CrowdStrike Falcon Host (OAuth Based)
Version: 2.3.11
CrowdStrike Falcon Host uniquely combines an array of powerful methods to provide prevention against the rapidly changing tactics, techniques and procedures (TTPs) used by adversaries to breach organizations - including commodity malware, zero-day malware and even advanced malware-free attacks.
Connect CrowdStrike with LogicHub
- Navigate to Automations > Integrations.
- Search for CrowdStrike.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- URL: URL to your CrowdStrike Falcon Host (OAuth Based) instance. Example: https://api.crowdstrike.com
- Client ID: Client ID of your CrowdStrike Falcon Host.
- Client Secret: Client Secret of your CrowdStrike Falcon Host.
- After you've entered all the details, click Connect.
Actions for CrowdStrike
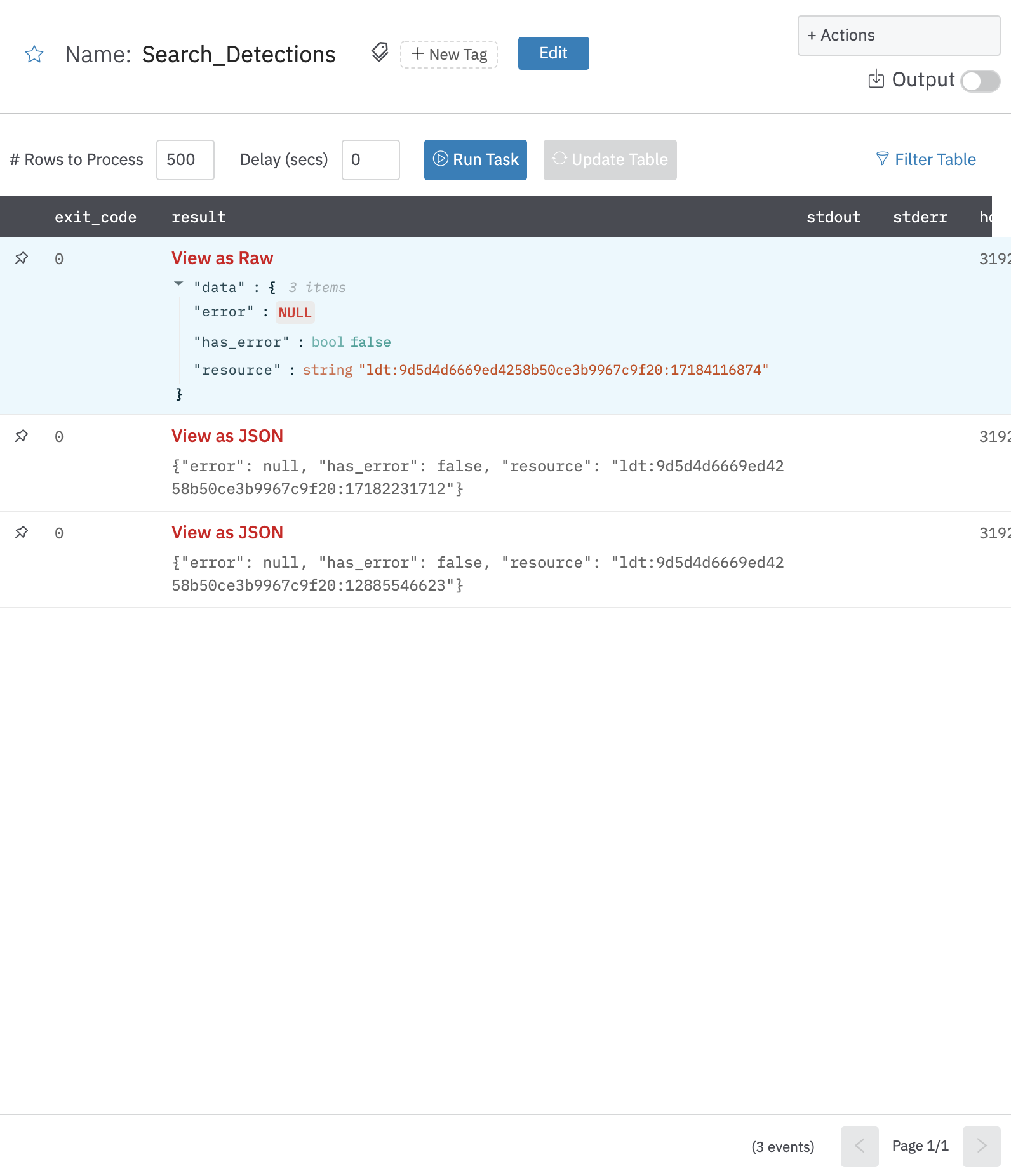
Search Detections (Deprecated)
Search for detection IDs that match a given query.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Query | Search all detection metadata for the provided string. Example: 'malicious' | Optional |
| Sort | Sort detections using these options. (Default is 'Max Severity: Descending'). | Optional |
| Filter | Filter detections using a query in Falcon Query Language (FQL) An asterisk wildcard * includes all results. Example: 'behaviors.behavior_id: {{behavior_id_column}}'. | Optional |
| Offset | The first detection to return, where 0 is the latest detection. Use with 'Limit' to manage pagination of results. | Optional |
| Limit | The maximum number of detections to return in this response (default: 9999; max: 9999). Use with 'Offset' to manage pagination of results. | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Detection details
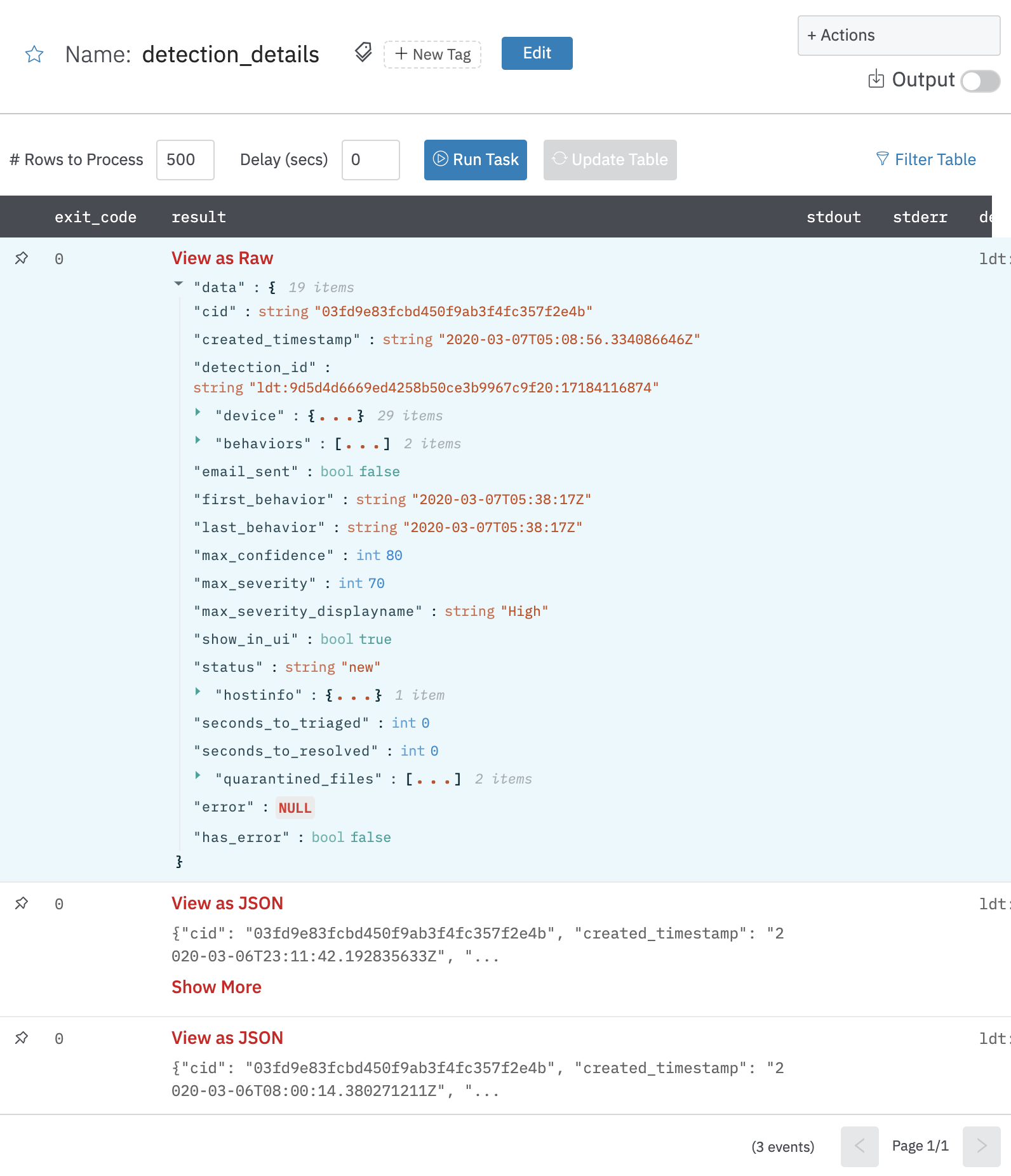
Get Detection Details (Deprecated)
Get detection details action allows you to view details for specific detections given one or more detection IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Detection ID Column Name | Column name from the parent table to lookup value for detection ID. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other fields of detections
Modify Detection (Deprecated)
Change the state and assignee of one or more detections.
Note
In addition to
FalconXScope,User Management[Read] Scope is also required for this integration action to work. This is required to create a mapping of the assignee uid (email) vs. the corresponding UUID to supply it to the remote API.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Detection ID | Column name from the parent table to lookup value for detection id to modify. | Required |
| Assignee | Column name from the parent table to lookup value for uid of the assignee (typically an email id) to modify the detection with. An empty value will ignore the updation of the assignee for that detection. | Optional |
| Status | Status to modify all the detection with among New/InProgress/TruePositive/FalsePositive/Ignored/Closed/Reopened. Note: One of Assignee or Status must be provided. | Optional |
| Comment | Jinja-templated comment to add to the detection. Comments are displayed with the detection in Falcon and usually used to provide context or notes for other Falcon users. A detection can have multiple comments over time. Example: Changed assignee of Detection: {{dection_id_column}} to {{assignee_uuid_column}} by LogicHub. | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Successfully Updated
{
"result": "Successfully updated",
"error": null,
"has_error": false
}
Search Devices
Search for devices based on a filter.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Devices Filter Template Column Name | Jinja2 template for the device filter. Following are a few examples. Find more on falcon API documentation. 1. To find devices with host name hostname: '{{hostcolumn}}' 2. To find devices based on prefix or suffix use wildcard ' ' (supported by few fields) hostname: '{{hostprefix_column}}' 3. To find devices with local IP local_ip: '{{ip_column}}' 4. To find devices which matches both hostname and platform '+' operator is used. Example: hostname: '{{host_column}}' + platform_name:'{{platform_column}}'5. To find devices which matches either hostname or platform name ' , ' operator is used. Example: hostname: '{{host_column}}' , platform_name:'{{platform_column}}' | Required |
| Max Number of Results | Number of results to fetch (default is 100 results). | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Device details
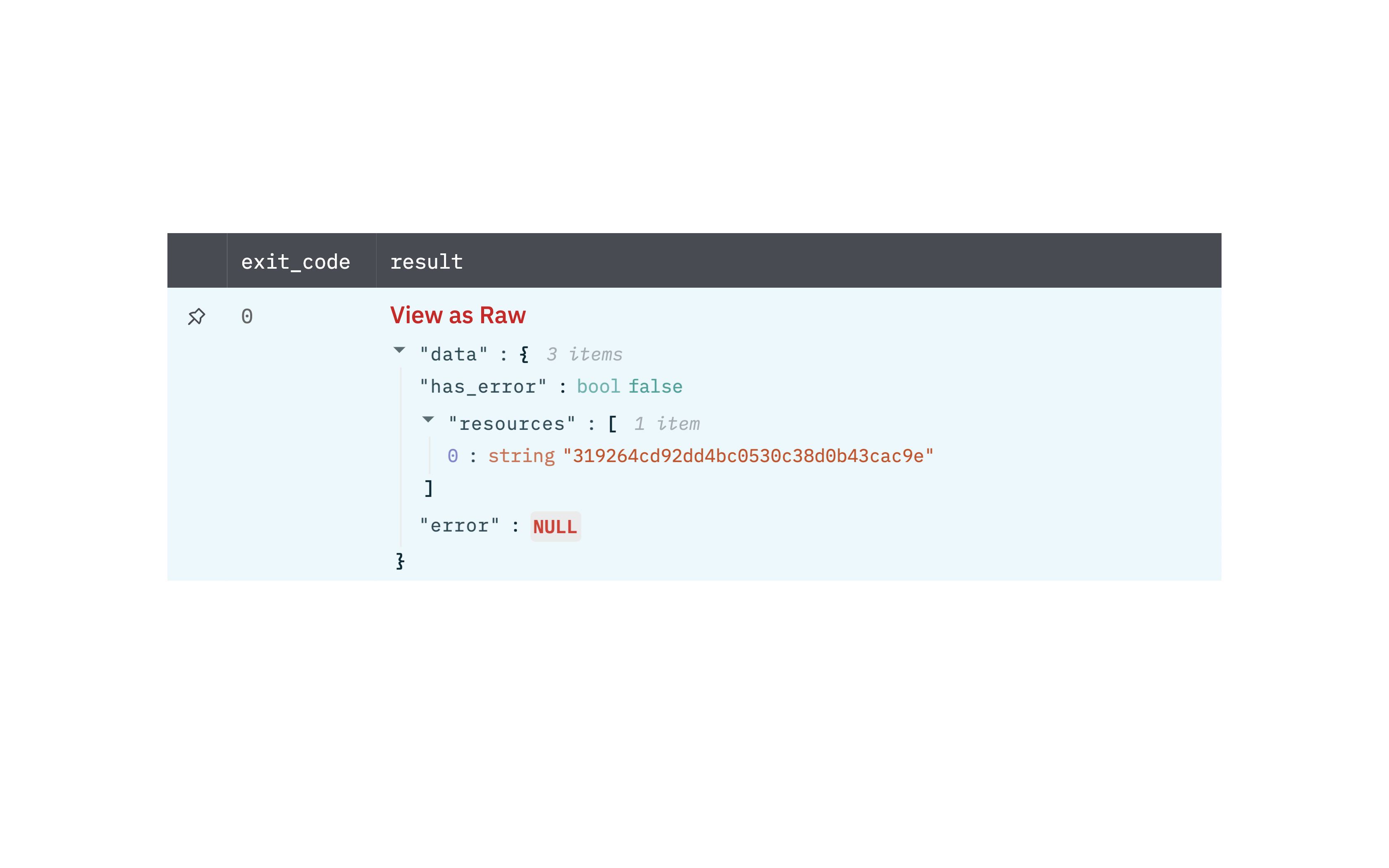
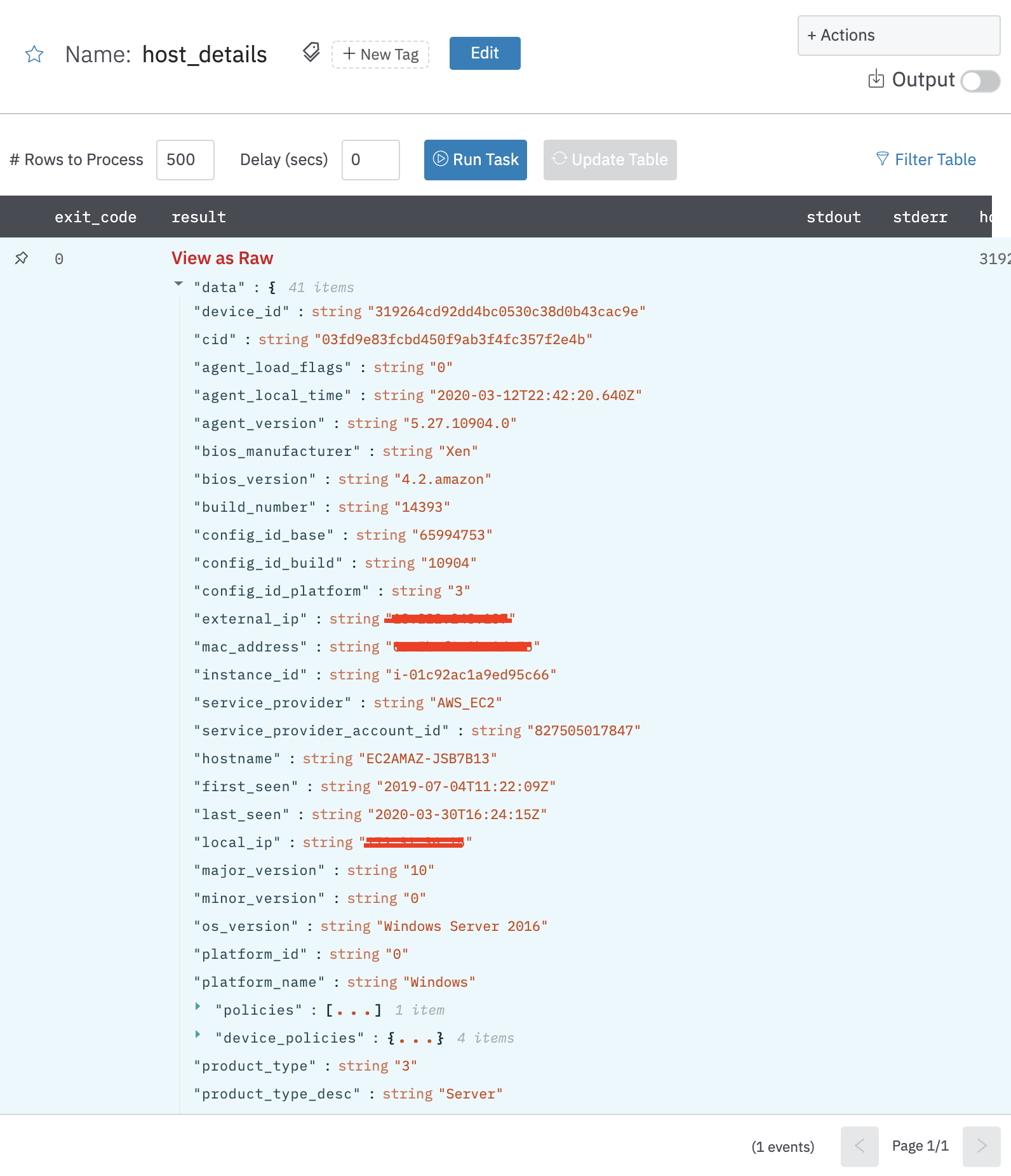
Get Device Details
Get device details action allows you to view details for specific devices given one or more device IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Device ID Column Name | Column name from the parent table to lookup value for the device ID. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other fields of device
Search Processes
Search for processes associated with a custom IOC type.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| IOC Type | Select IOC Type. sha256/md5/domain/ipv4/ipv6. | Required |
| Indicator Values | Select column containing the string representation of the indicator. | Required |
| Device ID | Specify a host's ID to return only processes from that host. | Required |
| Max Number of Results | Number of results to fetch (default is 100 results). | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Process details
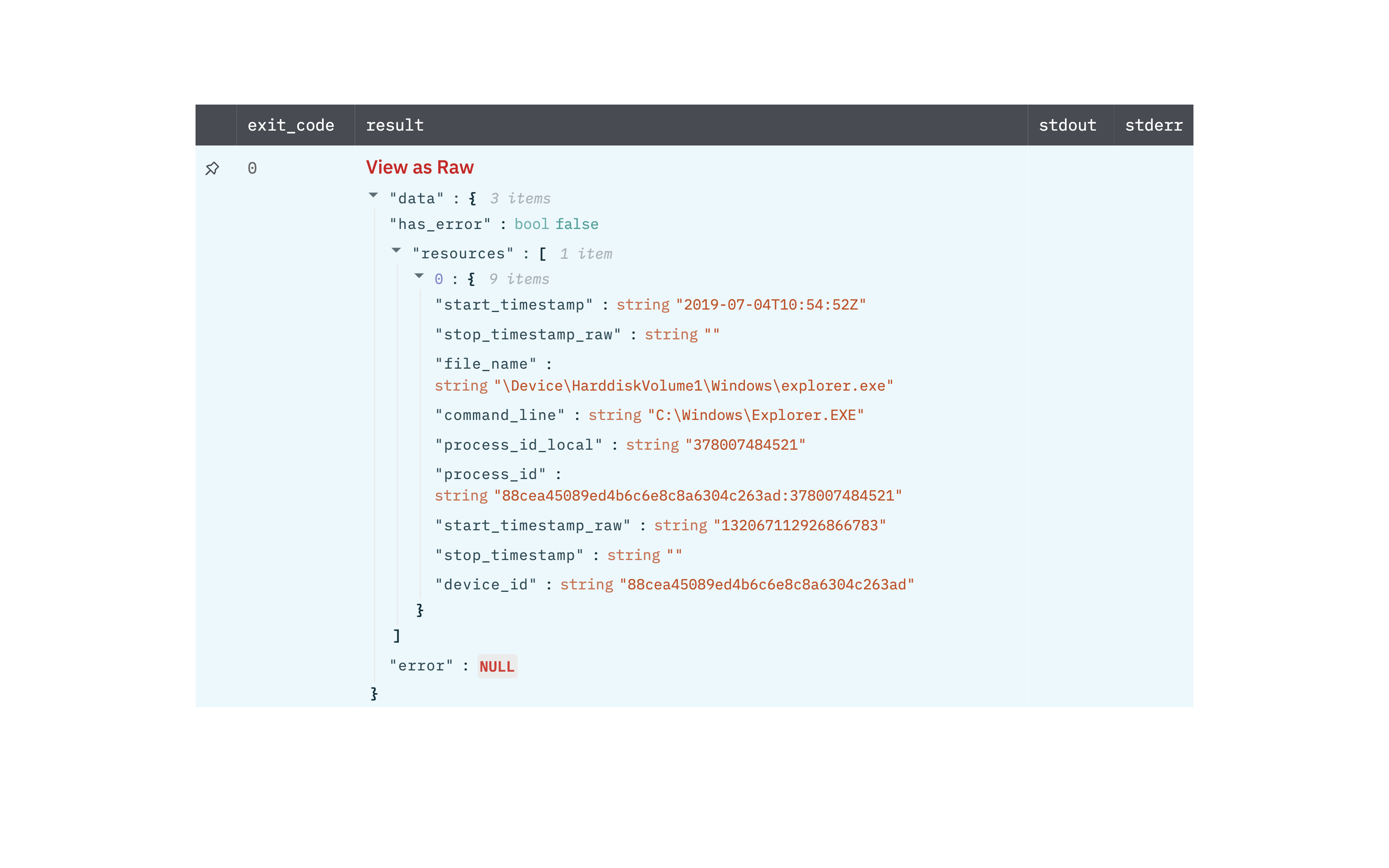
Get Process Details
Retrieve the details of a process that is running or that previously ran, given one or more process IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Process ID Column Name | Column name from the parent table to lookup value for process ID. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other fields of process
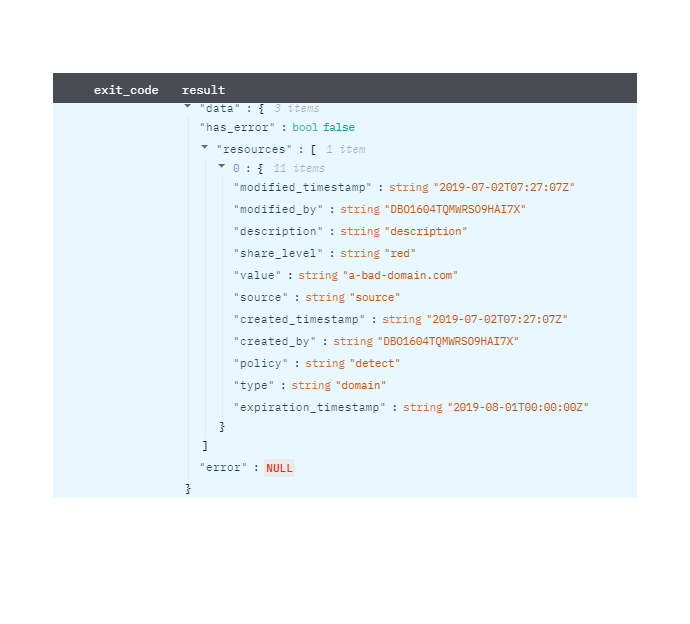
Search IOCs
Search custom IOCs in your account
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| IOC Type | Select IOC Type. sha256/md5/domain/ipv4/ipv6. | Optional |
| Indicator Values | Select column containing the string representation of the indicator. | Optional |
| Indicator Policy | Select Indicator Policy. detect/none. | Optional |
| Source | The source where this indicator originated. This can be used for tracking where this indicator was defined. Limit 200 characters. | Optional |
| Created By | The user or API client who created the custom IOC. | Optional |
| Deleted By | The user or API client who deleted the custom IOC. | Optional |
| Include Deleted | Select the option to include deleted IOCs. | Optional |
| After Timestamp | Find custom IOCs created after this time (RFC-3339 timestamp). | Optional |
| Before Timestamp | Find custom IOCs created before this time (RFC-3339 timestamp). | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: IOC details
Get IOC Details
Get IOC (Indicators of Compromise) details based on value and type.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| IOC Type | Select the value of IOC Type. | Required |
| IOC Value Column Name | Column name from parent table that contains IOC value. |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other fields of IOC
Create Custom IOCs
Create new IOCs to block custom domains, hashes or ips
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Indicator Type | Select IOC Type. | Required |
| Indicator Value | The string representation of the indicator | Required |
| Action | Select Action | Required |
| Severity | Select Severity (Required for the Prevent and Detect action) | Required |
| Platforms | Jinja-Templated text containing CSVs of platforms that the indicator applies to. Example: mac,linux,{{os}} | Required |
| Source | Jinja-Templated text containing the source where this indicator originated. This can be used for tracking where this indicator was defined (Limit is 256 characters). Example: {{source}} | Optional |
| IOC Description | Jinja-Templated text containing descriptive label for this custom IOC. Example: {{description}} | Optional |
| Tags | Jinja-Templated text containing CSVs of tags to apply to the indicator. Example: test_tag,{{tags}} | Optional |
| Host Groups | Jinja-Templated text containing CSVs of host group IDs that the indicator applies to. Example: sbcd,{{host_groups}} | Optional |
| Applied Globally | Select option for applied globally (Default is False). | Optional |
| Expiration | Jinja-Templated text containing the value of the date on which the indicator will become inactive (format is 2021-04-17T09:12:36-00:00). Example: {{date}} | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
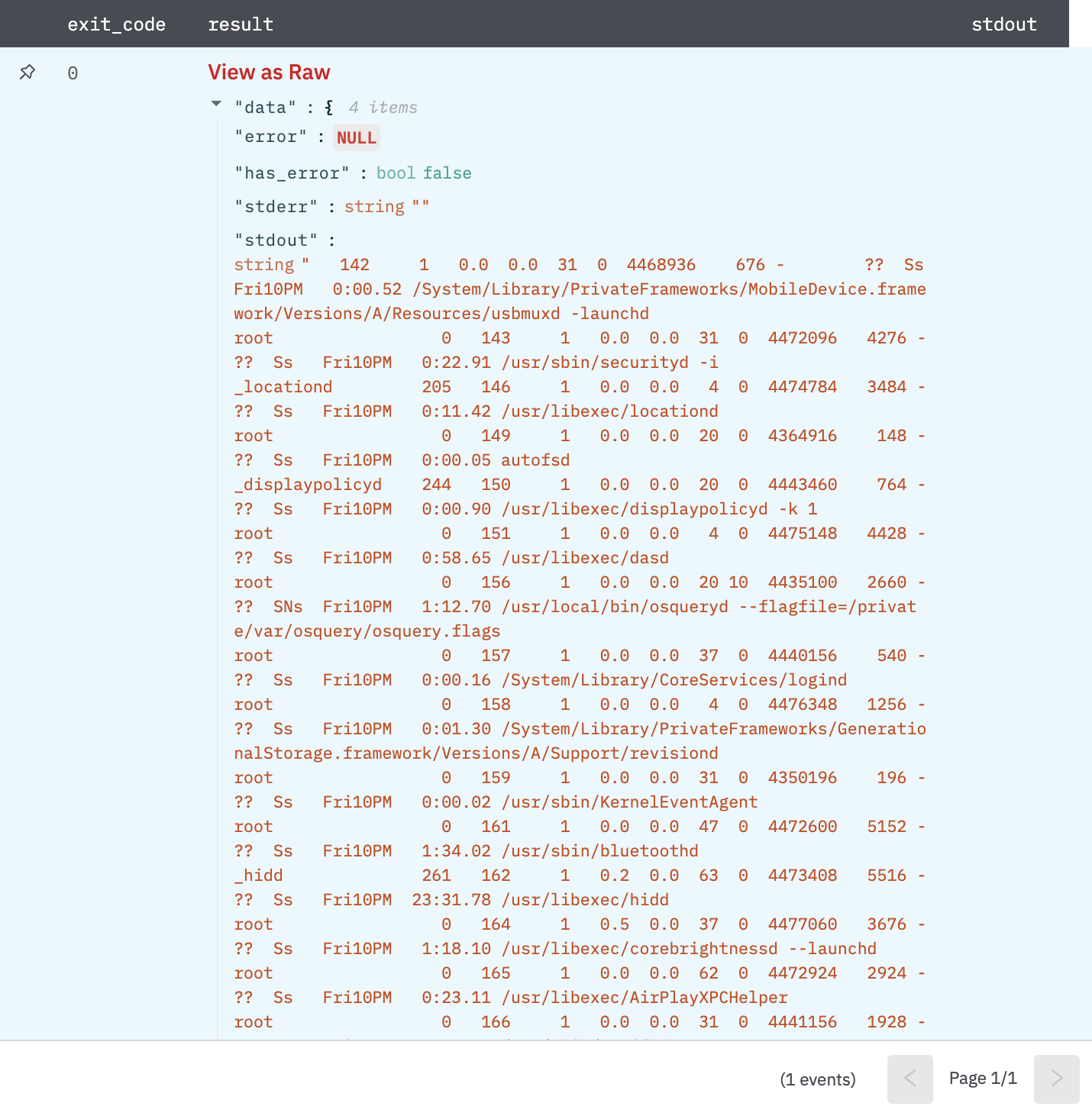
RTR Command: Single Host
Send Real-Time Response commands to a single host.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Command Scope | Select Scope of RTR Command. RTR Read-Only Analyst/RTR Active Responder/RTR Administrator. | Required |
| Device ID | The Host Agent ID of the device on which an RTR command is to be sent. | Required |
| Command String | Full command string for the command. For example, cd C:\some_directory. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- stdout: output response of running the RTR command on the host
- stderr: error response of running the RTR command on the host
Take Action on Devices
Take various actions on the hosts in your environment. Contain or lift containment on hosts. Delete or restore hosts.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Action Name | Select one of the actions: - Contain: This action contains the host, which stops any network communications to locations other than the CrowdStrike cloud and IPs specified in your containment policy. - Lift Containment: This action lifts containment on the host, which returns its network communications to normal. - Hide Host: This action will delete a host. After the host is deleted, no new detections for that host will be reported via UI or APIs. - Unhide Host: This action will restore a host. Detection reporting will resume after the host is restored | Required |
| Device ID | The Host Agent ID of the device. | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Successfully executed action on host
Search Incidents
Search for incidents by providing an FQL filter, sorting, and paging details.
Input Field
| Input Name | Description | Required |
|---|---|---|
| Filter | Filter criteria in the form of an FQL query. For more information about FQL queries, see documentation (https://falcon.crowdstrike.com/support/documentation/45/falcon-query-language-fql) in Falcon. | Optional |
| Sort | Enter the jinja-templated property to sort on, followed by a dot (.), followed by the sort direction, either "asc" or "desc". Example: {{property}}.{{direction}} or start.desc | Optional |
| Limit | Maximum number of incidents to return. (Default is 500). Note: Crowdstrike allows us to fetch only 500 results in a single API call, therefore a value greater than 500 will involve multiple API calls and may take some time. Increase Action Timeout, in case of action, gets timed out. | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: incident-id of a matched incident
{
"error": null,
"has_error": false,
"result": "inc:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
}
Get Incident Details
Get details on incidents by providing incident IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Column name from the parent table to lookup value for the incident ID. |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other keys containing incident details
{
"incident_id": "inc:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx:xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"incident_type": 1,
"cid": "c2f696880d9b4371b9760f7536078690",
"host_ids": [
"xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
],
"hosts": [
{
"device_id": "xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx",
"cid": "c2f696880d9b4371b9760f7536078690",
"agent_load_flags": "0",
"agent_local_time": "2020-09-23T13:51:08.032Z",
"agent_version": "5.37.11804.0",
"bios_manufacturer": "Apple Inc.",
"bios_version": "199.0.0.0.0",
"config_id_base": "65994753",
"config_id_build": "11804",
"config_id_platform": "4",
"external_ip": "xx.xx.xx.xx",
"hostname": "my-backup.local",
"first_seen": "2020-07-20T04:09:07Z",
"last_seen": "2020-09-23T14:11:08Z",
"local_ip": "127.0.0.1",
"mac_address": "xx-xx-xx-xx-xx-xx",
"major_version": "19",
"minor_version": "6",
"os_version": "Catalina (10.15)",
"platform_id": "1",
"platform_name": "Mac",
"product_type_desc": "Workstation",
"status": "normal",
"system_manufacturer": "Apple Inc.",
"system_product_name": "MacBookPro11,4",
"modified_timestamp": "2020-09-23T14:12:17Z"
}
],
"created": "2020-09-23T14:32:32Z",
"start": "2020-09-23T14:32:32Z",
"end": "2020-09-23T14:54:21Z",
"state": "closed",
"assigned_to": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"assigned_to_name": "Saurabh Prakash",
"status": 40,
"tactics": [
"Persistence"
],
"techniques": [
"Modify Existing Service"
],
"objectives": [
"Keep Access"
],
"modified_timestamp": "2020-09-23T14:45:15.179411419Z",
"fine_score": 10,
"error": null,
"has_error": false
}
Falcon X Sandbox File Upload
Upload a file for sandbox analysis. After uploading, use Falcon X Sandbox Analysis to start analyzing the file.
Max file size: 100 MB.
Accepted file formats:
- Portable executables: .exe, .scr, .pif, .dll, .com, .cpl.
- Office documents: .doc, .docx, .ppt, .pps, .pptx, .ppsx, .xls, .xlsx, .rtf, .pub
- APK
- Executable JAR
- Windows script component: .sct
- Windows shortcut: .lnk
- Windows help: .chm
- HTML application: .hta
- Windows script file: .wsf
- Javascript: .js
- Visual Basic: .vbs, .vbe
- Shockwave Flash: .swf
- Perl: .pl
- Powershell: .ps1, .psd1, .psm1
- Scalable vector graphics: .svg
- Python: .py
- Linux ELF executables
- Email files: MIME RFC 822 .eml, Outlook .msg.
Input Field
| Input Name | Description | Required |
|---|---|---|
| File ID | Column name from parent table that contains LogicHub File ID of the file to be uploaded. | Required |
| File Name | Column name from parent table that contains the File name of the file to be uploaded (defaults to LogicHub File ID, if the column is not selected or if the column value is empty). | Optional |
| Comment | Jinja-templated descriptive comment to identify the file for other users. | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- sha256: SHA256 hash of the uploaded file as reported by CrowdStrike
- file_name: file name of file uploaded
{
"error": null,
"has_error": false,
"sha256": "42a615198bcdfc72839936409c88af7ded125feabfec4753b307dc985aaba48f",
"file_name": "virus.exe"
}
Falcon X Sandbox Analysis
Submit either a URL or a sample SHA256 for sandbox analysis. For SHA256 analysis, a file needs to be uploaded to Falcon X first using the action Falcon X Sandbox File Upload. This action waits for the analysis to complete for each row of input. Use the appropriate number of Thread Count to make this action run faster (Recommended: max number of rows expected in the input table). As per Crowdstrike, the time required for each resource to be analyzed varies but is usually less than 15 minutes. Therefore, set Action Timeout appropriately.
Input Field
| Input Name | Description | Required |
|---|---|---|
| Type | Select type SHA256/ URL of analysis you want to run. | Required |
| URL/SHA256 | Column name from parent table that contains URL or SHA256 of the file to analyze. Appropriate Type above must be selected for the action to perform correctly. | Required |
| Environment ID | The environment relevant to the URLs/SHA being analyzed. - Linux (Ubuntu 16.04, 64 bit) - Android Static Analysis - Windows 10 64 bit - Windows 7 64 bit - Windows 7 32 bit | Required |
| Report Type | Select the type of report Detailed/Summarized you want to get. (Default is Summarized) | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- other keys representing the information in the report
{
"id": "c2f696880d9b4371b9760f7536078690_d00d7b1b2c184d24a63d2c59d638a052",
"cid": "c2f696880d9b4371b9760f7536078690",
"created_timestamp": "2020-12-02T04:08:00Z",
"origin": "apigateway",
"sandbox": [
{
"sha256": "dac3aaa58e1796468ee1b96d8c1c59c8192bff99b1622a1cf09e71ea2a8f8e72",
"environment_id": 100,
"environment_description": "Windows 7 32 bit",
"submit_name": "dac3aaa58e1796468ee1b96d8c1c59c8192bff99b1622a1cf09e71ea2a8f8e72",
"submission_type": "file",
"verdict": "no specific threat",
"file_type": "PDF document, version 1.6",
"sample_flags": [
"Extracted Files"
]
}
],
"verdict": "no specific threat",
"ioc_report_strict_csv_artifact_id": "65172ac1acf79d79958462f9123ee8f365f0e474c92185a2616adc2db2c19360",
"ioc_report_broad_csv_artifact_id": "65172ac1acf79d79958462f9123ee8f365f0e474c92185a2616adc2db2c19360",
"ioc_report_strict_json_artifact_id": "734de9198c5a6eae53e2a1a062e83ff9981d2c2a0cde4276a5235db5100cf795",
"ioc_report_broad_json_artifact_id": "734de9198c5a6eae53e2a1a062e83ff9981d2c2a0cde4276a5235db5100cf795",
"ioc_report_strict_stix_artifact_id": "205d28c146e45927ad04f99e6154a62682ec1f8fc5a62d8ff5005a8854c81717",
"ioc_report_broad_stix_artifact_id": "205d28c146e45927ad04f99e6154a62682ec1f8fc5a62d8ff5005a8854c81717",
"ioc_report_strict_maec_artifact_id": "0ad1af8daad615421fca9aa2bdbc3271a0225c3cee691f5d9fed2bacfa8e6190",
"ioc_report_broad_maec_artifact_id": "0ad1af8daad615421fca9aa2bdbc3271a0225c3cee691f5d9fed2bacfa8e6190",
"error": null,
"has_error": false
}
Run GraphQL Query
Run graphQL query
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Query | Jinja-templated text containing the graphQL query to execute. | Required |
Output
JSON containing the following items:
{
"data":
{
"timeline":{
"edges":[{
"node":{
"__typename":"SomeControllerEvent",
"eventType":"EVENT1",
"eventSeverity":"MODERATE",
"timestamp":"2023-03-26T08:42:11.122Z",
"startTime":"2023-03-26T08:42:11.122Z",
"endTime":"2023-03-26T08:42:11.122Z",
"state":{
"dismissed":false,
"resolved":false
},
"domainControllerEntity":{
"hostName":"test.comm"
}
}
},{
"node":{
"__typename":"SomeControllerEvent",
"eventType":"EVENT2",
"eventSeverity":"MODERATE",
"timestamp":"2023-03-26T08:42:11.122Z",
"startTime":"2023-03-26T08:42:11.122Z",
"endTime":"2023-03-26T08:42:11.122Z",
"state":{
"dismissed":false,
"resolved":false
},
"domainControllerEntity":{
"hostName":"test.com"
}
}
}],
}
},
"error":null,
"has_error":false
}
Search Alerts (Deprecated)
Search for alerts IDs that match a given filter.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Filter | Jinja-templated text containing the filter alerts using a filter query Eg: 'product: {{product_filter_column}}' | |
| Offset | The first alert to return, where 0 is the latest alert. Use with 'Limit' to manage pagination of results. | |
| Limit | The maximum number of alerts to return in this response (default: 100; max: 9999). Use with 'Offset' to manage pagination of results. |
Output
JSON containing the following items:
{
"error": null,
"has_error": false,
"resource": "eb8b5d1f79404eafaaafafee6b362ccc:cwpp:eb8b5d1f79404eafaaafafee6b362ccc:ffc50fb4a8eb463"
}
Search Alerts
Search for alerts IDs that match a given filter.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Filter | Jinja-templated text containing the filter alerts using a filter query Eg: 'product: {{product_filter_column}}' | Optional |
| Offset | The first alert to return, where 0 is the latest alert. Use with 'Limit' to manage pagination of results. | Optional |
| Limit | The maximum number of alerts to return in this response (default: 100; max: 9999). Use with 'Offset' to manage pagination of results. | Optional |
| Hidden Alerts | Jinja templated boolean value which specifies whether to include or exclude hidden alerts. (Default value is true) | Optional |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Get Alert Details
Get Alert details action allows you to view details for specific alerts given one or more alert IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert ID | Jinja-templated text containing the value for alert Id. | Required |
Output
JSON containing the following items:
{
"error": null,
"has_error": false,
"resource":{
"agent_id":"f4b5867146ed48775cd4c907838e3801",
"aggregate_id":"aggind:f4b5867146ed48775cd4c907838e3801:5068062748557",
"alleged_filetype":"exe",
"cid":"eb8b5d1f79404eafaaafafee6b362ccc",
"cloud_indicator":false,
"cmdline":"C:\WINDOWS\system32\fsquirt.exe",
"composite_id":"eb8b5d1f79404eafaaafafee6b362ccc:ind:f4b5867146ed48775cd4c907838e3801:7103546842047-41004-19523600",
"confidence":100,
"context_timestamp":"2024-01-04T09:47:56.322Z",
"control_graph_id":"ctg:f4b5867146ed48775cd4c907838e3801:5068062748557",
"crawl_edge_ids":{
"Sensor":[
"Pg&(m_CuN)i/%g0HC&j-/lQEr9E&Tr71^`N$Z= ..."]
},
"crawl_vertex_ids":{
"Sensor":[
"mod:f4b5867146ed48775cd4c907838e3801:b ..."]
},
"crawled_timestamp":"2024-01-04T10:47:58.208479481Z",
"created_timestamp":"2024-01-04T09:48:58.07280238Z",
"data_domains":["Endpoint"],
"description":"A process triggered an informational severity custom rule.",
"device":{
"agent_load_flags":"1",
"agent_local_time":"2023-1 ..."
},
"display_name":"CustomIOAWinLowest",
"falcon_host_link":"https://falcon.crowdstrike.com/activity-v2/detections/eb8b5d1f79404eafaaafafee6b362ccc:ind:f4b5867146ed48775cd4c907838e3801:7103546842047-41004-19523600",
"filename": "fsquirt.exe",
"objective":"Falcon Detection Method",
"parent_details":{"cmdline":"sihost.exe","filename":"sihost.exe","f ...}
}
Modify Alerts
Change the state and assignee of one or more alerts.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert ID | Jinja-templated text containing the value for alert Id. | Required |
| Assignee | Jinja-templated text containing the value for uid of assignee to modify the alert with. An empty value will ignore the updation of assignee for that alert. | Optional |
| Assignee Name | Jinja-templated text containing the name of assignee to modify the alert with. An empty value will ignore the updation of assignee for that alert. | Optional |
| Status | Status to modify all the detection with | Optional |
| Tag | Jinja-templated text containing tag to add to the alert. | Optional |
| Comment | Jinja-templated comment to add to the alert. Comments are displayed with the alert in Falcon and usually used to provide context or notes for other Falcon users. A alert can have multiple comments over time. Eg: Changed assignee of alert: {{alert_id_column}} to {{assignee_uuid_column}} by Devo | Optional |
Output
JSON containing the following items:
{
"error": null,
"has_error": false,
"result": "Successfully updated"
}
Create Static Host Group
Create static host group.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Host Group Body | Jinja-templated JSON containing the body of the static host group. Example {"name": "Test Group 45", "description": "A demo group", "group_type": "static"}. | Required |
Output
JSON containing the following items:
{
"errors": null,
"has_error": false,
"meta": {
"query_time": 0.450510996,
"trace_id": "trace-id"
},
"error": null,
"resources": [
{
"id": "id",
"group_type": "static",
"name": "Test Group 140001",
"description": "Test Group 140002 description",
"created_by": "api-client-id",
"created_timestamp": "2024-05-14T12:51:33.283695187Z",
"modified_by": "api-client-id",
"modified_timestamp": "2024-05-14T12:51:33.283695187Z"
}
]
}
Modify Static Host Group
Modify static host group.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Host Group Body | Jinja-templated JSON containing the body of the static host group. Example {"name": "Test Group 45", "id": "XXXX"} | Required |
Output
JSON containing the following items:
{
"errors": null,
"has_error": false,
"meta": {
"query_time": 0.450510996,
"trace_id": "trace-id"
},
"error": null,
"resources": [
{
"id": "id",
"group_type": "static",
"name": "Test Group 140001",
"description": "Test Group 140002 description",
"created_by": "api-client-id",
"created_timestamp": "2024-05-14T12:51:33.283695187Z",
"modified_by": "api-client-id",
"modified_timestamp": "2024-05-14T12:51:33.283695187Z"
}
]
}
Delete Static Host Group
Delete static host group.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Host Group ID | Jinja-templated text containing the ID of the static host group. | Required |
Output
JSON containing the following items:
{
"errors": null,
"has_error": false,
"meta": {
"query_time": 0.450510996,
"trace_id": "trace-id"
},
"error": null,
"resources": [
"id"
]
}
Manage Static Host Group
Manage static host group
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Host Group ID | Jinja-templated text containing the ID of the static host group. | Required |
| Host Group Body | Jinja-templated JSON containing the body of the static host group. Example { "name": "filter", "value": "(device_id: ['e139xxxxxxxx5885','389axxxxxxxx5e80'])"} | Required |
| Action Type | Select action. | Required |
Output
JSON containing the following items:
{
"errors": null,
"has_error": false,
"meta": {
"query_time": 0.450510996,
"trace_id": "trace-id"
},
"error": null,
"resources": [
{
"id": "id",
"group_type": "static",
"name": "Test Group 140001",
"description": "Test Group 140002 description",
"created_by": "api-client-id",
"created_timestamp": "2024-05-14T12:51:33.283695187Z",
"modified_by": "api-client-id",
"modified_timestamp": "2024-05-14T12:51:33.283695187Z"
}
]
}
Get Static Host Group
Get static host group
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Host Group ID | Jinja-templated text containing the ID of the static host group. | Required |
Output
JSON containing the following items:
{
"errors": null,
"has_error": false,
"meta": {
"query_time": 0.450510996,
"trace_id": "trace-id"
},
"error": null,
"resources": [
{
"id": "id",
"group_type": "static",
"name": "Test Group 140001",
"description": "Test Group 140002 description",
"created_by": "api-client-id",
"created_timestamp": "2024-05-14T12:51:33.283695187Z",
"modified_by": "api-client-id",
"modified_timestamp": "2024-05-14T12:51:33.283695187Z"
}
]
}
Search Static Host Group
Search static host group
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| FQL Filter | Jinja-templated text containing the fql filter. Example "group_type:'static'" | Optional |
| Limit | The maximum number of host group to return in this response.(Maximum 500) | Optional |
Output
JSON containing the following items:
{
"errors": null,
"has_error": false,
"meta": {
"query_time": 0.450510996,
"trace_id": id
},
"error": null,
"resources": [
{
"id": "id1",
"group_type": "static",
"name": "Test Group 140002",
"description": "Test Group 140001 description",
"created_by": "api-client-id",
"created_timestamp": "2024-05-14T12:51:33.283695187Z",
"modified_by": "api-client-id",
"modified_timestamp": "2024-05-14T12:51:33.283695187Z"
},
{
"id": "id2",
"group_type": "static",
"name": "Test Group 140002",
"description": "Test Group 140002 description",
"created_by": "api-client-id",
"created_timestamp": "2024-05-14T12:51:33.283695187Z",
"modified_by": "api-client-id",
"modified_timestamp": "2024-05-14T12:51:33.283695187Z"
}
]
}
Get Host ID in Host Group
Get the member host ID in static host group
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Host Group ID | Jinja-templated text containing the ID of the static host group. | Required |
| Limit | The maximum number of host group to return in this response.(Maximum 500) | Optional |
Output
JSON containing the following items:
{
"errors": [],
"has_error": false,
"meta": {
"query_time": 0.010058804,
"pagination": {
"offset": 5,
"limit": 5,
"total": 79042
},
"trace_id": "trace-id"
},
"error": null,
"resources": [
"id1",
"id2",
"id3",
"id4",
"id5"
]
}
Get Host Details in Host Group
Get the details of member host in static host group
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Host Group ID | Jinja-templated text containing the ID of the static host group. | Required |
| Limit | The maximum number of host group to return in this response.(Maximum 500) | Optional |
Output
JSON containing the following items:
{
"errors": null,
"has_error": false,
"meta": {
"query_time": 0.017531341,
"pagination": {
"offset": 3,
"limit": 3,
"total": 79040
},
"trace_id": "trace-id"
},
"error": null,
"resources": [
{
"device_id": "device-id",
"cid": "cid",
"agent_load_flags": "1",
"agent_local_time": "2024-05-14T01:40:01.040Z",
"agent_version": "7.11.18110.0",
"bios_manufacturer": "American.",
"bios_version": "5.6.5",
"build_number": "17763",
"config_id_base": "65994753",
"config_id_build": "18110",
"config_id_platform": "3",
"cpu_signature": "198265",
"cpu_vendor": "0",
"external_ip": "198.175.154.194",
"mac_address": "00-04-5f-a8-f8-d7",
"hostname": "108PERKINELMER",
"first_seen": "2022-08-26T19:50:38Z",
"last_login_timestamp": "2024-05-08T05:39:55Z",
"last_login_user": "TE1K1579",
"last_login_user_sid": "S-1-5-21-1547161642-484763869-725345543-921865",
"last_seen": "2024-05-14T06:12:20Z",
"local_ip": "64.1.1.2",
"machine_domain": "us.tycoelectronics.com",
"major_version": "10",
"minor_version": "0",
"os_version": "Windows 10",
"os_build": "17763",
"ou": [
"East",
"NCS",
"Workstations"
],
"platform_id": "0",
"platform_name": "Windows",
"policies": [
{
"policy_type": "prevention",
"policy_id": "policy-id",
"applied": true,
"settings_hash": "7c5959eb",
"assigned_date": "2024-01-05T16:30:17.751663753Z",
"applied_date": "2024-01-05T16:30:34.892376096Z",
"rule_groups": [
"rule-group-id1",
"rule-group-id2"
]
}
],
"reduced_functionality_mode": "no",
"device_policies": {
"prevention": {
"policy_type": "prevention",
"policy_id": "ploicy-id",
"applied": true,
"settings_hash": "7c5959eb",
"assigned_date": "2024-01-05T16:30:17.751663753Z",
"applied_date": "2024-01-05T16:30:34.892376096Z",
"rule_groups": [
"rule-group-id1",
"rule-group-id2"
]
}
},
"groups": [
"group-id1",
"group-id2"
],
"group_hash": "group hash",
"product_type": "1",
"product_type_desc": "Workstation",
"provision_status": "Provisioned",
"serial_number": "To be filled by O.E.M.",
"kernel_version": "10.0.17763.2114",
"os_product_name": "Windows 10 Enterprise LTSC 2019",
"chassis_type": "3",
"chassis_type_desc": "Desktop",
"last_reboot": "2024-05-14T05:39:37Z",
"connection_ip": "163.241.218.218",
"default_gateway_ip": "163.241.218.1",
"connection_mac_address": "00-04-5f-a8-f8-d6"
}
]
}
Get Falcon Spotlight Vulnerabilities
Provide one or more vulnerability IDs to get detailed info about those vulnerabilities. Maximum number of IDs is 400.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Vulnerability ID | Jinja-templated text containing the comma separated Vulnerabilities ID. Example 'abc,xyz' | Required |
Output
JSON containing the following items:
{
"resources": [
{
"id": "a2eftestba9fb",
"cid": "674testfa",
"aid": "a2testa23",
"vulnerability_id": "test",
"data_providers": [
{
"provider": "Falcon sensor"
}
],
"created_timestamp": "2024-07-10T23:06:39Z",
"updated_timestamp": "2024-08-02T04:24:01Z",
"status": "open",
"apps": [
{
"product_name_version": "Windows Server",
"product_name_normalized": "Windows Server",
"sub_status": "open",
"remediation": {
"ids": [
"8test4"
]
},
"evaluation_logic": {
"id": "a6testb2"
}
}
],
"suppression_info": {
"is_suppressed": false
},
"confidence": "confirmed",
"cve": {
"id": "test"
}
}]
"error": null,
"has_error": false
}
Get Falcon Spotlight Vulnerabilities Evaluation by Timestamp
Retrieve evaluation logic IDs for Windows and macOS-based products related to a vulnerability by timestamp.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Filter | Filter vulnerabilities evaluations. Filter fields include: aid, created_timestamp, updated_timestamp | Required |
| Limit | Maximum number of items to return. Default is 100. | Optional |
Output
JSON containing the following items:
{
"resources": [ "033cf8e", "123456789", "98765432"],
"error": null,
"has_error": false
}
List Falcon Spotlight Vulnerabilities
Retrieve vulnerabilities ids in your environment by providing an FQL filter
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Filter | Filter vulnerabilities. Filter fields include: aid, apps.remediation.ids, closed_timestamp, created_timestamp, cve.exploit_status, cve.exprt_rating, cve.id, cve.is_cisa_kev, cve.remediation_level, cve.severity, cve.types, host_info.asset.criticality, host_info.managed_by, host_info.groups, host_info.internet_exposure, host_info.platform_name, host_info.product_type_desc, host_info.tags, host_info.third_party_asset_ids, last_seen_within, status, suppression_info.is_suppressed, suppression_info.reason, updated_timestamp, vulnerability_id | Required |
| Limit | Maximum number of items to return. Default is 100. | Optional |
Output
JSON containing the following items:
{
"resources": [ "033cf8e", "123456789", "98765432"],
"error": null,
"has_error": false
}
List Combine Falcon Spotlight Vulnerability Entities
Get complete vulnerability instance data, including remediation, host, and CVE details.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Filter | Filter vulnerabilities. Filter fields include: aid, apps.remediation.ids, closed_timestamp, created_timestamp, cve.exploit_status, cve.exprt_rating, cve.id, cve.is_cisa_kev, cve.remediation_level, cve.severity, cve.types, data_providers.ports, data_providers.provider, data_providers.rating, data_providers.scan_time, data_providers.scanner_id, host_info.asset_criticality, host_info.groups, host_info.internet_exposure, host_info.managed_by, host_info.platform_name, host_info.product_type_desc, host_info.tags, host_info.third_party_asset_ids, last_seen_within, status, suppression_info.is_suppressed, suppression_info.reason, updated_timestamp, vulnerability_id | Required |
| Facet | Type of data to be returned for each vulnerability entity. The facet filter allows you to limit the response to just the information you want. For example, the CVE description and severity are the same for every instance of that CVE, and you might prefer to cache a copy of that information rather than have it included. Possible values: host_info, remediation, cve, evaluation_logic Note: Requests that do not include the cve or evaluation_logic facets still return the CVE and evaluation_logic IDs in the response. | Optional |
| Limit | Maximum number of items to return. Default is 100. | Optional |
Output
JSON containing the following items:
{
"resources": [
{
"id": "a2eftestba9fb",
"cid": "674testfa",
"aid": "a2testa23",
"vulnerability_id": "test",
"data_providers": [
{
"provider": "Falcon sensor"
}
],
"created_timestamp": "2024-07-10T23:06:39Z",
"updated_timestamp": "2024-08-02T04:24:01Z",
"status": "open",
"apps": [
{
"product_name_version": "Windows Server",
"product_name_normalized": "Windows Server",
"sub_status": "open",
"remediation": {
"ids": [
"8test4"
]
},
"evaluation_logic": {
"id": "a6testb2"
}
}
],
"suppression_info": {
"is_suppressed": false
},
"confidence": "confirmed",
"cve": {
"id": "test"
}
}]
"error": null,
"has_error": false
}
Get Device Details Using Child CID
Get device details action allows you to view details for specific devices given one or more device IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Device ID | Jinja-templated text containing the device id | Required |
| Member CID | Jinja-templated text containing the member cid | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Get Process Details Using Child CID
Retrieve the details of a process that is running or that previously ran, given one or more process IDs.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Process ID | Jinja-templated text containing the process id. Generally it is of the format pid:Process_Id:Sensor_id | Required |
| Member CID | Jinja-templated text containing the member cid | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Indicator search
list of hosts in your environment that have been associated with an indicator.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Indicator Value | Jinja-templated text containing the value you are searching for. | Required |
| Indicator type | Jinja-templated text containing the type of indicator you are searching for. Type can be one of the following: domain, md5, sha256 | Required |
| Limit | The maximum number of detections to return in this response. | Optional |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Get List of Applications
Get a list of applications that meet defined criteria
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Filter | Jinja templated text containing the filter. | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Execute an on-demand workflow
Provide either a workflow definition ID or a workflow name to trigger an on-demand workflow.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Body | Jinja templated text containing the body. Example: {"Name": "Host assessment"} | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Get Execution Result
Get the execution results using this endpoint
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Workflow Execution ID | Workflow Execution Id. Example: a1e652xxxxxxxxxxxxxxxxxxxxc7935e | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Configure the Policy Settings
Configure the policy settings.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Policy Body | Jinja templated text containing the policy body. Example: { "resources": [ { "id": "94fa45cf5d6640fea4137ccdd82ed857" , "settings": { "enforcement_mode": "MONITOR_ENFORCE" , "end_user_notification": "NOTIFY_USER" , "classes": [ { "id": "AUDIO_VIDEO" , "action": "BLOCK_ALL" , "exceptions": [ { "combined_id": "1133_2092_7A4F8BD0" , "action": "FULL_ACCESS" } ] }, { "id": "MASS_STORAGE" , "action": "BLOCK_ALL" , "exceptions": [ { "vendor_id": "59f" , "vendor_name": "LaCie" , "product_id": "10c4" , "product_name": "HDD" , "action": "BLOCK_EXECUTE" , "description": "Block temporarily" , "expiration_time": "2022-07-21T18:20:16Z" }, { "vendor_id_decimal": "3010" , "vendor_name": "Seagate", "action": "FULL_ACCESS" } ] } ] } } ] } | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Create query job
Create a query job and execute the search to run in the background. Required permission NGSIEM: Write
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Repository | Jinja templated text containing the repository to run the query against. Available repository values: search-all, forensics_view, falcon_for_it_view, third-party, investigate_view | Required |
| Body | Jinja templated JSON containing the job body. Example: {"queryString":"aid=abc123", "start":"1d", "end":"now"}. Note queryString is a mandatory field. | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Get query job
Monitor the progress of a running query job and get back partial results as they become available. Required permission NGSIEM: Read
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Repository | Jinja templated text containing the repository to run the query against. Available repository values: search-all, forensics_view, falcon_for_it_view, third-party, investigate_view | Required |
| Job Id | Jinja templated text containing the job ID. | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Stop query job
Used to stop an in-progress job. Required permission NGSIEM: Write
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Repository | Jinja templated text containing the repository to run the query against. Available repository values: search-all, forensics_view, falcon_for_it_view, third-party, investigate_view | Required |
| Job Id | Jinja templated text containing the job ID. | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Release Notes
v2.3.11-update the existing'Get query job'action to incorporate loop search to check if the action has returned valuesv2.3.10- Added 8 new actionsIndicator search,Get List of Applications,Execute an on-demand workflow,Get Execution Result,Configure the Policy Settings,Create query job,Get query jobandStop query job.v2.3.9- Deprecated existingSearch Alertsand created new actionSearch Alertsin accordance to the upgraded APIs of Crowdstrikev2.3.8- Added 2 new actionsGet Process Details Using Child CIDandGet Device Details Using Child CID.v2.3.7- Added optionalAssignee Namefield inModify Alertaction.v2.3.4- Added optionalTagsfield inModify Alertaction.v2.3.1- Added 4 new action:Get Falcon Spotlight Vulnerabilities,Get Falcon Spotlight Vulnerabilities Evaluation by Timestamp,List Falcon Spotlight VulnerabilitiesandList Combine Falcon Spotlight Vulnerability Entitiesv2.2.12- Bug Fix - Issue with Assignee field inModify Alertsv2.2.11- Bug Fix - Host ID not working inGet Host ID in Host GroupandGet Host Details in Host Group.v2.2.9- Added 8 new action:Create Static Host Group,Modify Static Host Group,Delete Static Host Group,Manage Static Host Group,Get Static Host Group,Search Static Host Group,Get Host ID in Host GroupandGet Host Details in Host Group.v2.2.6- Bug Fix forRTR Command: Single Hostv2.2.4- Bug Fix - Issue with Default limit inSearch IOCsfixed.v2.2.3- Added 3 new action:Search Alerts,Get Alert DetailsandModify Alertwhich support v2 API inplace of 3 deprecated actionsSearch Detection,Get Detection DetailsandModify Detectionrespectively.v2.1.8- Added support for pid which starts aspid:12341234inGet Process Detailaction.v2.1.0- Added 1 new action:Run GraphQL Query.v2.0.0- Updated architecture to support IO via filesystemv1.2.2- Bug fix - Made severity field required in getCreate Custom IOCaction.v1.2.1- Bug fix - Fix error message to show the original error/warnings from crowdstrike.
Updated 4 months ago