Cisco ThreatGrid
Version: 2.0.0
Threat Grid combines advanced sandboxing with threat intelligence into one unified solution to protect organizations from malware. With a robust, context-rich malware knowledge base, you will understand what malware is doing, or attempting to do, how large a threat it poses, and how to defend against it.
Connect Cisco ThreatGrid with LogicHub
- Navigate to Automations > Integrations.
- Search for Cisco ThreatGrid.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- API Key: API Key for Cisco ThreatGrid.
- URL (Optional): URL to your Cisco ThreatGrid instance. Default is https://panacea.threatgrid.com.
- After you've entered all the details, click Connect.
Actions for Syslog
File Analysis
Submits a file to Threat Grid for analysis and waits for completion. Completion of analysis may take time, so please use appropriate timeout and multi-threading options.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| File ID | Column name that contains LogicHub file id to be submitted for analysis. | Required |
| File Name | Column name that contains file name to be submitted. The filename should be with an extension. Example: myfile.csv or test.exe. | Required |
| VM Name | Name of the VM to use to analyze. Example: win7-x64 , Windows 7 64-bit. By default, ThreatGrid will select the best VM based on the properties of the submitted sample (file). This supports Jinja template input. | Optional |
| Private | Select to mark the sample private. Default is True. | Optional |
| Tags | Comma-separated list of tags applied to this sample. This supports Jinja template input. Example: test, 123, {{some_name}}. | Optional |
| Playbook | Name of a ThreatGrid playbook to apply to this sample run. To run nothing put "none". By default, it runs the default playbook configured in ThreatGrid. This supports Jinja template input. | Optional |
| Poll Interval | Poll Interval in seconds. It controls how frequently to check if the analysis is complete. The default is 20 seconds. | Optional |
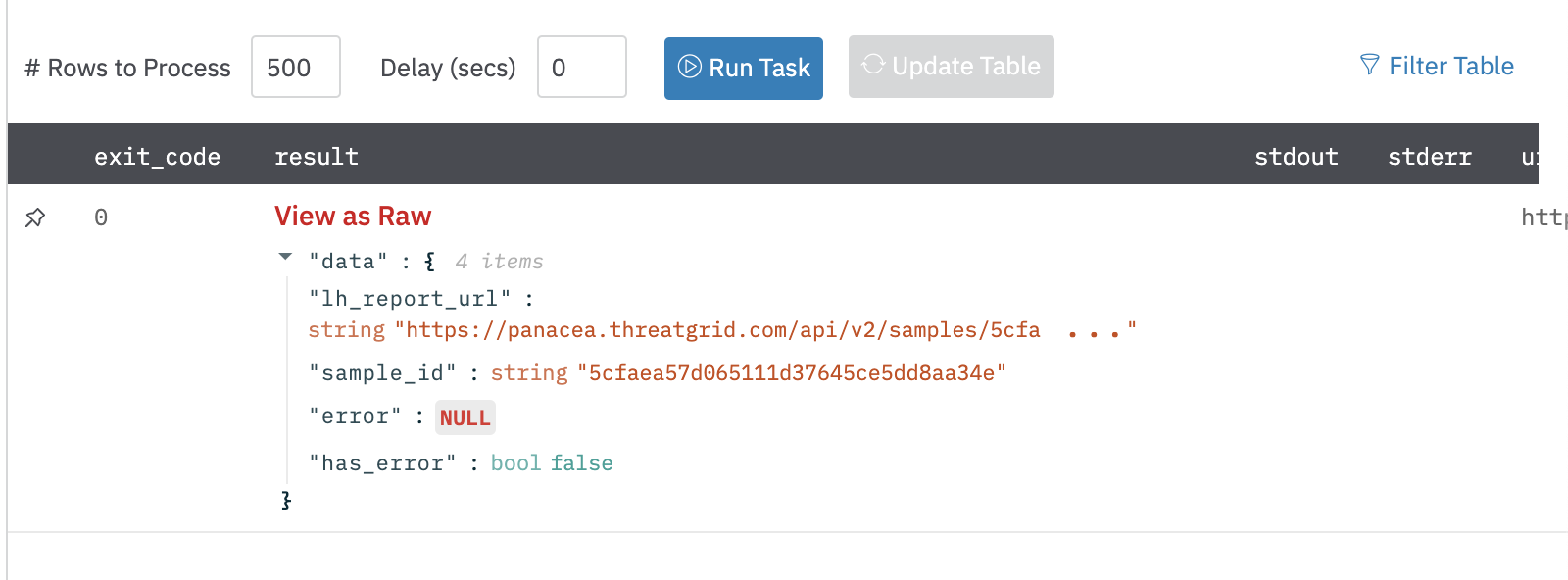
Output
A JSON object containing a link to the analysis report:
{
"lh_report_url": "https://panacea.threatgrid.com/api/v2/samples/53c675af6176f5946e562ad7330565eb/report.html",
"sample_id": "53c675af6176f5946e562ad7330565eb",
"error": null,
"has_error": false
}
URL Analysis
Submits a URL to Threat Grid for analysis and waits for completion. Completion of analysis may take time, we recommend you to use appropriate timeout and multi-threading options.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| URL | Column name that contains URL to be submitted. | |
| VM Name | Name of the VM to use to analyze. Example: win7-x64 , Windows 7 64-bit. By default, ThreatGrid will select the best VM based on the properties of the submitted sample (URL). This supports Jinja template input. | Optional |
| Private | Select to mark the sample private. Default is True. | Optional |
| Tags | Comma-separated list of tags applied to this sample. This supports Jinja template input. Example: test, 123, {{some_name}}. | Optional |
| Playbook | Name of a ThreatGrid playbook to apply to this sample run. To run nothing put "none". By default, it runs the default playbook configured in ThreatGrid. This supports Jinja template input. | Optional |
| Poll Interval | Poll Interval in seconds. It controls how frequently to check if the analysis is complete. The default is 20 seconds. | Optional |
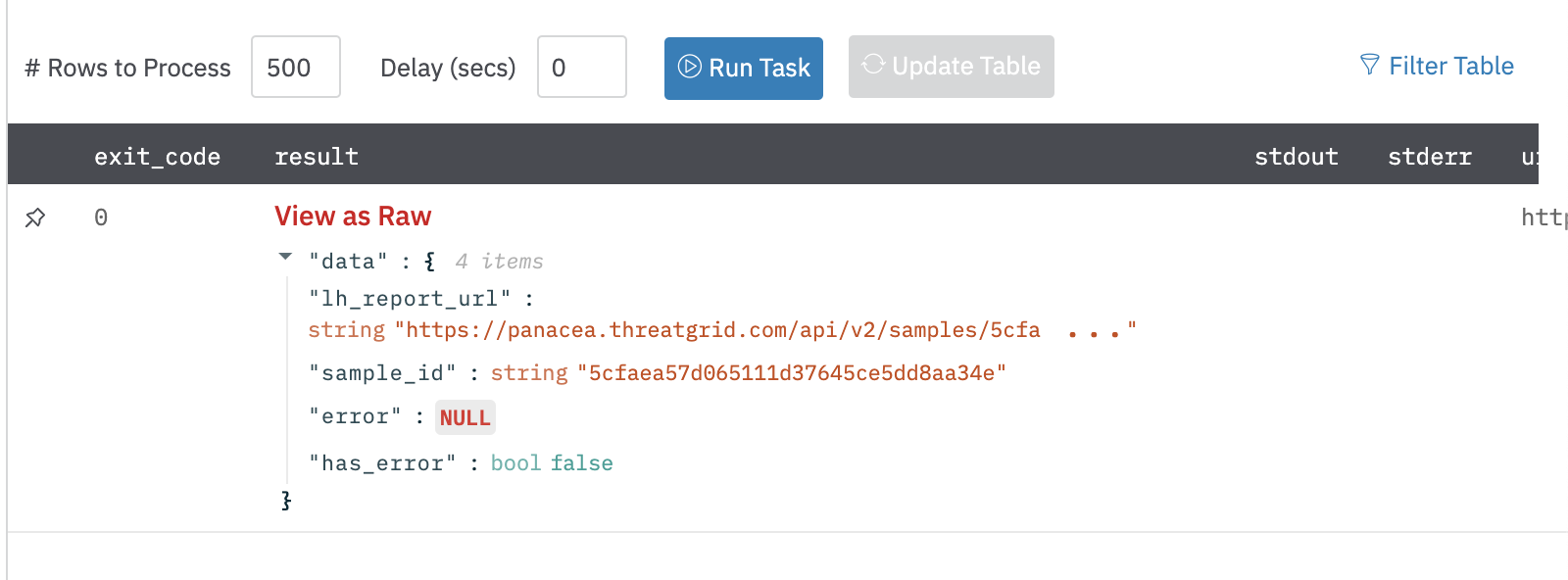
Output
A JSON object containing a link to the analysis report:
{
"lh_report_url": "https://panacea.threatgrid.com/api/v2/samples/53c675af6176f5946e562ad7330565eb/report.html",
"sample_id": "53c675af6176f5946e562ad7330565eb",
"error": null,
"has_error": false
}
Search Submissions
Search all public submission records. Use appropriate filter options to control and refine the search queries.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Start Time | Jinja-templated text for start time (Default is Batch start time). Example: 2020-09-01T22:02:24-07:00. | Optional |
| End Time | Jinja-templated text for end time (Default is Batch end time). Example: 2020-10-01T22:02:24-07:00. | Optional |
| Query | Jinja-templated text containing query to filter the search results. Example: {{query_column}}. | Optional |
| Organization Only | Select to restrict results to those submitted by the user's organization (Default is False). | Optional |
| Use Only | Select to restrict results to those submitted by the user (Default is False). | Optional |
| Sort By | Jinja-templated text containing fields on which results will be sorted by. Example: {{sort_by_column}}. | Optional |
| Sort Order | Select to mark order of the results (Default is Descending). | Optional |
| State | Select the state of the sample (Default is All). | Optional |
| Term | Jinja-templated text containing comma-delimited list of strings which select groups of submission fields. Example: {{submission_field_column1}}, {{submission_field_column2}}. | Optional |
| Limit | Restrict the number of records returned (Default is 10000). | Optional |
Output
List of Submissions
{
"error": null,
"has_error": false,
"item": {
"analysis": {
"behaviors": [
{
"name": "antivirus-flagged-artifact",
"threat": 72,
"title": "Artifact Flagged by Antivirus"
},
{
"name": "pe-encrypted-section",
"threat": 9,
"title": "Executable with Encrypted Sections"
},
{
"name": "pe-header-timestamp-prior",
"threat": 3,
"title": "PE COFF Header Timestamp is Set to Date Prior to 1999"
},
{
"name": "file-ini-modified",
"threat": 35,
"title": "Process Modified INI File"
},
{
"name": "pe-section-shared",
"threat": 24,
"title": "PE Has Sections Marked Shareable"
},
{
"name": "pe-tls-callback",
"threat": 24,
"title": "PE Contains TLS Callback Entries"
},
{
"name": "modified-file-in-user-dir",
"threat": 56,
"title": "Process Modified File in a User Directory"
},
{
"name": "pe-resource-lang-korean",
"threat": 15,
"title": "PE Resource Indicates Korean Origin"
},
{
"name": "artifact-flagged-antianalysis",
"threat": 64,
"title": "Static Analysis Flagged Artifact As Anti-Analysis"
},
{
"name": "hook-installed",
"threat": 14,
"title": "Hook Procedure Detected in Executable"
},
{
"name": "pe-certificate-invalid-signing-date",
"threat": 30,
"title": "Executable Signing Date Invalid"
},
{
"name": "artifact-flagged-vm",
"threat": 56,
"title": "Static Analysis Flagged Artifact As VM Aware"
},
{
"name": "file-ini-read",
"threat": 15,
"title": "Process Read INI File"
},
{
"name": "pe-uses-armadillo",
"threat": 9,
"title": "Executable Uses Armadillo"
},
{
"name": "artifact-flagged-anomaly",
"threat": 48,
"title": "Static Analysis Flagged Artifact As Anomalous"
},
{
"name": "antivirus-service-flagged-artifact-mid",
"threat": 66,
"title": "Artifact Flagged by Antivirus Engines"
},
{
"name": "high-heuristic-score",
"threat": 85,
"title": "Specific Set Of Indicators Signaling High Likelihood of Maliciousness Detected"
},
{
"name": "pe-filename-mismatch",
"threat": 64,
"title": "File Name of Executable on Disk Does Not Match Original File Name"
},
{
"name": "imports-IsDebuggerPresent",
"threat": 4,
"title": "Executable Imported the IsDebuggerPresent Symbol"
},
{
"name": "memory-execute-readwrite",
"threat": 25,
"title": "Potential Code Injection Detected"
},
{
"name": "modified-executable",
"threat": 60,
"title": "Process Modified an Executable File"
},
{
"name": "artifact-vm-detect",
"threat": 72,
"title": "Artifact With Virtual Environment Enumeration Detected"
},
{
"name": "pe-certificate",
"threat": 10,
"title": "Executable Signed With Digital Certificate"
},
{
"name": "created-executable-in-user-dir",
"threat": 57,
"title": "Process Created an Executable in a User Directory"
}
],
"metadata": {
"analyzed_file": {
"filename": "bdadfd07680c461a34ab09cc15.exe",
"magic": "PE32 executable (GUI) Intel 80386, for MS Windows",
"md5": "bdadfbc07680c461a34ab09cc15",
"sha1": "b7faced14eaaf8652ed1efcd834e1d58e160",
"sha256": "bd1393d1a67f054d7f312b40e0d3f8227a37db4a0e0ff32352",
"size": 5937880,
"type": "exe"
},
"general_details": {
"report_created": "2021-03-30T14:53:53Z",
"sandbox_id": "-",
"sandbox_version": "pilot-d"
},
"malware_desc": [
{
"filename": "bdadfd8c07680c461a34ab09cc15.exe",
"magic": "PE32 executable (GUI) Intel 80386, for MS Windows",
"md5": "bdadfd8c07680c461a34ab09cc15",
"sha1": "b7faced1eaaf8652ed1efcd834e1d58e160",
"sha256": "bd1393d1a3084ae67367f054d7f312b40e0d3f8227a37db4a0e0ff32352",
"size": 5937880,
"type": "exe"
},
{
"filename": "bdadfd8513b680c461a34ab09cc15",
"magic": "PE32 executable (GUI) Intel 80386, for MS Windows",
"md5": "bdadfd8507680c461a34ab09cc15",
"sha1": "b7faced16c04eaaf8652ed1efcd834e1d58e160",
"sha256": "bd1393d1a3084a367f054d7f312b40e0d3f8227a37db4a0e0ff32352",
"size": 5937880,
"type": "exe"
}
],
"sandcastle_env": {
"analysis_end": "2021-03-30T14:53:53Z",
"analysis_features": [],
"analysis_start": "2021-03-30T14:46:50Z",
"controlsubject": "-",
"current_os": "7601.18798.amd64fre.win7sp1_gdr.150316-1654",
"display_name": "Windows 7 64-bit",
"run_time": 300,
"sample_executed": 1617115665,
"sandcastle": "-",
"vm": "win7-x64",
"vm_id": "061f2d9002d08c2113eb4027c082"
},
"submitted_file": {
"filename": "bdadfd851c07680c461a34ab09cc15",
"magic": "PE32 executable (GUI) Intel 80386, for MS Windows",
"md5": "bdadfd8513680c461a34ab09cc15",
"sha1": "b7faced16e4eaaf8652ed1efcd834e1d58e160",
"sha256": "bd1393d1084ae6bc1b67367f054d7f312b40e0d3f8227a37db4a0e0ff32352",
"size": 5937880,
"type": "exe"
}
},
"threat_score": 85
},
"filename": "bdadfd8513c07680c461a34ab09cc15",
"login": null,
"md5": "bdadfd8513b7680c461a34ab09cc15",
"organization_id": null,
"private": false,
"sample": "061f2d2d08dcb5c2113eb4027c082",
"sha1": "b7fac04eaaf8652ed1efcd834e1d58e160",
"sha256": "bd1393d1a32b40e0d3f8227a37db4a0e0ff32352",
"state": "succ",
"status": "job_done",
"submitted_at": "2021-03-30T14:46:46Z",
"tags": [],
"vm_runtime": 300
},
"matches": {},
"score": 1000000
}
Search Samples (Beta)
Single-term searches for a specific entity data type. Use appropriate filter options to control and refine the search queries.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Start Time | Jinja-templated text for start time (Default is Batch start time). Example: 2020-09-01T22:02:24-07:00. | Optional |
| End Time | Jinja-templated text for end time (Default is Batch end time). Example: 2020-10-01T22:02:24-07:00. | Optional |
| Query | Jinja-templated text containing query to filter the search results. Example: {{query_column}}. | Optional |
| Term | Jinja-templated text containing comma-delimited list of strings which select groups of submission fields. Example: {{submission_field_column1}}, {{submission_field_column2}}. | Optional |
Output
List of Samples
Release Notes
v2.0.0- Updated architecture to support IO via filesystem
Updated over 2 years ago