Smokescreen
Version: 2.0.0
Smokescreen's IllusionBLACK deception platform detects cyber attacks like reconnaissance, spear phishing, lateral movement, stolen credentials and data theft.
Connect Smokescreen with LogicHub
- Navigate to Automations > Integrations.
- Search for Smokescreen.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- Base URL: example, https://logichub.smokescreen.com
- x-client-id
- x-client-auth
- After you've entered all the details, click Connect.
Actions for Smokescreen
Get All Network Decoys
This is used to get details about all network decoys deployed on IllusionBLACK.
Input Field
Choose a connection that you have previously created to complete the connection.
Output
Gives network decoys from ILlusionBLACK.
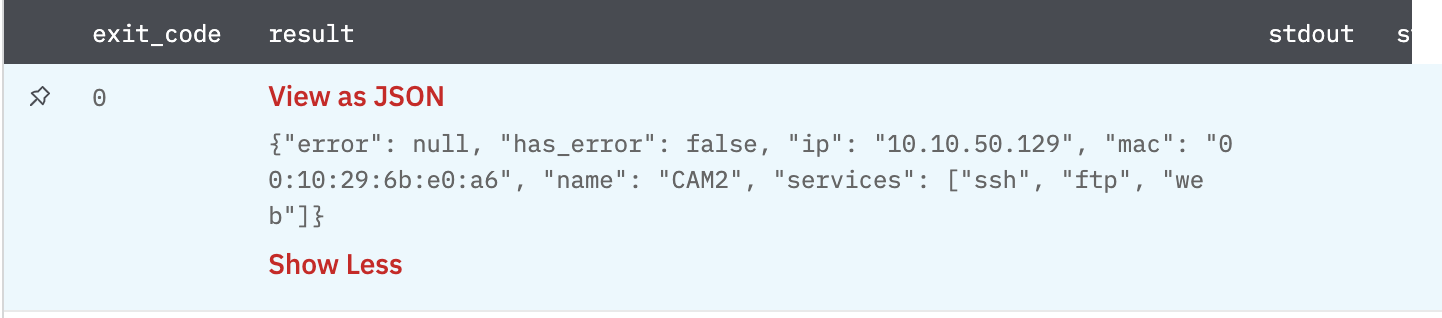
Get All AD Decoys
This is used to get details about all AD decoys deployed on IllusionBLACK.
Input Field
Choose a connection that you have previously created to complete the connection.
Output
Gives AD decoys from ILlusionBLACK.
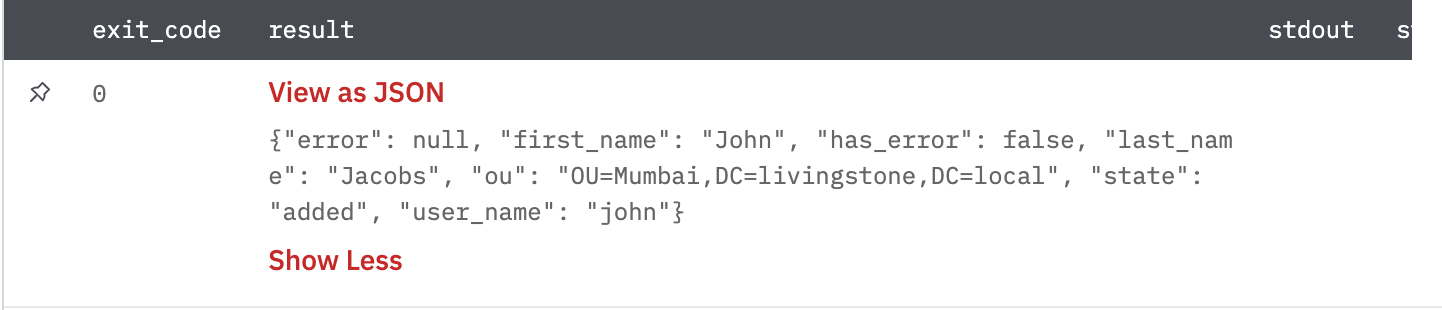
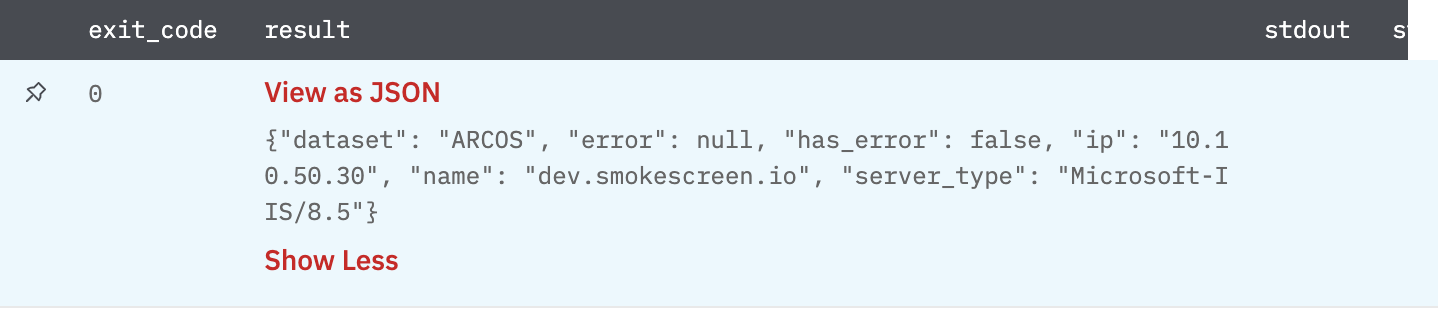
Get All TI Decoys
This is used to get details about all TI decoys deployed on IllusionBLACK.
Input Field
Choose a connection that you have previously created to complete the connection.
Output
Gives TI decoys from ILlusionBLACK.
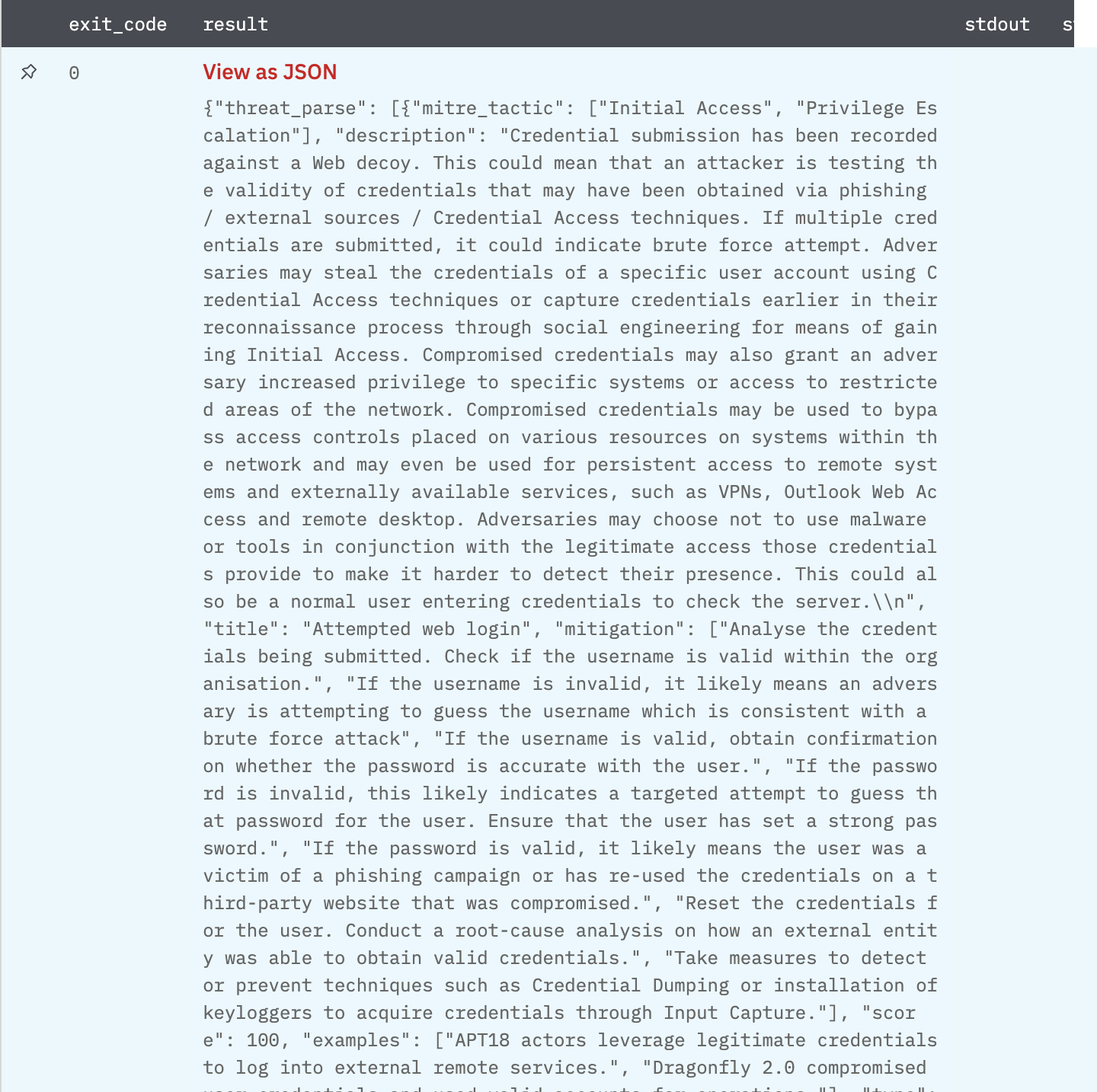
Get Raw Events from IllusionBLACK
Get events from IllusionBLACK filtering using the IllusionBLACK extensive rule engine.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| From | Get events from datetime which is 8601 formatted string. | Required |
| To | Get events to datetime which is 8601 formatted string. | Required |
| Limit | The number of events sent in response per API call. | Required |
| Expfilter | An IllusionBLACK rule engine query string. Detailed documentation on the rule engine is here: https://drive.google.com/file/d/1bnDzyUCLD5-fBjQVr9tNbDeYRq1-AMyb/view?usp=sharing | Required |
| Whitelisted | Return whitelisted events or not. | Required |
| Resolved | Return resolved events or not. | Required |
Output
Returns the list of Events and Threat Parse data associated with them.
Release Notes
v2.0.0- Updated architecture to support IO via filesystem
Updated over 2 years ago