rich resource that can amplify the other solutions in your tech stack, from SIEMs and firewalls to ticketing systems. |
| Recorded Future | Recorded Future is the world's largest intelligence company with complete coverage across adversaries, infrastructure, and targets. |
| Recorded Future Triage | Recorded Future Triage is a state-of-the–art malware analysis sandbox, with all the features you need. High-volume sample submission in a customizable environment with detections and configuration extraction for many malware families. |
| ReversingLabs TitaniumCore A1000 | The A1000 Malware Analysis Platform supports advanced hunting and investigations through the TitaniumCore high-speed automated static analysis engine. It is integrated with file reputation services to provide in-depth rich context and threat classification on over 8 billion files and across all file types. |
| ReversingLabs TitaniumCloud | ReversingLabs TitaniumCloud Reputation Services are powerful threat intelligence solutions with up-to-date, threat classification and rich context on over 8 billion goodware and malware files. |
| RSA Archer | RSA Archer GRC Platform is a software that supports business-level management of governance, risk management, and compliance (GRC). The Platform allows users to adapt solutions to their requirements, build new applications, and integrate with external systems without touching a single line of code. |
| Sailpoint | The SailPoint Identity Security Cloud Platform is purpose-built for today’s enterprise demands, delivering an intelligent, autonomous identity foundation that securely fuels your business. |
| Salesforce | Salesforce.com, Inc. is an American cloud computing company headquartered in San Francisco, California. Though its revenue comes from a customer relationship management (CRM) product, Salesforce also sells commercial applications of social networking through acquisition and internal development. |
| SANS Blacklist | SANS Blacklist is a service that utilizes a radically different approach to blacklist formulation called Highly Predictive Blacklisting. Each DShield contributor can now access a unique HPB that reflects the most probable set of source addresses that will connect to that contributor's network over a prediction window that may last several days into the future. |
| SAP Gigya | Gigya offers a customer identity management platform for managing profiles, preference, opt-in and consent settings. |
| Screenshot Machine | Screenshot Machine is a cloud service that allows capturing website images. |
| Securonix SNYPR | SNYPR is a security analytics platform that transforms Big Data into actionable security intelligence. It delivers the proven power of Securonix analytics with the speed, scale, and affordable, long-term storage of Hadoop in a single, out-of-the box solution. |
| SentinelOne | Cyber security that prevents threats at faster speed, greater scale, and higher accuracy than humanly possible. |
| ServiceNow | Achieve end-to-end transformation for your IT services and infrastructure through a single cloud-based platform. ServiceNow IT Service Management (ITSM) software lets you consolidate fragmented tools and legacy systems while automating service management processes. |
| ServiceNow - Basic Auth | Achieve end-to-end transformation for your IT services and infrastructure through a single cloud-based platform. ServiceNow IT Service Management (ITSM) software lets you consolidate fragmented tools and legacy systems while automating service management processes. |
| Sharepoint | Sharepoint empowers teamwork with dynamic and productive team sites for every project team, department, and division. Share files, data, news, and resources. Customize your site to streamline your team's work. Collaborate effortlessly and securely with team members inside and outside your organization, across PCs, Macs, and mobile devices. |
| Shodan | Shodan lets you search for devices that are connected to the Internet. |
| Simulate File | Injects a dummy file to help testing / developing file-based integrations. |
| Slack | Slack is a cloud-based set of proprietary team collaboration tools and services. |
| Slack Web API | Slack is a cloud-based set of proprietary team collaboration tools and services. |
| Smartsheet | Smartsheet is a software as a service offering for collaboration and work management. Smartsheet used to assign tasks, track project progress, manage calendars, share documents, and manage other work, using a tabular user interface. |
| SMB Actions | Server Message Block (SMB) is a network communication protocol for providing shared access to files, printers, and serial ports between nodes on a network. |
| Smokescreen | Smokescreen's IllusionBLACK deception platform detects cyber attacks like reconnaissance, spear phishing, lateral movement, stolen credentials and data theft. |
| SMTP | Simple Mail Transfer Protocol (SMTP) is a standard communication protocol for sending email messages on business networks and the Internet. |
| Snowflake | One platform that power the data cloud. Execute your most critical workloads on top of Snowflake's multi-cluster shared data architecture in a fully managed way. |
| Solarwinds Orion | The SolarWinds Orion Platform is a powerful, scalable infrastructure monitoring and management platform designed to simplify IT administration for on-premises, hybrid, and software as a service (SaaS) environments in a single pane of glass. |
| Splunk | Turn Machine Data Into Answers. Splunk delivers real-time answers and business value from machine data so you can make better decisions. |
| SpyCloud | SpyCloud recaptures data from the criminal underground to illuminate risk you didn’t even know you had across your enterprise, vendors, and customers — so your team can take immediate action. |
| SSH | SSH lets you run a command on a remote host. |
| Sumo Logic | Sumo Logic is a platform for monitoring, analyzing, troubleshooting, and visualizing data from your application and network environment. |
| Symantec Data Loss and Prevention (DLP) | With Symantec Data Loss Prevention, you can discover, monitor and protect sensitive data wherever it's used - in the office, on the road, or in the cloud. It gives you complete visibility and control across the broadest range of data loss channels: cloud apps, endpoints, data repositories, and email and web communications. |
| Symantec Endpoint Detection and Response (EDR) | Symantec Endpoint Security (SES) Complete delivers comprehensive protection for all your traditional and mobile devices across the entire attack chain. |
| Syslog | Send events to remote syslog server. |
| TAXII | TAXII is an application layer protocol for the communication of cyber threat information in a simple and scalable manner. This specification defines the TAXII RESTful API and its resources along with the requirements for TAXII Client and Server implementations. |
| TCell | tCell makes web application security easy for companies using Agile, DevOps, Cloud, and Microservices by enabling web apps to protect itself. |
| Telegram | Telegram is a free and open source, cross-platform, cloud-based instant messaging software. The service also provides end-to-end encrypted video calling. |
| Tenable | Managed on-premises and powered by Nessus technology, the Tenable.sc suite of products provides the a comprehensive vulnerability coverage with real-time continuous assessment of a network. It’s a complete end-to-end vulnerability management solution. |
| TheHive | TheHive is a scalable, open source and free security incident response platform. |
| Threatminer | An open source search engine for fast threat intelligence research & pivoting with context. |
| Trend Micro Cloud Conformity | Trend Micro Cloud Conformity provides continuous security, compliance, and governance for your cloud infrastructure. |
| Trend Micro Workload Security | Trend Micro workload security protects endpoints, servers, and cloud workloads through unified visibility, management, and role-based access control. |
| TruSTAR | TruSTAR is an intelligence management platform that helps enterprises easily enrich and operationalize their security data. The platform uses Enclave architecture to fuse and correlate intelligence sources, helping analysts speed investigations and simplify workflows. |
| Twilio | Twilio allows software developers to programmatically make and receive phone calls and send and receive text messages using its web service APIs. |
| Unshorten.me | Unshorten.me API provides an easy method to unshorten a wide range of shortened URLs. |
| Urlscan_IO | Urlscan.io is a service which analyzes websites and the resources they request. Much like the Inspector of browser, urlscan.io will let you take a look at the individual resources that are requested when a site is loaded. |
| Utilities | Bucket for miscellaneous utility integrations. |
| Virus Total | Virustotal can be used to analyze suspicious files and URLs to detect types of malware including viruses, worms, and trojans. |
| VMRay | VMRay Threat Identifier (VTI) identifies and flags malicious behavior in an uploaded file, generating an overall severity score of malicious behavior. |
| VMWare | VMware Workspace ONE is an intelligence-driven digital workspace platform that enables you to simply and securely deliver and manage any app on any device, anywhere. |
| Web API | Web API integration allows you to execute any Web API and retrieve results. |
| Webroot BrightCloud | The Webroot BrightCloud Web Classification and Web Reputation Services provide the most effective way to block access to unwanted content and protect users against web-based threats. |
| WildFire | Palo Alto WildFire cloud-based threat analysis service is the industry's most advanced analysis and prevention engine for highly evasive zero-day exploits and malware. |
| xMatters | xMatters helps identify, prevent, and resolve IT issues before they impact customers whether it's a simple bug fix or a complex major incident. |
| YETI | Yeti is all about organizing observables, indicators of compromise, TTPs, and knowledge on threat actors in a single, unified repository. |
| Zendesk | Zendesk provides customer service software featuring an email ticketing system for a better customer experience. |
| ZeroFox | ZeroFox provides cloud-based software as a service for organizations to detect risks found on social media and digital channels, such as phishing, malware, scams, impersonator accounts, piracy, counterfeit and more. |
| Zoom | Zoom provides video telephony and online chat services through a cloud-based peer-to-peer software platform and is used for teleconferencing, telecommuting, distance education, and social relations. |
| Zscaler | Zscaler is a global cloud-based information security company that provides Internet security, web security, firewalls, sandboxing, SSL inspection, antivirus, vulnerability management and granular control of user activity in cloud computing, mobile and Internet of Things environments. Zscaler provides a cloud-based approach to security as a service. |
| Zscaler ZPA | The Zscaler Private Access (ZPA) service enables organizations to provide access to internal applications and services while ensuring the security of their networks. ZPA is an easier-to-deploy, more cost-effective, and more secure alternative to VPNs. Unlike VPNs, which require users to connect to your network to access your enterprise applications, ZPA allows you to give users policy-based secure access only to the internal apps they need to get their work done. With ZPA, application access does not require network access. |
| Zenduty | Zenduty is a cutting edge platform for incident management. With high level automation, Zenduty enables faster and better incident resolution keeping developers first. |
Updated 9 months ago