Introduction
The DevoSOAR™ platform is an integrated automation solution for security operations, which helps cyber analysts reduce investigation and threat detection times by easily capturing and automating the expertise, context, and processes specific to their IT environment.
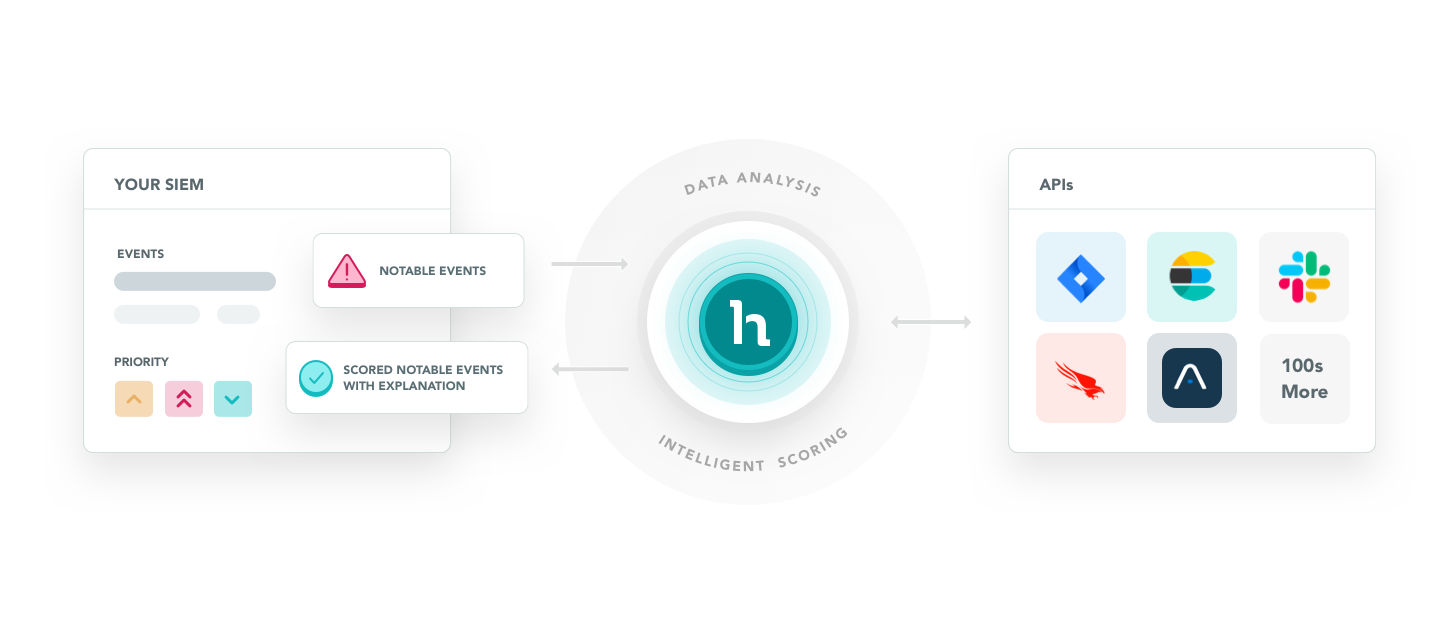
DevoSOAR takes event data ingested from your security information and event management (SIEM) environment and applies intelligent process automation to identify and score events according to their potential severity. After the process flow is designed as a playbook in DevoSOAR, the results become available for intelligent threat detection on an ongoing basis.
Beginning with notable events from your SIEM environment, DevoSOAR processes the data, leveraging the analyst's expertise along with information from web security services to produce a score for each event. The scored events that meet a severity threshold are then provided back to your SIEM system along with an explanation that lets you focus on the events that are most likely to require attention.
Before you begin, let's look at the building blocks of the DevoSOAR product.
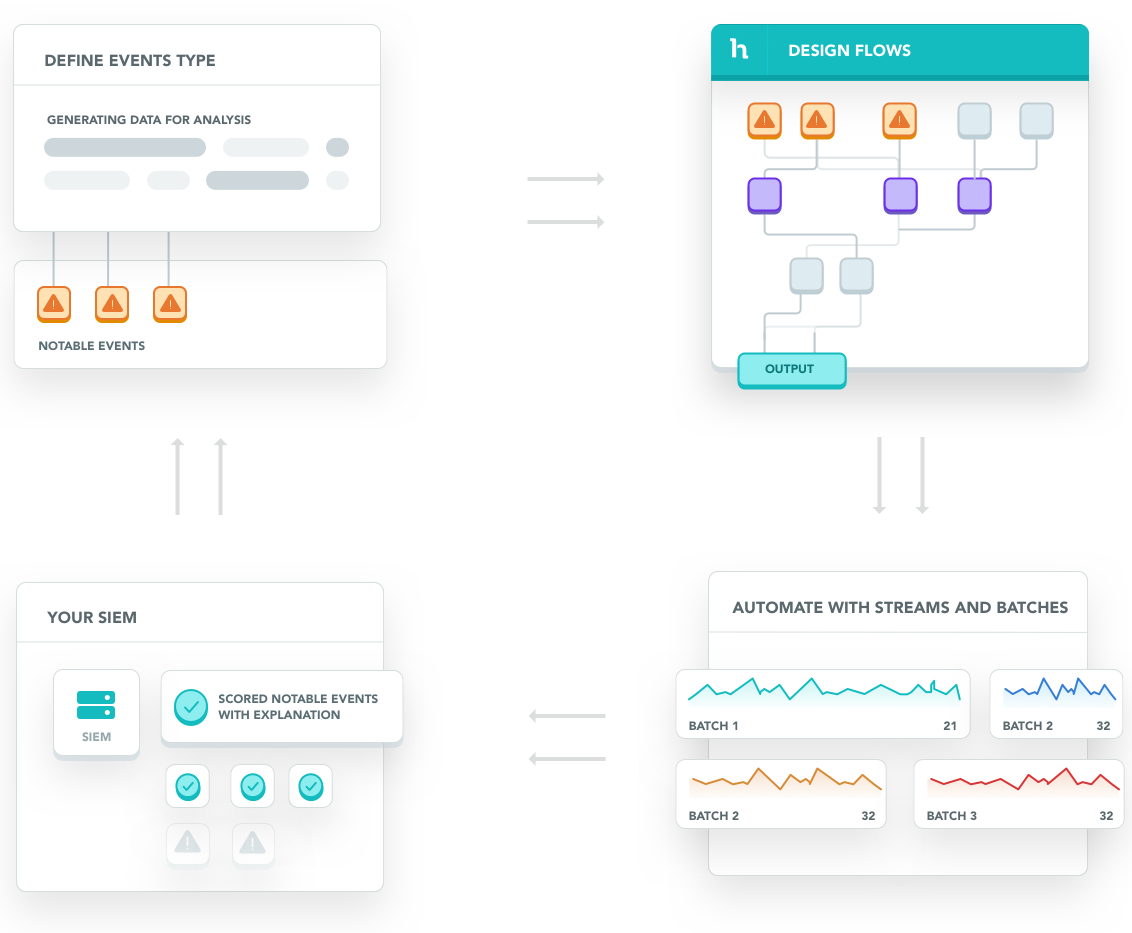
Connections allow you to ingest data into DevoSOAR from your security information and event management (SIEM) environment.
Event types are the queries that get specific events from your connections and yield the results that will pipe into the DevoSOAR analysis. The queries are the same native queries that you would run on your SIEM.
Playbooks (formerly called flows) are the graphical representations of the logic that the security analyst goes through to make decisions about events. Playbook execution ranks security events such that the critical events at the top. Playbooks allow you to take multiple inputs and apply data reduction and advanced correlation techniques to generate a single score or ranking as the output for each event.
Streams allow you to automate the analysis logic codified in the playbooks and apply it to upcoming events on a fixed interval, creating batches of results. You can set up streams to run at a set interval (such as every 30 minutes), and apply a playbook to each. Within each stream, you can drill down to see why alerts were scored in a particular way, and what portions of the playbook contributed to the scoring.
Destinations represent third-party tools to which you can forward the scored events and associated explanations. A destination can be your SIEM, ticketing system, or any other third-party tool that is compatible with your workflow.
Updated 7 months ago