Microsoft Graph
Version: 3.14.4
Microsoft Graph is the gateway to data and intelligence in Microsoft 365. Microsoft Graph provides a unified programmability model that you can use to take advantage of the tremendous amount of data in Office 365, Enterprise Mobility + Security, and Windows 10.
Connect Microsoft Graph with LogicHub
- Navigate to Automations > Integrations.
- Search for Microsoft Graph.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- Tenant ID: Tenant ID of the app created in Azure Active Directory.
- Client ID: Client ID of the app created in Azure Active Directory.
- Client Secret: Client secret of the app created in Azure Active Directory.
- After you've entered all the details, click Connect.
Permission Notes
- For Some actions (Example: Get managed device by MAC address), An admin user needs to grant admin consent to the 'DeviceManagementManagedDevices.Read.All' and 'DeviceManagementManagedDevices. ReadWrite.All' permissions. Applications are authorized to call managed device data when they are granted permissions by an admin user as part of the consent process ("Grant Admin consent for Active_Directory").
- Some actions need work or school account.
- Application Permissions (if available) will be applied as LogicHub uses OAuth 2.0 client credentials grant method. For more information click here. Reference image:
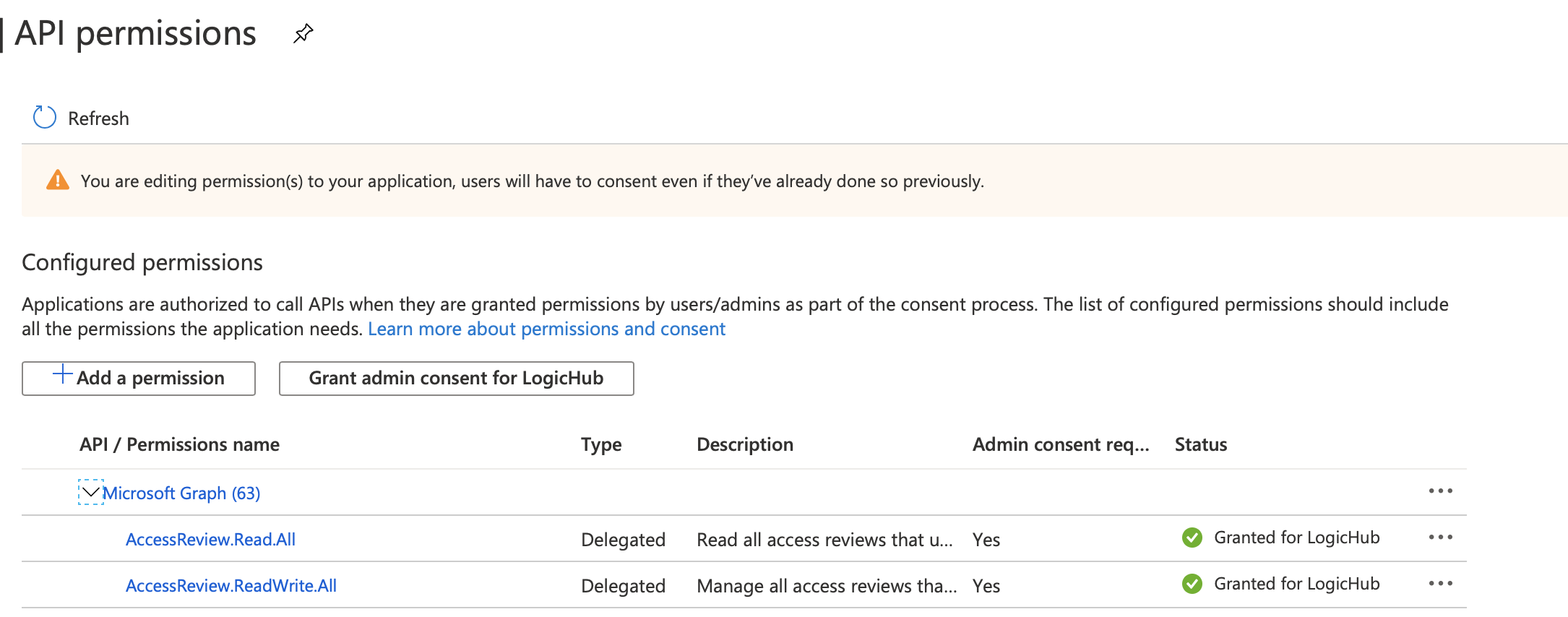
Actions for Microsoft Graph
List Users
Users are the representation of an Azure Active Directory (Azure AD) user account. This action retrieves a list of user objects.
Permission Required(Application): User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Select Query | Column name from parent table containing the select query to filters properties (Default is no filter). Example 'displayName,givenName' | Optional |
Output
Return a list of JSON objects, each of which represents a user.
Figure 1
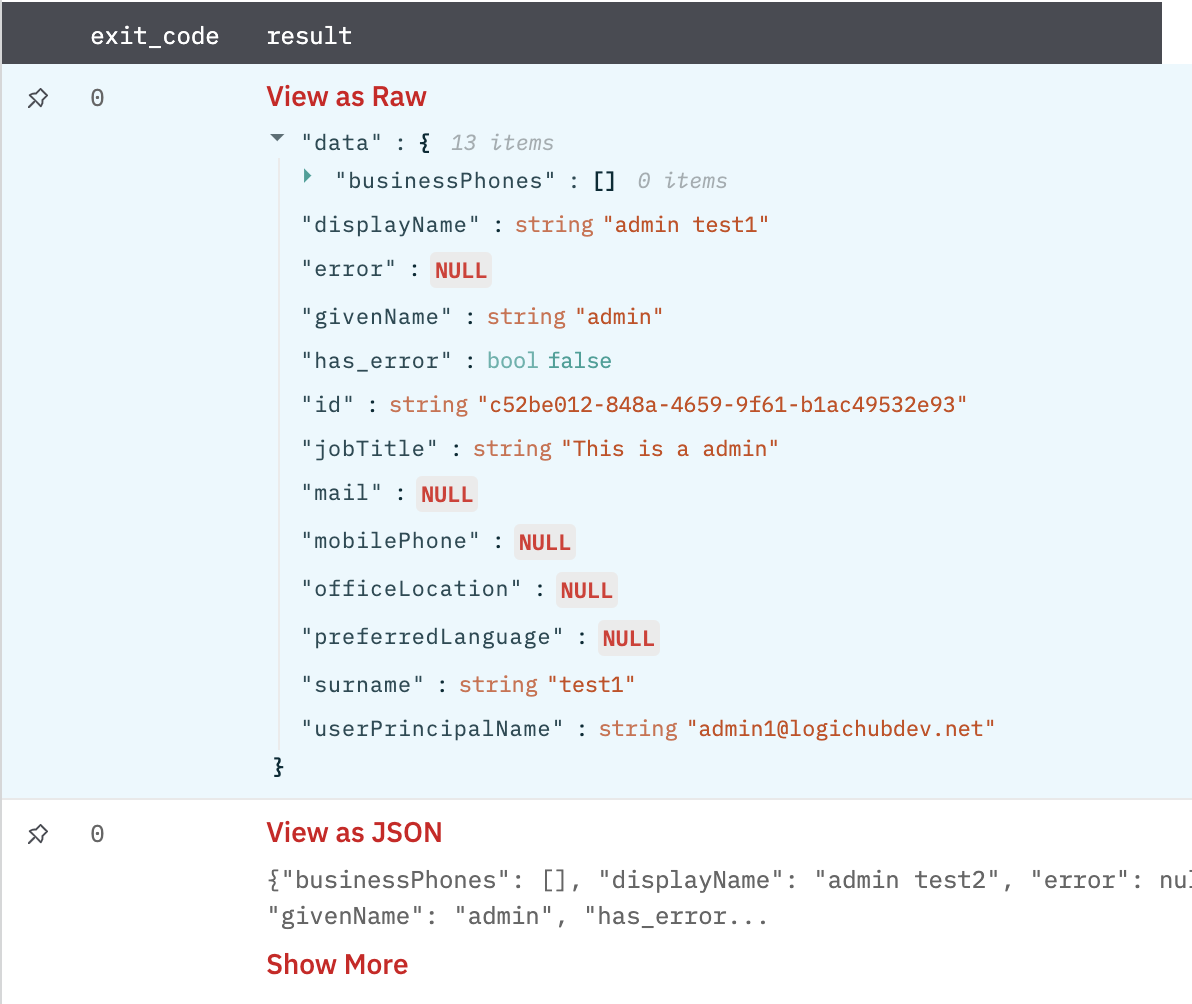
Fig 1
Get User
Users are the representation of an Azure Active Directory (Azure AD) user account. This action retrieves the properties and relationships of the user object.
Permission Required(Application): User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
| Select Query | Column name from parent table containing the select query to filters properties (Default is no filter). Example 'displayName,givenName' | Optional |
Output
Return the user object in JSON format corresponding to a given user's principal name or user's unique identifier (ID).
Figure 2
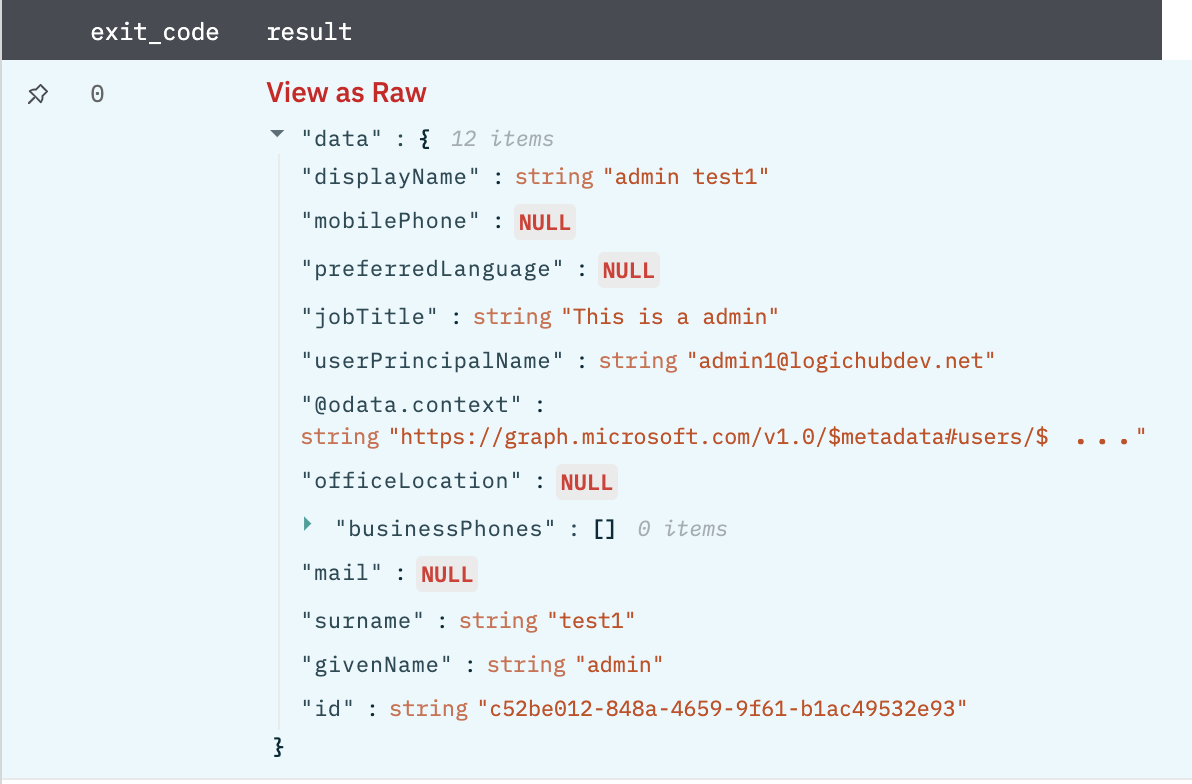
Fig 2
Delete User
Users are the representation of an Azure Active Directory (Azure AD) user account. This action deletes the user.
Permission Required(Application): User.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
Output
Return a JSON with no error on successful deletion as shown in Fig 3.
Figure 3
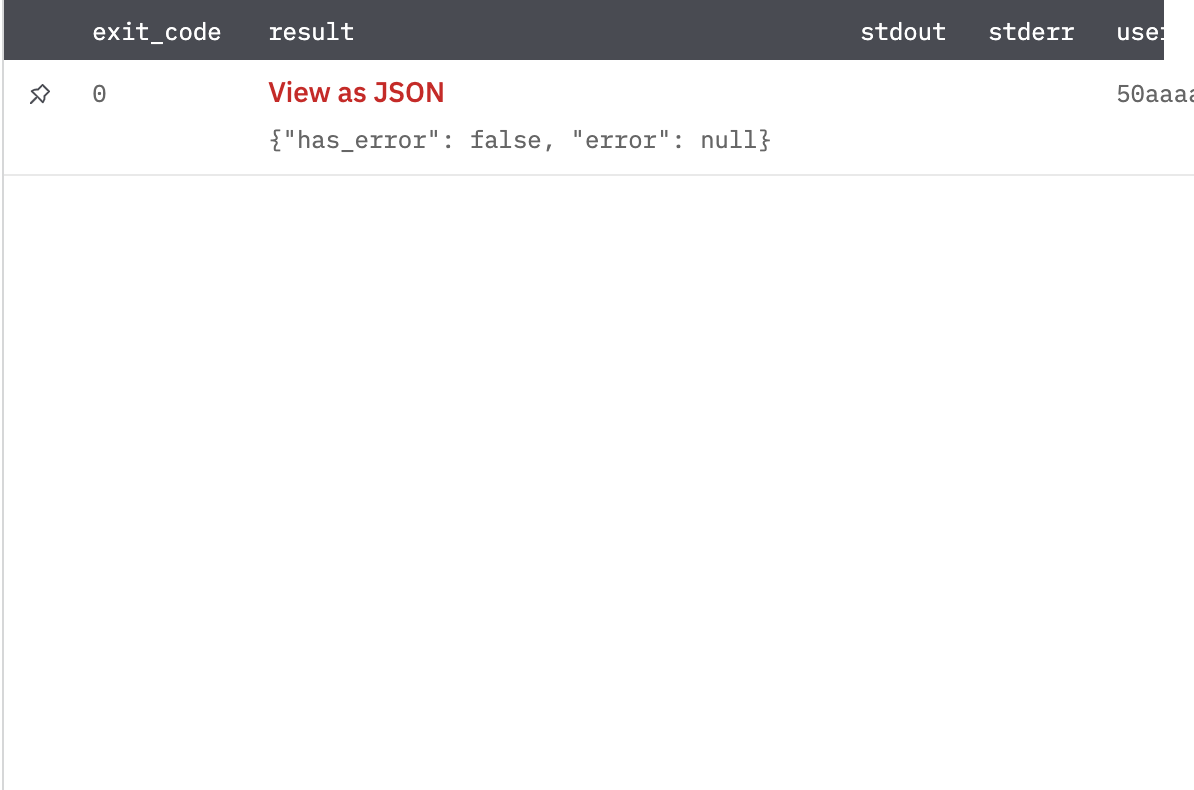
Fig 3
Get User's Manager
Returns the user or contact assigned as the user's manager.
Permission Required(Application): User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
Output
Return the user or contract if the manager exists as shown in Fig 4 else error with the message as shown in Fig 5.
Figure 4
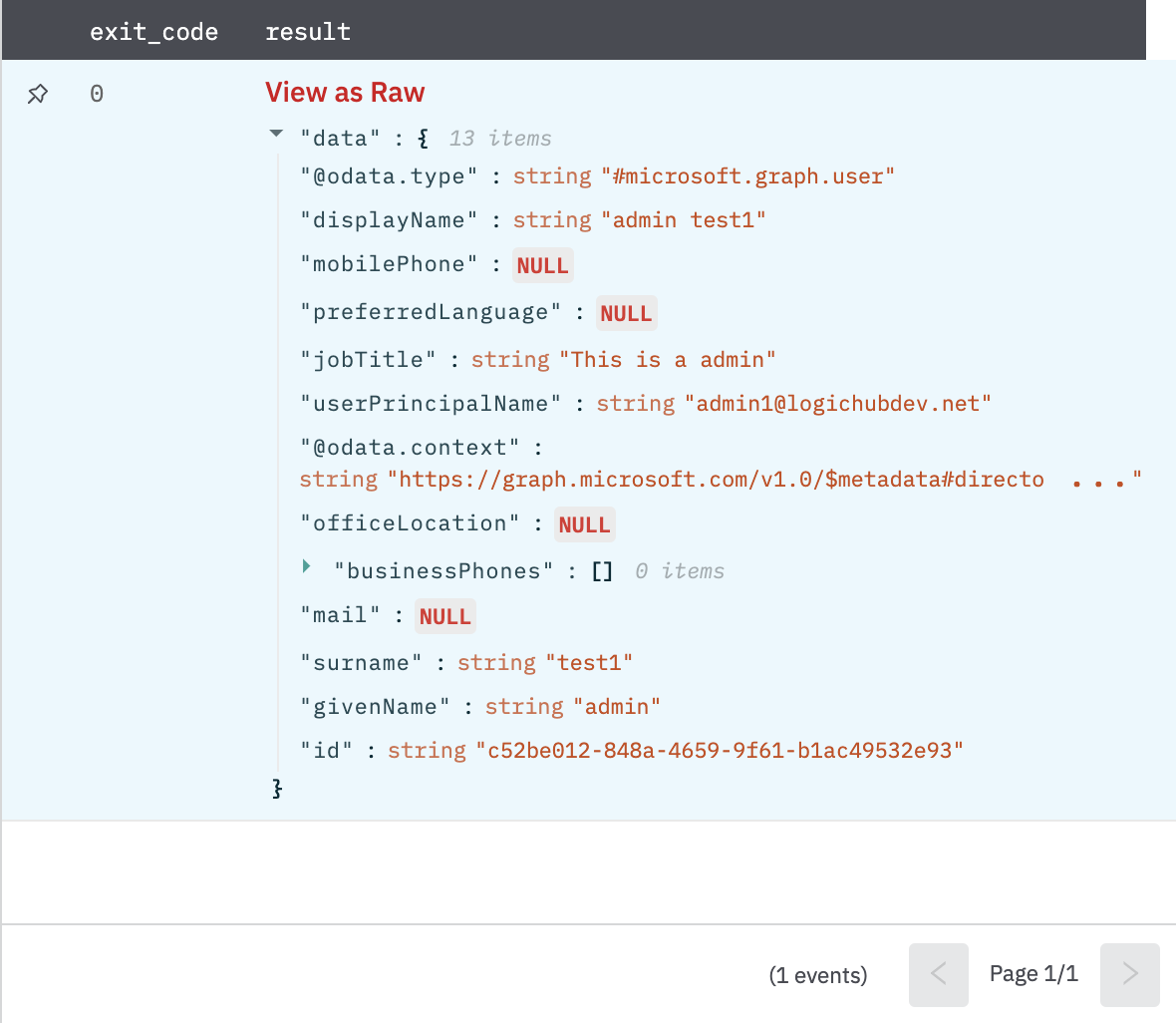
Fig 4
Figure 5
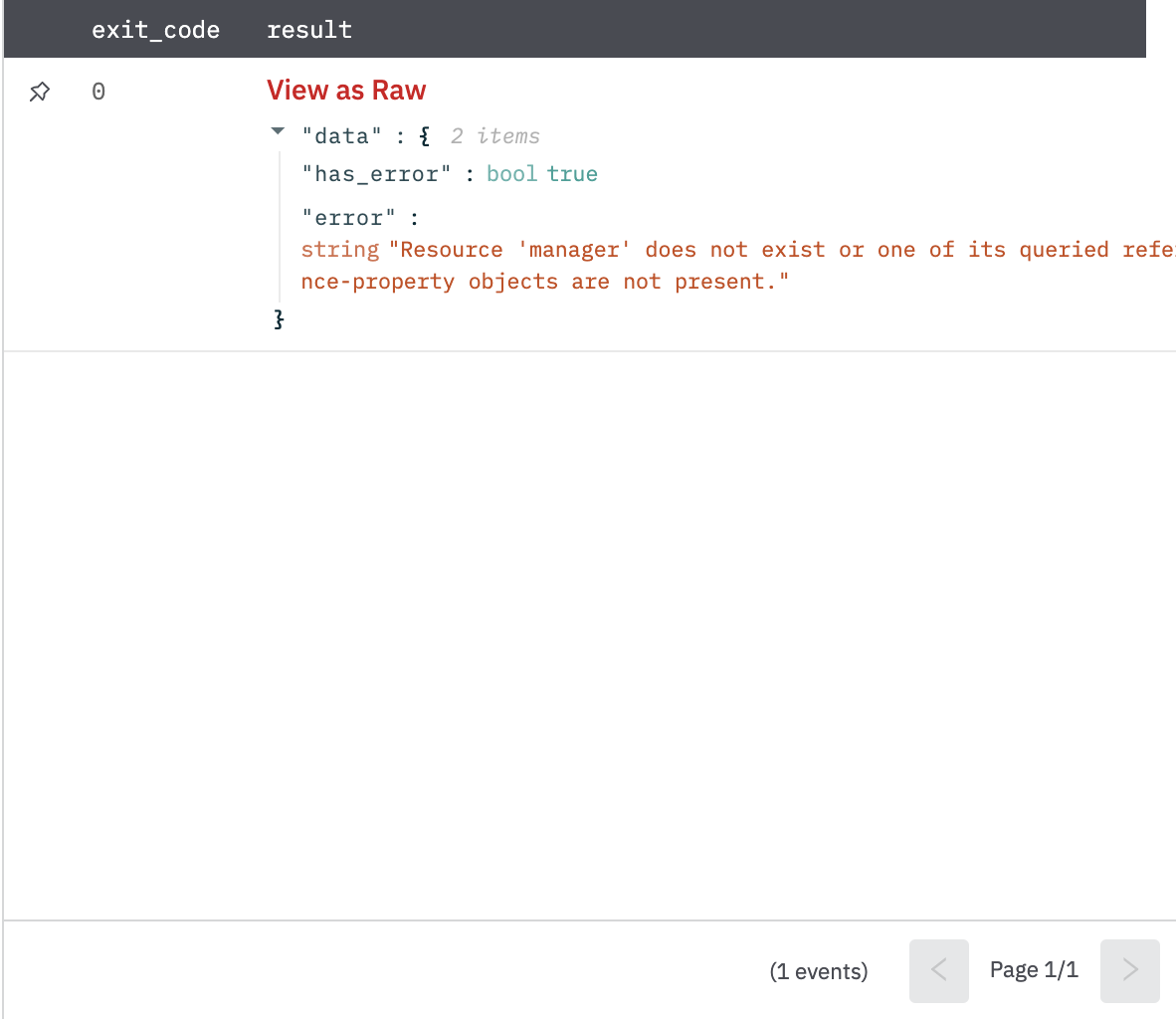
Fig 5
Get User's Direct Reports
Returns the users and contacts for whom this user is assigned as manager.
Permission Required(Application): User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
Output
Return a JSON object whose value field contains the list of users and contacts for whom the given user is assigned as manager.
Figure 6
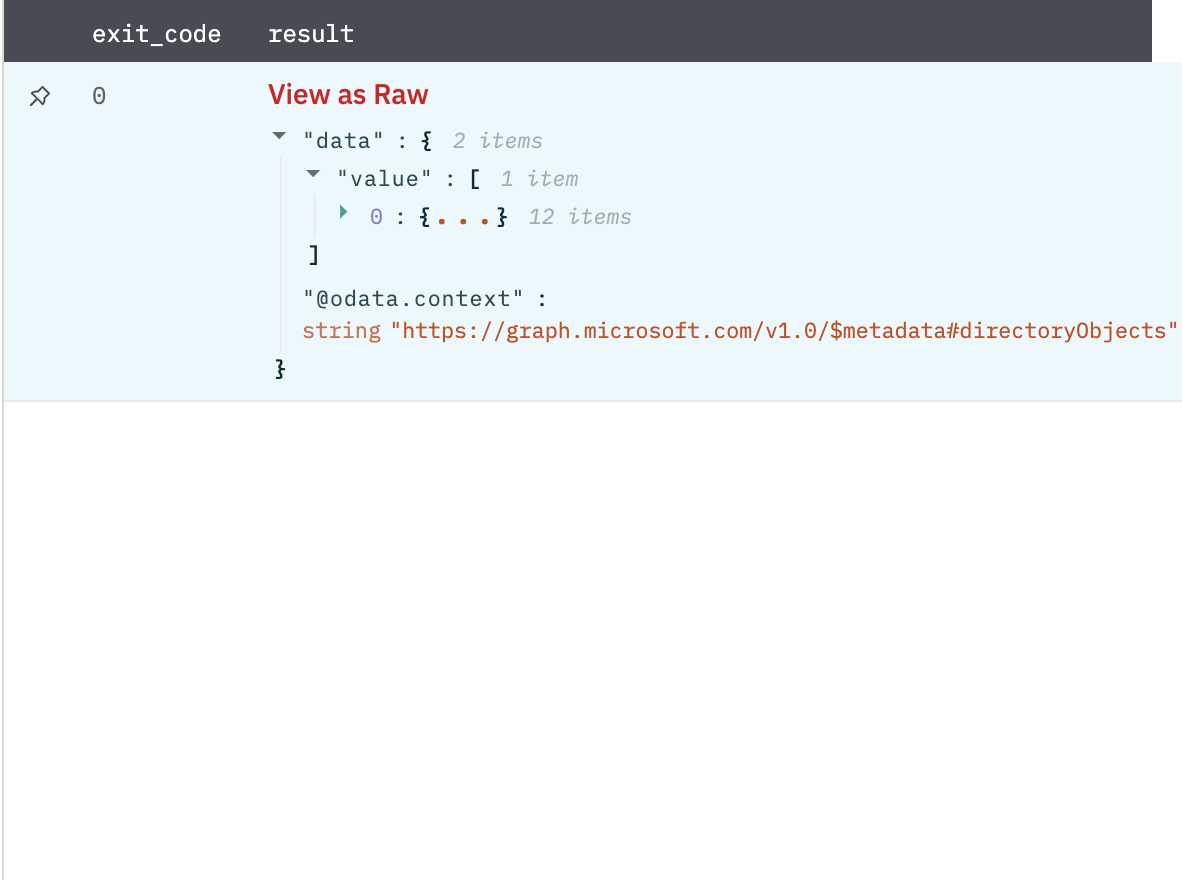
Fig 6
List messages (Deprecated)
Get the messages in the signed-in user's mailbox (including the Deleted Items and Clutter folders).
Permission Required(Application): Mail.ReadBasic.All, Mail.Read, Mail.ReadWrite
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
| Custom OData query | Jinja templated custom OData query to retrieve a list of messages. Refer https://docs.microsoft.com/en-us/graph/query-parameters to construct a valid OData query. Example: $filter=subject eq '{{subject_column}}' and from/emailAddress/address eq '{{sender_email_column}}'&$top=5. (Default is no filter). | Optional |
| Number of messages to be fetched | Number of messages to be fetched (Default 10). | Optional |
Output
Return a list of message objects. The value field in JSON will contain a list of messages. In the below screenshot, there are zero messages corresponding to a given user's principal name or user's unique identifier (ID).
Figure 7
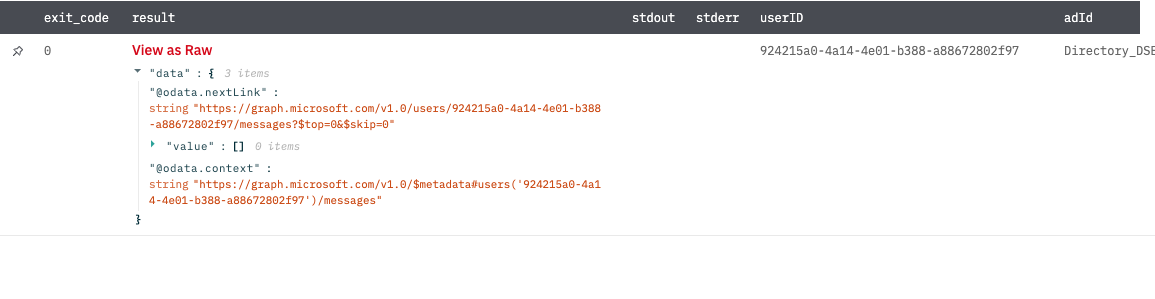
Fig 7
Get Message
Retrieve the properties and relationships of a message object.
Permission Required(Application): Mail.ReadBasic.All, Mail.Read
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Message's unique identifier (ID) | Message's unique identifier (ID). | Required |
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
Output
Return a message object in JSON format corresponding to the given message ID and user's principal name or user's unique identifier (ID).
Delete Message
This action deletes a message.
Permission Required(Application): Mail.ReadWrite
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Message's unique identifier (ID) | Message's unique identifier (ID). | Required |
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
Output
Return a JSON with no error on successful deletion.
Block Messages
Blocks Messages/Mails received from specified email addresses. Sends them to the "Junk Email" folder.
Permission Required(Application): MailboxSettings.ReadWrite
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
| Email addresses to block | Jinja-templated comma-separated email addresses to block receiving an email from. | Required |
| Rule Name | Jinja-templated rule name to assign to the configured rule that blocks messages/emails from specified email addresses. | Required |
Output
Return a JSON with details of the Rule that'll block messages.
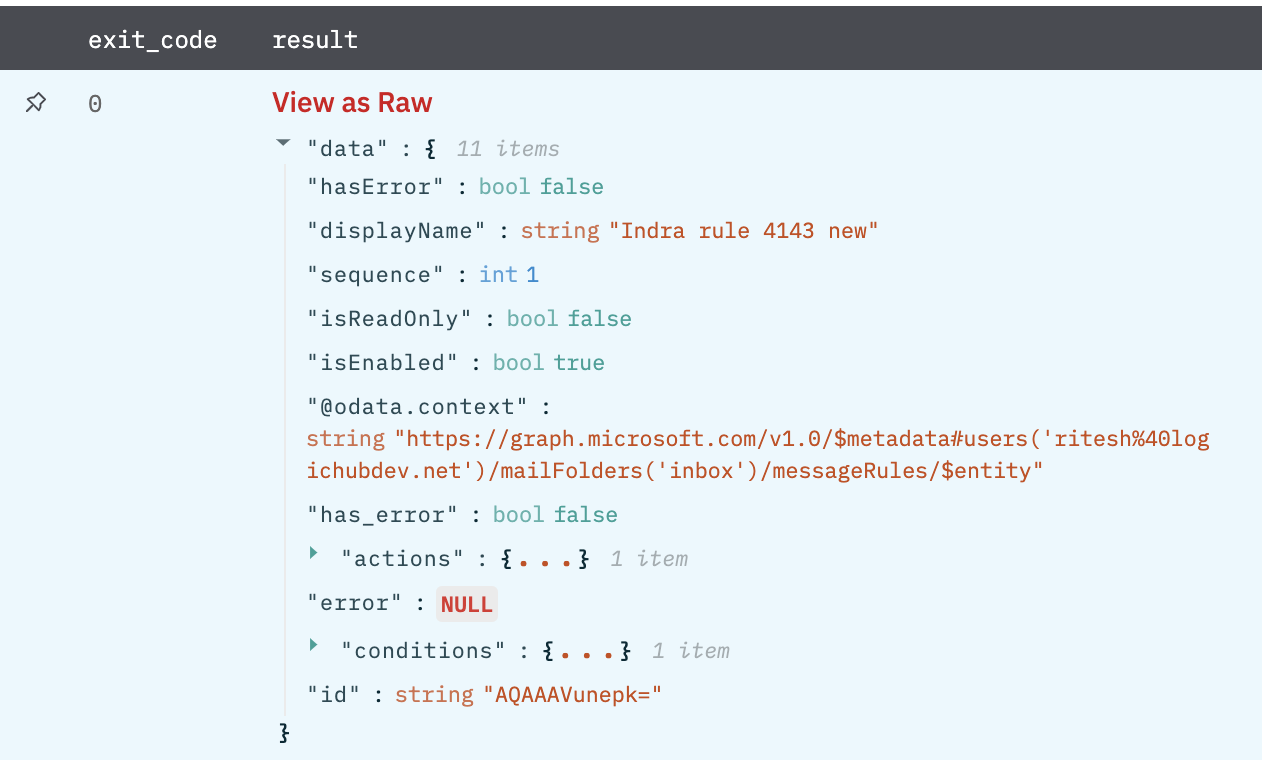
List Security Alerts
This action lists security alerts.
Permission Required(Application): SecurityEvents.Read.All, SecurityEvents.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Jinja Template for Custom OData query | Jinja template for custom OData query to retrieve a list of alerts (Default is no filter). Example: $filter={{property_column}} eq '{{property_value_column}}'&$top=5 . For more OData query parameters click here. | Required |
Output
Return a list of security alerts.
Get Security Alert
This action gets a security alert.
Permission Required(Application): SecurityEvents.Read.All, SecurityEvents.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Microsoft Graph AlertId Column name | Column name from parent table containing Microsoft Graph Alert ID. | Required |
Output
Return a security alert object in a JSON format corresponding to the given alert ID.
Update Security Alert
This action updates the security alert.
Permission Required(Application): SecurityEvents.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Microsoft Graph AlertId Column name | Column name from parent table containing Microsoft Graph Alert ID. | Required |
| Query Template | Query Template in JSON format referencing the inputs table columns by {{column_name}}. | Required |
Output
Return an updated security alert object in JSON format, if the update is successful.
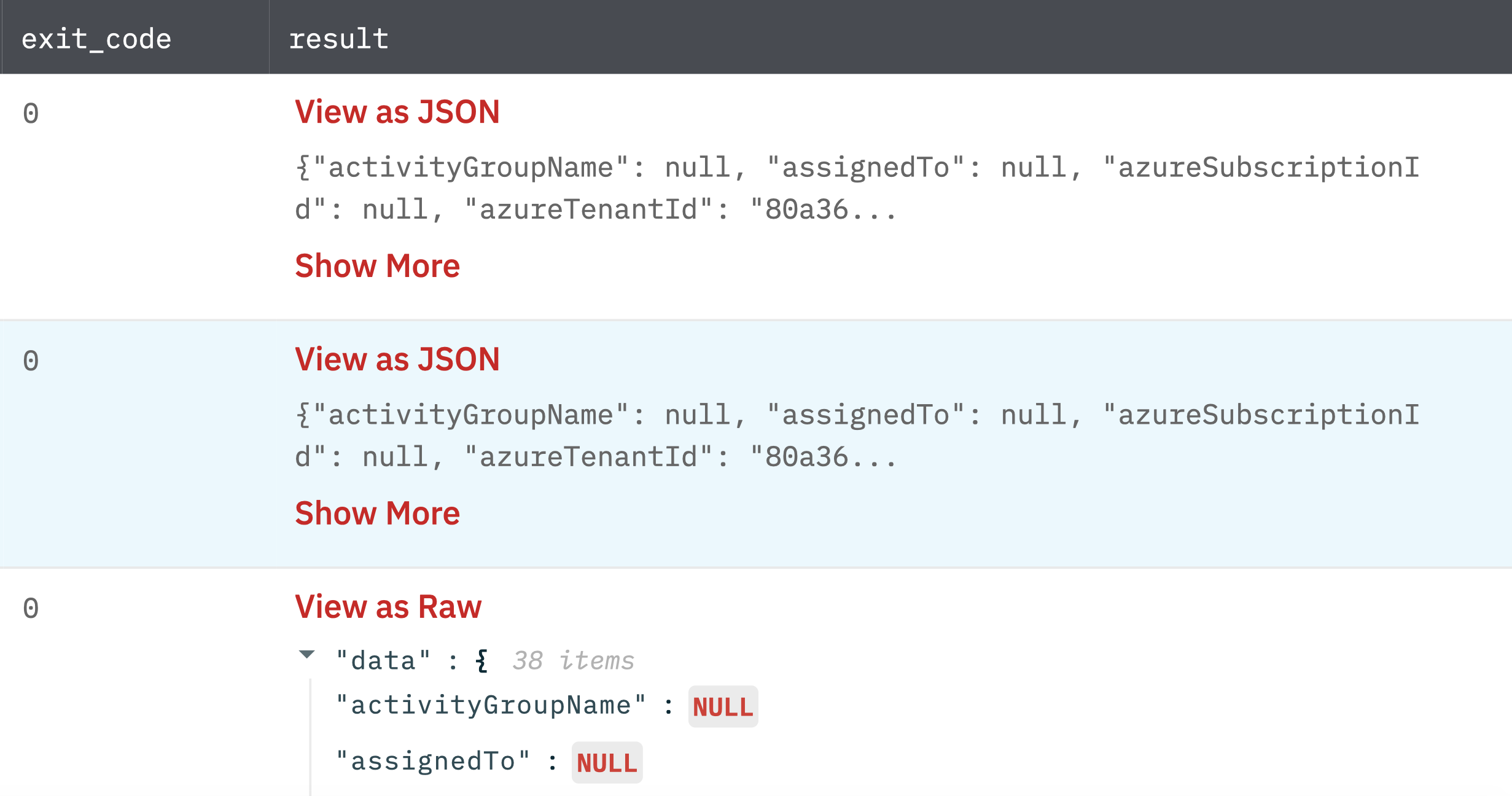
List Directory Audit Logs
Gets the list of audit logs generated by Azure Active Directory.
Permission Required(Application): AuditLog.Read.All and Directory.Read.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Query Filter Template | Jinja-templated query parameter to retrieve just a subset of a collection. Example {{query_column}}. | Optional |
| Top | Sets the number of items in each result. It is used in the pagination of results. | Optional |
Output
Return a list of JSON where each JSON representing the audit log generated by Azure Active Directory.
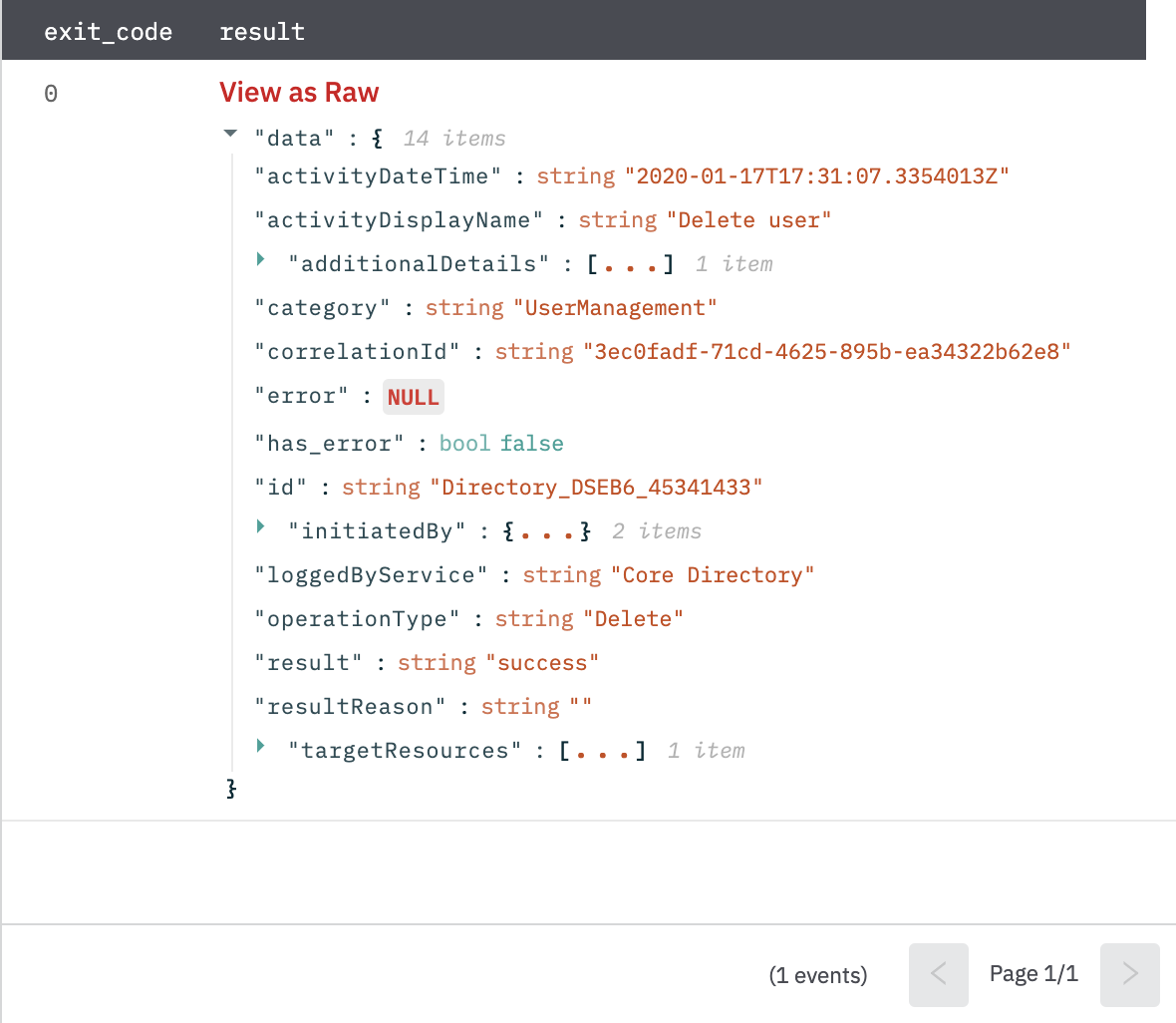
Fig 8
Get Directory Audit Log
Get a specific Azure Active Directory audit log item.
Permission Required(Application): AuditLog.Read.All and Directory.Read.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Microsoft Graph Directory Audit Column name | Column name from parent table containing directory audit log ID. | Required |
Output
Return an audit log object in JSON format corresponding to the given directory audit log ID.
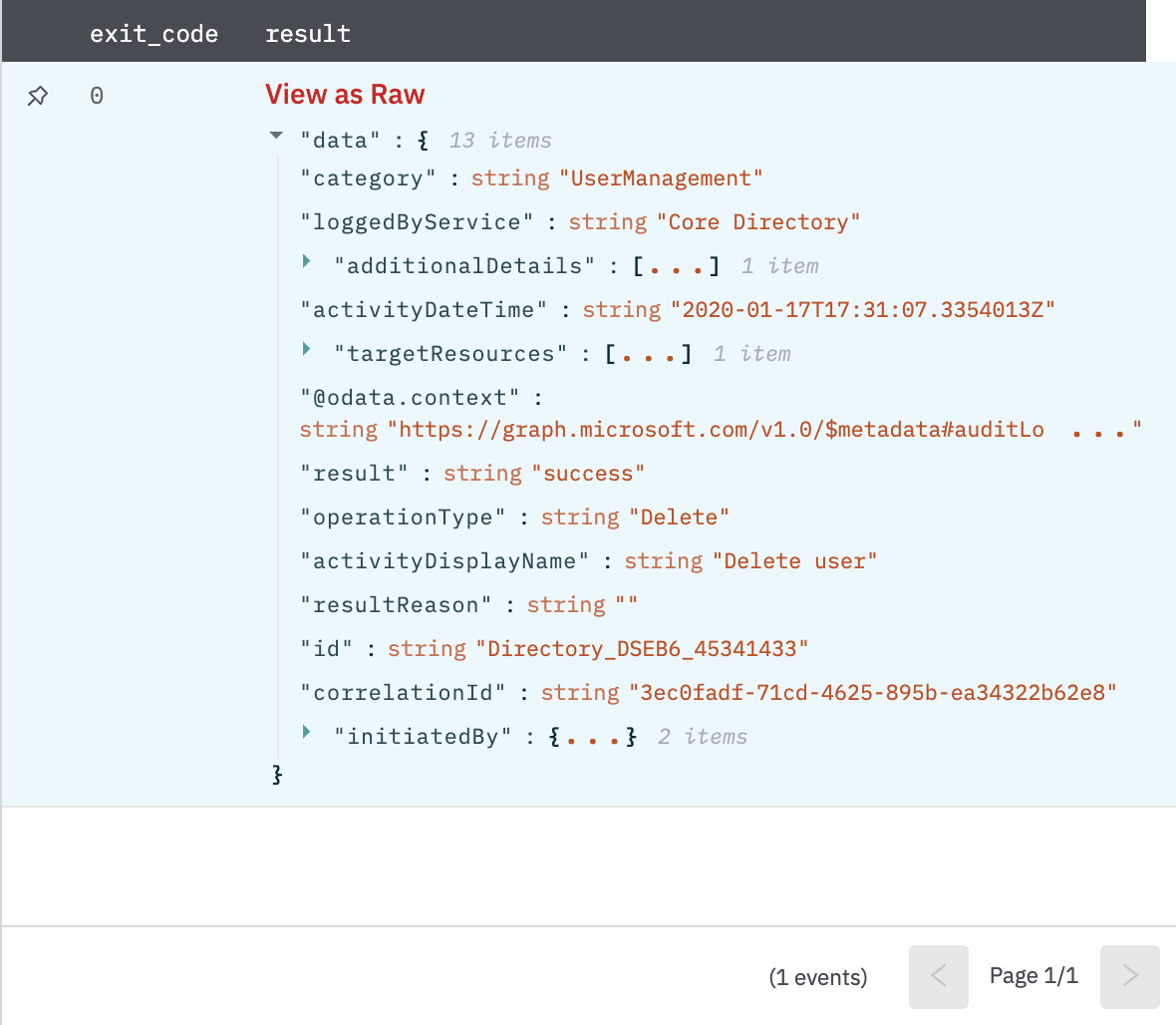
Fig 9
Get Managed Device by MAC Address
Get a managed device (properties and relationships) by MAC address.
Permission Required(Application): DeviceManagementManagedDevices.Read.All, DeviceManagementManagedDevices.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| MAC Address Column name | Column name from parent table containing the MAC address of the managed device. | Required |
Output
Return a managed device object in JSON format corresponding to the given MAC Address.
List Managed Devices
List properties and relationships of the managed devices and supports custom OData query.
Permission Required(Application): DeviceManagementManagedDevices.Read.All, DeviceManagementManagedDevices.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Jinja Template for Custom OData query | Jinja template for custom OData query to retrieve a list of devices (Default is no filter). Example: $filter={{property_column}} eq '{{property_value_column}}'&$top=5. For more OData query parameters click here. | Required |
Output
Return a list of devices.
Send Message
Send message.
Permission Required(Application): Mail.Send
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing user's principal name or user's unique identifier(id). | Required |
| Mail Recipients | Jinja-templated text containing comma separated email ids. | Required |
| Mail Subject | Jinja-templated text string containing the mail subject. | Required |
| Type | Select type of email body (Default is Plain Text) Name", "h-1" | Optional |
| Mail Body | Jinja-templated string containing the mail body. | Required |
| CC on outbound e-mail | Jinja-templated comma separated email ids, which would be added to cc of the email | Optional |
| BCC | Jinja-templated comma separated email ids, which would be added to bcc of the email. Example '[email protected],[email protected]' | Optional |
| Attachment | Jinja-templated string containing one or more file IDs to attachment. (Can be a comma separated string of lhub_file_id values or a json dict in the format of {"<lhub_id>":"<file_name>"}) | Optional |
| Attachment file extension | Jinja-templated text. If no file name is provided, add this extension to attached files. | Optional |
Output
JSON containing following items:
{
"recipients": [
"[email protected]"
],
"date_sent": "2022-05-16 13:19:01 UTC",
"has_error": false,
"error": null,
"msg": "E-mail sent successfully",
"cc": "",
"attachments": []
}
Move Message
Move a message to another folder within the specified user's mailbox. This creates a new copy of the message in the destination folder and removes the original message.
Permission Required(Application): Mail.ReadWrite
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing user's principal name or user's unique identifier(id). | Required |
| Email message ID | Jinja-templated text containing the ID of the message. Example: {{id}} | Required |
| Destination Folder Name | Jinja-templated text containing the name of the destination folder. | Required |
Output
JSON containing following items:
{
"has_error": false,
"result": "Successfully moved e-mails to folder: upper folder",
"error": null
}
List Messages
Get the messages of a user via User ID or Principal Name (including the Deleted Items and Clutter folders).
Permission Required(Application): Mail.ReadBasic.All, Mail.Read, Mail.ReadWrite
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing user's principal name or user's unique identifier(id). | Required |
| Mailbox Folder | Jinja-templated Path & name of the folder from which to pull email messages (typically Inbox) | Optional |
| Query Filter Template | Jinja-templated query parameter to retrieve just a subset of a collection. Example {{query_column}} | Optional |
| Mark Read | Automatically mark messages read when they are pulled by LogicHub (Default is False) | Optional |
| Unread Only | Pull only unread messages (Default is False) | Optional |
| Download attachments | Automatically download all attachments with the mail. (Default False) | Optional |
| Number of messages to be fetched | Jinja-templated text containing the number of messages to be fetched. It'll override $top provided in "Custom OData query" (Default is 10 messages if it is not provided in "Custom OData query" also) | Optional |
Output
JSON containing following items:
{
"attachment_count": 2,
"attachments": [
{
"content_type": "image/png",
"file_name": "Screenshot 2022-05-09 at 10.59.01 AM.png",
"hash_md5": "e0932a256500bdea71195548f00b",
"hash_sha1": "faadf45b94385e11e7bdc507d3d8943575f8",
"hash_sha256": "5458062b29b094fb16d728c482ca1b8b588674783f2b5c35cb33b6b807",
"lhub_file_id": "7ffa875650414b8d8fd2de0abe4",
"size": 23544
},
{
"content_type": "image/png",
"file_name": "Screenshot 2022-05-09 at 11.26.27 AM.png",
"hash_md5": "aca46825dff6181cda18b82c9b",
"hash_sha1": "6a6ec705baa5c0edcca2e4cc5d43cdb9b39",
"hash_sha256": "035be23d50c1c15245687f62a4ffa197c345ff3afb59d167a9a782bc73d",
"lhub_file_id": "9c2fdbc81e2d4745a7d067b31f1",
"size": 21893
}
],
"body": "<html><head>\r\n<meta http-equiv=\"Content-Type\" content=\"text/html; charset=utf-8\"></head><body><div dir=\"ltr\">Hi,<div><br></div><div>PFA.<br clear=\"all\"><div><br></div>-- <br><div dir=\"ltr\" class=\"gmail_signature\"><div dir=\"ltr\"><div><div dir=\"ltr\">Thanks,<div>Indrajeet</div></div></div></div></div></div></div></body></html>",
"body_html": "<html><head>\r\n<meta http-equiv=\"Content-Type\" content=\"text/html; charset=utf-8\"></head><body><div dir=\"ltr\">Hi,<div><br></div><div>PFA.<br clear=\"all\"><div><br></div>-- <br><div dir=\"ltr\" class=\"gmail_signature\"><div dir=\"ltr\"><div><div dir=\"ltr\">Thanks,<div>Indrajeet</div></div></div></div></div></div></div></body></html>",
"body_text": "Hi,\n\n \n\nPFA. \n\n \n\n\\-- \n\nThanks,\n\nIndrajeet\n\n",
"body_type": "HTML",
"categories": [],
"changekey": "CQAAABYAAACJG/25+WUFRIgXSi/IudxUAAOCU5iA",
"date_received": "2022-05-16T12:18:44Z",
"date_sent": "2022-05-16T12:18:28Z",
"error": null,
"from": [
{
"email": "[email protected]",
"name": "Indrajeet Sah"
}
],
"has_error": false,
"headers": [
"Received: from MWHPR0401MB3548.namprd04.prod.outlook.com (2603:10b6:301:79::11) by PH0PR04MB7849.namprd04.prod.outlook.com with HTTPS; Mon, 16 May 2022 12:18:44 +0000",
"Received: from BN8PR16CA0033.namprd16.prod.outlook.com (2603:10b6:408:4c::46) by MWHPR0401MB3548.namprd04.prod.outlook.com (2603:10b6:301:79::11) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.5250.14; Mon, 16 May 2022 12:18:43 +0000",
"X-MS-Exchange-CrossTenant-Id: 09b6e7dd-02b9-4034-84f4-c71214e59109",
"X-MS-Exchange-CrossTenant-AuthSource: BN1NAM02FT029.eop-nam02.prod.protection.outlook.com",
"X-MS-Exchange-CrossTenant-AuthAs: Anonymous",
"X-MS-Exchange-CrossTenant-FromEntityHeader: Internet",
"X-MS-Exchange-Transport-CrossTenantHeadersStamped: MWHPR0401MB3548",
"X-MS-Exchange-Transport-EndToEndLatency: 00:00:02.3478748",
"X-MS-Exchange-Processed-By-BccFoldering: 15.20.5250.018",
"X-Microsoft-Antispam-Mailbox-Delivery: ucf:0;jmr:0;auth:0;dest:I;ENG:(910001)(944506458)(944626604)(920097)(930097);",
"X-Microsoft-Antispam-Message-Info: Y+1Ac3uC5hCQDyj1K65/59C9mQmbT/vnPa5GLtAXeEsaaGrRPu0qJxsMw2TCG/sC3v70O39ngeWP7dt5JgCVQMfsNlr9/Ujgg22YZxy0MA4qQXZjvfNrKOdNJ9tZFgLb105Duc30UpmBUSQ9m+3uwSO5Othrt2MkzR6xpCuRIvbqCfhRCGbnIS0VFQDAZXbi4FjMy6rTlclSSVuYLnMgFmQ0wXMhuxLOZeo6lzwvfJLi9MlmfjTnofMFCR+jKYC+hoN0+EsyZ1BG9i57qJ03Q1nYtpnVN1Qsgfuigw66e9AYtrot5Fn1or42np0ZX+wI5fVx+WXzr6EsMmw+D8sM6BpIAqqNw5FsXkjhWJdWsRQqEqWufNcYBe6kiH9WKtvH32+Co4SgC66c4EAq82miS8udaxUVmLMmO8Eo6q7YM5i8J8btzSvInCgA7PVQEbQx57dXsKzZE8kyyj/Nw9tseZuoT91cV3mzgaxplzjMMuTG/fNfzLqhTfG+5eeIJdsLVlk1H9CEQj70T/13Ey48uJ3AjUG4E89DoN9VQ1cAOha6Jg2BJndbvbeI7HTAOSOY6j8GcTw7ms4/mTNz8HZeNuQMW2sbNf7fONxYWyFuDizIWf6B+18nTpchZHdJC+Ki0LKEMq9EiAoMwZH/dTpM/Y224bjgKG7qCHuYLzGLq95ifmZw/s+RoRMIRPtRshoYK8ZmUbNi3trD5c4Jxn9qSh4ResAfQRG8gjYAtiT7q5zXXA/+dKPvCZlje6+v4VFzLHf0/qI9bWeaFjy/IgpHEODm4b0iK+DTAiuCK2XqpniOfKiM/ckECUjWYzG9nSRYxHGcq/nBBPQ+2d0575J+fBzl80idPPYAVaCHqFv765XhuuE9lZjTmPolK0mi3Fh8O4UYpQsY4QRr7Li9URyl7YXXXM89iHftuWG+dsM/kIlOdktAhmPw3MgonbmDunzgtkOUgtbYFlzlrowaPTbA9zXiIHoJWi4mbzIChdGUNsKVRk9smmwaI7XwVMmo+3hxXim4sl320Xk+ZNFGef3PlRmojTF0Oeyarz1n/hD4IDRO/vKGGfPlCbZTbd5QIf713whBUidi7AL8W7Oa5VuItbXOKEfNKtEBez+sdUXtgTARn6pPaCGHwvF+GOVQtB44WYwsMchI2T55U+OHMsyAYKwD+GRfIu6rHgJVJNY9y2CTMaS/+Yqf6aA073NcNctU7H6rNoFGemgvk1llbT/3ZSY1ZRCAiYboV0H4fXMfSj2q6/K/qWQLv+/MxXfwBQ7qRPIQJ1LFhdaNfcv569i9DMJUdLDWeUMKPWFnzplIjSj4T+Prm+hTIDuOWaezTJ6JB66R/1M6gXDD+d26W83+mAPDQzSI8LaseaHJYPMGff3HQL2rOrs9hDLh5bMYfUIT9pC1Lg2ApoKwex8wSv0lYhb/luLRJpvNCsaM+kjkx3NWZl2NOoz7o7VZI3oC+qeaVSup1dY6imTPjfzZDDZmtinlfpN5GXP67DeL/gBgbWUOAMUfFSQqBZ8VhSVKJVE7Kps+rX9qmpNFu8ZJg/tTWv8KtGy716z8dX/tV5dJ3NNciPF43GyR7Qxzk+YShzlADQqYiG8Rg8Oop8j64L/5yYIsemxi/wSMWjUfSbNY6xTL/HxhTIFThxXQ3sMMTjPWc1ynFGY/1x3O8L2KLaM4lBhVpcLRY4vU9Q5oV+R7SIZeRb2OyseEMRMArtj17ZDZl0QMbLNYQ8J2cET0QO4l+j1sKMCtFOwHnHtteTN9u0eGnJynM11BxaHNUW7/rbledmMhxtCb/xJ98fO2al+LtZK0nsu8XcAgpSOfMAhvq3ZHdGwK6J8fIhwbIj9JMwqX"
],
"headers_dict": {
"Authentication-Results": "spf=pass (sender IP is 209.85.208.178) smtp.mailfrom=logichub.com; dkim=pass (signature was verified) header.d=logichub-com.20210112.gappssmtp.com;dmarc=bestguesspass action=none header.from=logichub.com;compauth=pass reason=109",
"Content-Type": "multipart/mixed",
"DKIM-Signature": "v=1; a=rsa-sha256; c=relaxed/relaxed; d=logichub-com.20210112.gappssmtp.com; s=20210112; h=mime-version:from:date:message-id:subject:to; bh=IBztBsEpR3QApNW6piOosLTQhZjOMG7WYJIqqcmVG0M=; b=rpKk50J28MpaBzgZTp4kkBFhv6p1BFbHEc02xufkvM/JS+dX0mzRfS0ozdPcFOI6n7 x/ZaQ0WHlPNN9WG/OveWuVyPaqE94VTtcxnquJZMNohJnk7L01hjsE3bHOFgJCAKxYUG DgMBmKyE7vq9TCTGSJzk5CjDoSH0OyEDy2/LHBWlt7sb/t9YlJpyb9PDCSYvqgYrhKV8 bDvA0JKu4MEIQuC4ylBgd20TsJVPFFxRvWHaCHa+l2vM8/2N8bzy/+gb0AQ9tQdjHo4h BZdcfVBE719UucftBRAfYzYRDWJWeE8ranS1Js1PYauod+wXUpUeVp5DQqK86tlaRXQe 3c+A==",
"Date": "Mon, 16 May 2022 17:48:28 +0530",
"From": "\"Indrajeet Sah\" <[email protected]>",
"MIME-Version": "1.0",
"X-Received": "by 2002:a2e:b5d4:0:b0:250:82fd:129f with SMTP id g20-20020a2eb5d4000000b0025082fd129fmr11004768ljn.467.1652703520262; Mon, 16 May 2022 05:18:40 -0700 (PDT)"
},
"id": "AAMkAGNjYTNlNWYhNzliNQBGAAAAAABa8sc5ukLMTKUiPJlQGwspBwCJG-25_WUFRIgXSi-IudxUAAAAAAEMAACJG-25_WUFRIgXSi-IudxUAAOCWh6CAAA=",
"is_read": false,
"lhub_ts": "1652706734000",
"msgid": "<[email protected]>",
"recipients": [
"[email protected]"
],
"sender": "[email protected]",
"subject": "Test Email with multiple attachments",
"urls": [],
"urls_all": [],
"urls_probable": []
}
Revoke Sign-in Sessions
Invalidates all the refresh tokens issued to applications for a user (as well as session cookies in a user's browser), by resetting the signInSessionsValidFromDateTime user property to the current date-time.
Permission Required(Application): User.ReadWrite.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja templated text containing the user's principal name or user's unique identifier(id). Example: {{user_principal_name}} | Required |
Output
JSON containing the following items:
{
"has_error":false,
"value":true,
"@odata.context":"https://graph.microsoft.com/v1.0/$metadata#Edm.Boolean",
"error":null
}
Update User
Update the properties of a user object. Not all properties can be updated by Member or Guest users with their default permissions without Administrator roles.
Permission Required(Application): User.ReadWrite.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| User Object | Jinja-templated JSON containing the user object. Example: '{"businessPhones": "User's principal n, "officeLocation": "18/2111"}' | Required |
Output
JSON containing the following items:
{
"msg":"Successfully updated.",
"has_error":false,
"error":null
}
List Password Methods
Retrieve a list of the passwords registered to a user, represented by a passwordAuthenticationMethod object. This will return exactly one object, as a user can have exactly one password. For security, the password itself will never be returned in the object and the password property is always null.
Permission Required(Application): User.ReadWrite.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Limit | Jinja-templated number containing the limit of the no. of results. Default is 1000 | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "28c10230-6103-485e-b985-444c60001490",
"password": null,
"createdDateTime": null
}
],
"error":null,
"has_error":false
}
Get Password Method
Retrieve a password that's registered to a user, represented by a passwordAuthenticationMethod object. For security, the password itself will never be returned in the object and the password property is always null.
Permission Required(Application): User.ReadWrite.All, Directory.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Password Method Id | Jinja-templated text containing the password method Id. | Required |
Output
JSON containing the following items:
{
"id": "28c10230-6103-485e-b985-444c60001490",
"password": null,
"creationDateTime": null,
"error":null,
"has_error":false
}
List Phone Methods
Retrieve a list of phone authentication method objects for a user. This will return up to three objects, as a user can have up to three phones usable for authentication. This method is available only for standard Azure AD and B2B users, but not B2C users.
Permission Required(Application): UserAuthenticationMethod.Read.All, UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Limit | Jinja-templated number containing the limit of the no. of results. Default is 1000 | Optional |
Output
JSON containing the following items:
{
"value": [
{
"phoneNumber": "+1 2065555555",
"phoneType": "mobile",
"smsSignInState": "ready",
"id": "3179e48a-750b-4051-897c-87b9720928f7"
},
{
"phoneNumber": "+1 2065555556",
"phoneType": "alternateMobile",
"smsSignInState": "notSupported",
"id": "b6332ec1-7057-4abe-9331-3d72feddfe41"
},
{
"phoneNumber": "+1 2065555557",
"phoneType": "office",
"smsSignInState": "notSupported",
"id": "e37fc753-ff3b-4958-9484-eaa9425c82bc"
}
],
"error":null,
"has_error":false
}
Get Phone Method
Retrieve a single phoneAuthenticationMethod object for a user. This method is available only for standard Azure AD and B2B users, but not B2C users.
Permission Required(Application): UserAuthenticationMethod.Read.All, UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Phone Method Id | Jinja-templated text containing the phone method Id. | Required |
Output
JSON containing the following items:
{
"phoneNumber": "+1 2065555555",
"phoneType": "mobile",
"smsSignInState": "ready",
"id": "3179e48a-750b-4051-897c-87b9720928f7",
"error":null,
"has_error":false
}
Delete Phone Method
Delete a user's phone authentication method. This removes the phone number from the user and they will no longer be able to use the number for authentication, whether via SMS or voice calls.
Permission Required(Application): UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Phone Method Id | Jinja-templated text containing the phone method Id. | Required |
Output
JSON containing the following items:
{
"message": "Successfully deleted.",
"error":null,
"has_error":false
}
Update Phone Method
Update a user's phone number associated with a phone authentication method object.
Permission Required(Application): UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Phone Method Id | Jinja-templated text containing the phone method Id. | Required |
| Phone Number | Jinja-templated text containing the phone number. The phone number to text or call for authentication. Phone numbers use the format +{country code} {number}x{extension}, with extension optional. For example, '+1 5555551234' or '+1 5555551234x123' are valid. Numbers are rejected when creating or updating if they do not match the required format. | Required |
| Phone Type | Jinja-templated text containing the phone type. Possible values are: mobile, alternateMobile, and office. | Optional |
Output
JSON containing the following items:
{
"message": "Successfully updated.",
"error":null,
"has_error":false
}
Add Phone Method
Update a user's phone number associated with a phone authentication method object.
Permission Required(Application): UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Phone Number | Jinja-templated text containing the phone number. The phone number to text or call for authentication. Phone numbers use the format +{country code} {number}x{extension}, with extension optional. For example, '+1 5555551234' or '+1 5555551234x123' are valid. Numbers are rejected when creating or updating if they do not match the required format. | Required |
| Phone Type | Jinja-templated text containing the phone type. Possible values are: mobile, alternateMobile, and office. | Required |
Output
JSON containing the following items:
{
"phoneNumber": "+1 2065555555",
"phoneType": "phoneType-value",
"smsSignInState": "ready",
"id": "3179e48a-750b-4051-897c-87b9720928f7",
"error":null,
"has_error":false
}
Enable SMS Sign-in
Enable SMS sign-in for an existing mobile phone number registered to a user.
Permission Required(Application): UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Phone Method Id | Jinja-templated text containing the phone method Id. | Required |
Output
JSON containing the following items:
{
"message": "Successfully updated.",
"error":null,
"has_error":false
}
Disable SMS Sign-in
Disable SMS sign-in for an existing mobile phone number registered to a user. The number will no longer be available for SMS sign-in, which can prevent your user from signing in.
Permission Required(Application): UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Phone Method Id | Jinja-templated text containing the phone method Id. | Required |
Output
JSON containing the following items:
{
"message": "Successfully updated.",
"error":null,
"has_error":false
}
List Microsoft Authenticator Methods
Get a list of the microsoftAuthenticatorAuthenticationMethod objects and their properties.
Permission Required(Application): UserAuthenticationMethod.Read.All, UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Limit | Jinja-templated number containing the limit of the no. of results. Default is 1000 | Optional |
Output
JSON containing the following items:
{
"value": [
{
"@odata.type": "#microsoft.graph.microsoftAuthenticatorAuthenticationMethod",
"id": "6803c096-c096-6803-96c0-036896c00368",
"displayName": "Sandeep's iPhone",
"deviceTag": "",
"phoneAppVersion": "6.5.4",
"createdDateTime": "2020-12-03T23:16:12Z"
}
],
"error":null,
"has_error":false
}
Get Microsoft Authenticator Method
Read the properties and relationships of a microsoftAuthenticatorAuthenticationMethod object.
Permission Required(Application): UserAuthenticationMethod.Read.All, UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the phone microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"value": {
"@odata.type": "#microsoft.graph.microsoftAuthenticatorAuthenticationMethod",
"id": "6803c096-c096-6803-96c0-036896c00368",
"displayName": "Sandeep's iPhone",
"deviceTag": "",
"phoneAppVersion": "6.5.4",
"createdDateTime": "2020-12-03T23:16:12Z"
},
"error":null,
"has_error":false
}
Delete Microsoft Authenticator Method
Deletes a microsoftAuthenticatorAuthenticationMethod object.
Permission Required(Application): UserAuthenticationMethod.ReadWrite.All
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"message": "Successfully deleted.",
"error":null,
"has_error":false
}
List FIDO2 Authentication Method
Retrieve a list of a user's FIDO2 Security Key Authentication Method objects and their properties.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Limit | Jinja-templated number containing the limit of the no. of results. (Default is 1000) | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "-2_GRUg2-HYz6_1YG4YRAQ2",
"displayName": "Red key",
"creationDateTime": "2020-08-10T06:44:09Z",
"aaGuid": "2fc0579f-8113-47ea-b116-555a8db9202a",
"model": "NFC key",
"attestationCertificates": [
"dbe793efdf1945e2df25d93653a1e8a3268a9075"
],
"attestationLevel": "attested"
},
{
"id": "_jpuR-TGZgk6aQCLF3BQjA2",
"displayName": "Blue key",
"creationDateTime": "2020-08-10T06:25:38Z",
"aaGuid": "c5ef55ff-ad9a-4b9f-b580-ababafe026d0",
"model": "USB key",
"attestationCertificates": [
"b479e7652167f574296e76bfa76731b8ccd22ed7"
],
"attestationLevel": "attested"
}
],
"error":null,
"has_error":false
}
Get FIDO2 Authentication Method
Read the properties and relationships of a fido2AuthenticationMethod object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the phone microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"id": "-2_GRUg2-HYz6_1YG4YRAQ2",
"displayName": "Red key",
"creationDateTime": "2020-08-10T06:44:09Z",
"aaGuid": "2fc0579f-8113-47ea-b116-555a8db9202a",
"model": "NFC key",
"attestationCertificates": [
"dbe793efdf1945e2df25d93653a1e8a3268a9075"
],
"attestationLevel": "attested",
"error":null,
"has_error":false
}
Delete FIDO2 Authenticator Method
Deletes a fido2AuthenticationMethod object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"message": "Successfully deleted.",
"error":null,
"has_error":false
}
List Software OATH Authentication Method
Retrieve a list of a user's software OATH token authentication method objects and their properties.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Limit | Jinja-templated number containing the limit of the no. of results. (Default is 1000) | Optional |
Output
JSON containing the following items:
{
"value": [
{
"@odata.type": "#microsoft.graph.softwareOathAuthenticationMethod",
"id": "b172893e-893e-b172-3e89-72b13e8972b1",
"secretKey": null
}
],
"error":null,
"has_error":false
}
Get Software OATH Authentication Method
Retrieve a user's single Software OATH token authentication method object and its properties.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the phone microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"@odata.type": "#microsoft.graph.softwareOathAuthenticationMethod",
"id": "b172893e-893e-b172-3e89-72b13e8972b1",
"secretKey": null,
"error":null,
"has_error":false
}
Delete Software OATH Authentication Method
Delete a user's Software OATH token authentication method object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"message": "Successfully deleted.",
"error":null,
"has_error":false
}
List Windows Hello for Business Authentication Method
Get a list of the windowsHelloForBusinessAuthenticationMethod objects and their properties.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Limit | Jinja-templated number containing the limit of the no. of results. (Default is 1000) | Optional |
Output
JSON containing the following items:
{
"value": [
{
"@odata.type": "#microsoft.graph.windowsHelloForBusinessAuthenticationMethod",
"id": "b5e01f81-1f81-b5e0-811f-e0b5811fe0b5",
"displayName": "Jordan's Surface Book",
"createdDateTime": "2020-11-27T23:12:49Z",
"keyStrength": "normal"
},
{
"@odata.type": "#microsoft.graph.windowsHelloForBusinessAuthenticationMethod",
"id": "e6dab818-e68d-433e-89d5-547357870cb2",
"displayName": "New Surface Duo",
"createdDateTime": "2020-12-25T02:20:13Z",
"keyStrength": "normal"
}
],
"error":null,
"has_error":false
}
Get Windows Hello for Business Authentication Method
Read the properties and relationships of a windowsHelloForBusinessAuthenticationMethod object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the phone microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"@odata.type": "#microsoft.graph.windowsHelloForBusinessAuthenticationMethod",
"id": "b5e01f81-1f81-b5e0-811f-e0b5811fe0b5",
"displayName": "Jordan's Surface Book",
"createdDateTime": "2020-11-27T23:12:49Z",
"keyStrength": "normal",
"error":null,
"has_error":false
}
Delete Windows Hello for Business Authentication Method
Deletes a windowsHelloForBusinessAuthenticationMethod object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Microsoft Authenticator Method Id | Jinja-templated text containing the microsoft authenticator method Id. | Required |
Output
JSON containing the following items:
{
"message": "Successfully deleted.",
"error":null,
"has_error":false
}
Get User Registration Details
Read the properties and relationships of a userRegistrationDetails object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User Id | Jinja-templated text containing the user Id. | Required |
Output
JSON containing the following items:
{
"@odata.type": "#microsoft.graph.userRegistrationDetails",
"id": "String (identifier)",
"isAdmin": "Boolean",
"isMfaCapable": "Boolean",
"isMfaRegistered": "Boolean",
"isPasswordlessCapable": "Boolean",
"isSsprCapable": "Boolean",
"isSsprEnabled": "Boolean",
"isSsprRegistered": "Boolean",
"isSystemPreferredAuthenticationMethodEnabled": "Boolean",
"lastUpdatedDateTime": "String (timestamp)",
"methodsRegistered": ["String"],
"systemPreferredAuthenticationMethods": ["String"],
"userDisplayName": "String",
"userPreferredMethodForSecondaryAuthentication": "String",
"userPrincipalName": "String",
"userType": "String",
"error": null,
"has_error":false
}
Get User Mailbox Settings
Get the user's mailbox settings.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
Output
JSON containing the following items:
{
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#Me/mailboxSettings",
"automaticRepliesSetting": {
"status": "Scheduled",
"externalAudience": "All",
"scheduledStartDateTime": {
"dateTime": "2016-03-14T07:00:00.0000000",
"timeZone": "UTC"
},
"scheduledEndDateTime": {
"dateTime": "2016-03-28T07:00:00.0000000",
"timeZone": "UTC"
},
"internalReplyMessage": "<html>\n<body>\n<p>I'm at our company's worldwide reunion and will respond to your message as soon as I return.<br>\n</p></body>\n</html>\n",
"externalReplyMessage": "<html>\n<body>\n<p>I'm at the Contoso worldwide reunion and will respond to your message as soon as I return.<br>\n</p></body>\n</html>\n"
},
"timeZone":"UTC",
"language":{
"locale":"en-US",
"displayName":"English (United States)"
},
"workingHours":{
"daysOfWeek":[
"monday",
"tuesday",
"wednesday",
"thursday",
"friday"
],
"startTime": "08:00:00.0000000",
"endTime": "17:00:00.0000000",
"timeZone":{
"name":"Pacific Standard Time"
}
},
"userPurpose": {
"value": "user"
},
"dateFormat": "MM/dd/yyyy",
"timeFormat": "hh:mm tt",
"delegateMeetingMessageDeliveryOptions": "sendToDelegateOnly",
"error": null,
"has_error": false
}
Reply All
Reply to all the recipients of the provided message.
Permission Required(Application): Mail.Send
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Message's unique identifier (ID) | Message's unique identifier (ID). | Required |
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
Output
JSON containing the following items:
{
"date_sent": "2023-12-08 05:54:44 UTC",
"msg": "E-mail sent successfully",
"has_error": false,
"error": null
}
Create Reply All
Create a draft to reply to the sender and all recipients of a message.
Permission Required(Application): Mail.ReadWrite
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Message's unique identifier (ID) | Message's unique identifier (ID). | Required |
| User's principal name or user's unique identifier (ID) Column name | Column name from parent table containing the user's principal name or user's unique identifier (ID). | Required |
Output
Return a JSON with no error on successful completion.
{
"date_sent": "2023-12-08 05:54:44 UTC",
"msg": "Successfully create a message draft to reply-all to an existing message",
"has_error": false,
"error": null
}
List Users V2
Retrieve a list of user objects. This action enables use of jinja template. Each row will be separately processed using the input jinja values if provided.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Select Query | Jinja-templated text containing the select query. Example 'displayName,givenName' | Optional |
| Filter | Jinja-templated text containing the filter query to filter properties (Default is no filter). Example startswith(displayName,'a') | Optional |
Output
Return a list of JSON objects, each of which represents a user.

Add Attachments
Add an attachment to a message.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated string containing user's principal name or user's unique identifier(id). Example: {{user_principal_id}} | Required |
| Message's unique identifier(id) | Jinja-templated text containing the Message's unique identifier(id). Example: {{message_id}} | Required |
| Attachment object. | Jinja-templated JSON containing attachment object. Example: {"@odata.type":"#microsoft.graph.fileAttachment","contentBytes":"valid base64 encoded file content", "name":"name.jpg"} | Required |
Output
JSON containing the following items:
{
"name": "ATT00001.jpg",
"size": 2331,
"contentBytes": "/9j/U3Cof//Z",
"isInline": true,
"@odata.type": "#microsoft.graph.fileAttachment",
"has_error": false,
"id": "id",
"contentType": "image/jpeg",
"error": null,
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#users/messages/attachments/$entity",
"contentId": "content",
"@odata.mediaContentType": "image/jpeg",
"contentLocation": null,
"lastModifiedDateTime": "2024-06-06T06:24:44Z"
}
Send Draft
Send an existing draft message.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated string containing user's principal name or user's unique identifier(id). Example: {{user_principal_id}} | Required |
| Message's unique identifier(id) | Jinja-templated text containing the Message's unique identifier(id). Example: {{message_id}} | Required |
Output
JSON containing the following items:
{
"date_sent": "2024-06-06T06:24:44Z",
"msg": "Successfully send a message draft."
}
List Message Rule
List message rule that applies to messages in the inbox of a user.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example: {{user_principal_name}} | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.context":"https://graph.microsoft.com/v1.0/$metadata#Me/mailFolders('inbox')/messageRules",
"value":[
{
"id":"AQAAAJ5dZp8=",
"displayName":"Remove spam",
"sequence":1,
"isEnabled":true,
"hasError":false,
"isReadOnly":false,
"conditions":{
"subjectContains":[
"enter to win"
]
},
"actions":{
"delete":true,
"stopProcessingRules":true
}
},
{
"id":"AQAAAJ5dZqA=",
"displayName":"From partner",
"sequence":2,
"isEnabled":true,
"hasError":false,
"isReadOnly":false,
"conditions":{
"senderContains":[
"ADELE"
]
},
"actions":{
"stopProcessingRules":true,
"forwardTo":[
{
"emailAddress":{
"name":"Alex Wilbur",
"address":"[email protected]"
}
}
]
}
}
]
}
}
Get Message Rule
Get the properties and relationships of a message rule object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example: {{user_principal_name}} | Required |
| Message Rule Id | Jinja-templated text containing the message rule Id | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.context":"https://graph.microsoft.com/beta/$metadata#Me/mailFolders('inbox')/messageRules/$entity",
"id":"AQAAAJ5dZqA=",
"displayName":"From partner",
"sequence":2,
"isEnabled":true,
"hasError":false,
"isReadOnly":false,
"conditions":{
"senderContains":[
"ADELE"
]
},
"actions":{
"stopProcessingRules":true,
"forwardTo":[
{
"emailAddress":{
"name":"Alex Wilbur",
"address":"[email protected]"
}
}
]
}
}
}
Create Message Rule
Create a messageRule object by specifying a set of conditions and actions.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example: {{user_principal_name}} | Required |
| Message Rule Name | Jinja-templated text containing the display name of the rule | Required |
| Message Rule Action | Jinja-templated text containing the actions to be taken on a message when the corresponding conditions, if any, are fulfilled. | Required |
| Message Rule Sequence | Jinja-templated text containing the sequence indicating the order in which the rule is executed, among other rules. | Required |
| Message Rule Enabled | Indicates whether the rule is enabled to be applied to messages. Default No | Optional |
| Message Rule Exception | Jinja-templated text containing the exception conditions for the rule. | Optional |
| Message Rule Conditions | Jinja-templated text containing the conditions that when fulfilled, will trigger the corresponding actions for that rule. | Optional |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"displayName": "From partner",
"sequence": 2,
"isEnabled": true,
"conditions": {
"senderContains": [
"adele"
]
},
"actions": {
"forwardTo": [
{
"emailAddress": {
"name": "Alex Wilbur",
"address": "[email protected]"
}
}
],
"stopProcessingRules": true
}
}
}
Update Message Rule
Change writable properties on a messageRule object and save the changes.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example: {{user_principal_name}} | Required |
| Message Rule Id | Jinja-templated text containing the message rule Id | Required |
| Message Rule Name | Jinja-templated text containing the display name of the rule | Optional |
| Message Rule Action | Jinja-templated text containing the actions to be taken on a message when the corresponding conditions, if any, are fulfilled. | Optional |
| Message Rule Sequence | Jinja-templated text containing the sequence indicating the order in which the rule is executed, among other rules. | Optional |
| Message Rule Enabled | Indicates whether the rule is enabled to be applied to messages. Default Yes | Optional |
| Message Rule Exception | Jinja-templated text containing the exception conditions for the rule. | Optional |
| Message Rule Conditions | Jinja-templated text containing the conditions that when fulfilled, will trigger the corresponding actions for that rule. | Optional |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result":{
"@odata.context":"https://graph.microsoft.com/v1.0/$metadata#Me/mailFolders('inbox')/messageRules/$entity",
"id":"AQAAAJ5dZqA=",
"displayName":"Important from partner",
"sequence":2,
"isEnabled":true,
"hasError":false,
"isReadOnly":false,
"conditions":{
"senderContains":[
"ADELE"
]
},
"actions":{
"markImportance": "high"
}
}
}
Delete Message Rule
Delete the specified message rule object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example: {{user_principal_name}} | Required |
| Message Rule Id | Jinja-templated text containing the message rule Id | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"msg": "Successfully deleted the message rule."
}
}
List Devices
Retrieve a list of device objects registered in the organization.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Query Filter | Jinja-templated text containing the OData query filter. If no filter is provided top 100 rows will be returned | Optional |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"value": [
{
"accountEnabled":true,
"deviceId":"00000000-0000-0000-0000-000000000000",
"deviceVersion":1,
"displayName":"contoso_Android",
"Manufacturer":"Google",
"Model":"Pixel 3a",
"operatingSystemVersion":"10.0"
},
{
"accountEnabled":true,
"deviceId":"00000000-0000-0000-0000-000000000000",
"deviceVersion":1,
"displayName":"contoso_Android",
"Manufacturer":"Google",
"Model":"Pixel 3a",
"operatingSystemVersion":"10.0"
}
]
}
}
Get Device
Get the properties and relationships of a device object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Device Id | Jinja-templated text containing the device Id | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"value":{
"accountEnabled":true,
"deviceId":"00000000-0000-0000-0000-000000000000",
"deviceVersion":1,
"displayName":"contoso_Android",
"Manufacturer":"Google",
"Model":"Pixel 3a",
"operatingSystemVersion":"10.0"
}
}
}
List Registered Owners of Device
Retrieve a list of users that are registered owners of the device. A registered owner is the user that cloud joined the device or registered their personal device. The registered owner is set at the time of registration. Currently, there can be only one owner.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Device Id | Jinja-templated text containing the device Id | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#directoryObjects",
"value": [
{
"@odata.type": "#microsoft.graph.user",
"@odata.id": "https://graph.microsoft.com/v2/72f988bf-86f1-41af-91ab-2d7cd011db47/directoryObjects/96a5df40-617b-4450-8b7a-1dc18b872d8f/Microsoft.DirectoryServices.User",
"id": "96a5df40-617b-4450-8b7a-1dc18b872d8f"
}
]
}
}
List Registered Users of Device
Retrieve a list of users that are registered users of the device.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Device Id | Jinja-templated text containing the device Id | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.context": "https://graph.microsoft.com/beta/$metadata#directoryObjects",
"value": [
{
"@odata.type": "#microsoft.graph.user",
"@odata.id": "https://graph.microsoft.com/v2/72f988bf-86f1-41af-91ab-2d7cd011db47/directoryObjects/96a5df40-617b-4450-8b7a-1dc18b872d8f/Microsoft.DirectoryServices.User",
"id": "96a5df40-617b-4450-8b7a-1dc18b872d8f",
"displayName": "Alex Wilber",
"mail": "[email protected]",
"mailNickname": "[email protected]"
}
]
}
}
List Alert
Get a list of alert resources created to track suspicious activities in an organization.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Query Filter | Jinja-templated text containing the OData query filter | Optional |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"value": [
{
"@odata.type": "#microsoft.graph.security.alert",
"id": "da637551227677560813_-961444813",
"providerAlertId": "da637551227677560813_-961444813",
"incidentId": "28282",
"status": "new",
"severity": "low",
"classification": "unknown",
"determination": "unknown",
"serviceSource": "microsoftDefenderForEndpoint",
"detectionSource": "antivirus",
"detectorId": "e0da400f-affd-43ef-b1d5-afc2eb6f2756",
"tenantId": "b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"title": "Suspicious execution of hidden file",
"description": "A hidden file has been launched. This activity could indicate a compromised host. Attackers often hide files associated with malicious tools to evade file system inspection and defenses.",
"recommendedActions": "Collect artifacts and determine scope\n�\tReview the machine timeline for suspicious activities that may have occurred before and after the time of the alert, and record additional related artifacts (files, IPs/URLs) \n�\tLook for the presence of relevant artifacts on other systems. Identify commonalities and differences between potentially compromised systems.\n�\tSubmit relevant files for deep analysis and review resulting detailed behavioral information.\n�\tSubmit undetected files to the MMPC malware portal\n\nInitiate containment & mitigation \n�\tContact the user to verify intent and initiate local remediation actions as needed.\n�\tUpdate AV signatures and run a full scan. The scan might reveal and remove previously-undetected malware components.\n�\tEnsure that the machine has the latest security updates. In particular, ensure that you have installed the latest software, web browser, and Operating System versions.\n�\tIf credential theft is suspected, reset all relevant users passwords.\n�\tBlock communication with relevant URLs or IPs at the organization�s perimeter.",
"category": "DefenseEvasion",
"assignedTo": null,
"alertWebUrl": "https://security.microsoft.com/alerts/da637551227677560813_-961444813?tid=b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"incidentWebUrl": "https://security.microsoft.com/incidents/28282?tid=b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"actorDisplayName": null,
"threatDisplayName": null,
"threatFamilyName": null,
"mitreTechniques": [
"T1564.001"
],
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"lastUpdateDateTime": "2021-05-02T14:19:01.3266667Z",
"resolvedDateTime": null,
"firstActivityDateTime": "2021-04-26T07:45:50.116Z",
"lastActivityDateTime": "2021-05-02T07:56:58.222Z",
"comments": [],
"evidence": [
{
"@odata.type": "#microsoft.graph.security.deviceEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"firstSeenDateTime": "2020-09-12T07:28:32.4321753Z",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"azureAdDeviceId": null,
"deviceDnsName": "tempDns",
"osPlatform": "Windows10",
"osBuild": 22424,
"version": "Other",
"healthStatus": "active",
"riskScore": "medium",
"rbacGroupId": 75,
"rbacGroupName": "UnassignedGroup",
"onboardingStatus": "onboarded",
"defenderAvStatus": "unknown",
"ipInterfaces": [
"1.1.1.1"
],
"loggedOnUsers": [],
"roles": [
"compromised"
],
"detailedRoles": [
"Main device"
],
"tags": [
"Test Machine"
],
"vmMetadata": {
"vmId": "ca1b0d41-5a3b-4d95-b48b-f220aed11d78",
"cloudProvider": "azure",
"resourceId": "/subscriptions/8700d3a3-3bb7-4fbe-a090-488a1ad04161/resourceGroups/WdatpApi-EUS-STG/providers/Microsoft.Compute/virtualMachines/NirLaviTests",
"subscriptionId": "8700d3a3-3bb7-4fbe-a090-488a1ad04161"
}
},
{
"@odata.type": "#microsoft.graph.security.fileEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"detectionStatus": "detected",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"roles": [],
"detailedRoles": [
"Referred in command line"
],
"tags": [],
"fileDetails": {
"sha1": "5f1e8acedc065031aad553b710838eb366cfee9a",
"sha256": "8963a19fb992ad9a76576c5638fd68292cffb9aaac29eb8285f9abf6196a7dec",
"fileName": "MsSense.exe",
"filePath": "C:\\Program Files\\temp",
"fileSize": 6136392,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
}
},
{
"@odata.type": "#microsoft.graph.security.processEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"processId": 4780,
"parentProcessId": 668,
"processCommandLine": "\"MsSense.exe\"",
"processCreationDateTime": "2021-08-12T12:43:19.0772577Z",
"parentProcessCreationDateTime": "2021-08-12T07:39:09.0909239Z",
"detectionStatus": "detected",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"roles": [],
"detailedRoles": [],
"tags": [],
"imageFile": {
"sha1": "5f1e8acedc065031aad553b710838eb366cfee9a",
"sha256": "8963a19fb992ad9a76576c5638fd68292cffb9aaac29eb8285f9abf6196a7dec",
"fileName": "MsSense.exe",
"filePath": "C:\\Program Files\\temp",
"fileSize": 6136392,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
},
"parentProcessImageFile": {
"sha1": null,
"sha256": null,
"fileName": "services.exe",
"filePath": "C:\\Windows\\System32",
"fileSize": 731744,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
},
"userAccount": {
"accountName": "SYSTEM",
"domainName": "NT AUTHORITY",
"userSid": "S-1-5-18",
"azureAdUserId": null,
"userPrincipalName": null,
"displayName": "System"
}
},
{
"@odata.type": "#microsoft.graph.security.registryKeyEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"registryKey": "SYSTEM\\CONTROLSET001\\CONTROL\\WMI\\AUTOLOGGER\\SENSEAUDITLOGGER",
"registryHive": "HKEY_LOCAL_MACHINE",
"roles": [],
"detailedRoles": [],
"tags": []
}
],
"systemTags" : [
"Defender Experts"
]
}
]
}
}
Get Alert
Get the properties and relationships of an alert object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Id | Jinja-templated text containing the alert Id | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.type": "#microsoft.graph.security.alert",
"id": "da637578995287051192_756343937",
"providerAlertId": "da637578995287051192_756343937",
"incidentId": "28282",
"status": "new",
"severity": "low",
"classification": "unknown",
"determination": "unknown",
"serviceSource": "microsoftDefenderForEndpoint",
"detectionSource": "antivirus",
"productName": "Microsoft Defender for Endpoint",
"detectorId": "e0da400f-affd-43ef-b1d5-afc2eb6f2756",
"tenantId": "b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"title": "Suspicious execution of hidden file",
"description": "A hidden file has been launched. This activity could indicate a compromised host. Attackers often hide files associated with malicious tools to evade file system inspection and defenses.",
"recommendedActions": "Collect artifacts and determine scope\n�\tReview the machine timeline for suspicious activities that may have occurred before and after the time of the alert, and record additional related artifacts (files, IPs/URLs) \n�\tLook for the presence of relevant artifacts on other systems. Identify commonalities and differences between potentially compromised systems.\n�\tSubmit relevant files for deep analysis and review resulting detailed behavioral information.\n�\tSubmit undetected files to the MMPC malware portal\n\nInitiate containment & mitigation \n�\tContact the user to verify intent and initiate local remediation actions as needed.\n�\tUpdate AV signatures and run a full scan. The scan might reveal and remove previously-undetected malware components.\n�\tEnsure that the machine has the latest security updates. In particular, ensure that you have installed the latest software, web browser, and Operating System versions.\n�\tIf credential theft is suspected, reset all relevant users passwords.\n�\tBlock communication with relevant URLs or IPs at the organization�s perimeter.",
"category": "DefenseEvasion",
"assignedTo": null,
"alertWebUrl": "https://security.microsoft.com/alerts/da637578995287051192_756343937?tid=b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"incidentWebUrl": "https://security.microsoft.com/incidents/28282?tid=b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"actorDisplayName": null,
"threatDisplayName": null,
"threatFamilyName": null,
"mitreTechniques": [
"T1564.001"
],
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"lastUpdateDateTime": "2021-05-02T14:19:01.3266667Z",
"resolvedDateTime": null,
"firstActivityDateTime": "2021-04-26T07:45:50.116Z",
"lastActivityDateTime": "2021-05-02T07:56:58.222Z",
"comments": [],
"evidence": [
{
"@odata.type": "#microsoft.graph.security.deviceEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"firstSeenDateTime": "2020-09-12T07:28:32.4321753Z",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"azureAdDeviceId": null,
"deviceDnsName": "tempDns",
"osPlatform": "Windows10",
"osBuild": 22424,
"version": "Other",
"healthStatus": "active",
"riskScore": "medium",
"rbacGroupId": 75,
"rbacGroupName": "UnassignedGroup",
"onboardingStatus": "onboarded",
"defenderAvStatus": "unknown",
"ipInterfaces": [
"1.1.1.1"
],
"loggedOnUsers": [],
"roles": [
"compromised"
],
"detailedRoles": [
"Main device"
],
"tags": [
"Test Machine"
],
"vmMetadata": {
"vmId": "ca1b0d41-5a3b-4d95-b48b-f220aed11d78",
"cloudProvider": "azure",
"resourceId": "/subscriptions/8700d3a3-3bb7-4fbe-a090-488a1ad04161/resourceGroups/WdatpApi-EUS-STG/providers/Microsoft.Compute/virtualMachines/NirLaviTests",
"subscriptionId": "8700d3a3-3bb7-4fbe-a090-488a1ad04161"
}
},
{
"@odata.type": "#microsoft.graph.security.fileEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"detectionStatus": "detected",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"roles": [],
"detailedRoles": [
"Referred in command line"
],
"tags": [],
"fileDetails": {
"sha1": "5f1e8acedc065031aad553b710838eb366cfee9a",
"sha256": "8963a19fb992ad9a76576c5638fd68292cffb9aaac29eb8285f9abf6196a7dec",
"fileName": "MsSense.exe",
"filePath": "C:\\Program Files\\temp",
"fileSize": 6136392,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
}
},
{
"@odata.type": "#microsoft.graph.security.processEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"processId": 4780,
"parentProcessId": 668,
"processCommandLine": "\"MsSense.exe\"",
"processCreationDateTime": "2021-08-12T12:43:19.0772577Z",
"parentProcessCreationDateTime": "2021-08-12T07:39:09.0909239Z",
"detectionStatus": "detected",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"roles": [],
"detailedRoles": [],
"tags": [],
"imageFile": {
"sha1": "5f1e8acedc065031aad553b710838eb366cfee9a",
"sha256": "8963a19fb992ad9a76576c5638fd68292cffb9aaac29eb8285f9abf6196a7dec",
"fileName": "MsSense.exe",
"filePath": "C:\\Program Files\\temp",
"fileSize": 6136392,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
},
"parentProcessImageFile": {
"sha1": null,
"sha256": null,
"fileName": "services.exe",
"filePath": "C:\\Windows\\System32",
"fileSize": 731744,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
},
"userAccount": {
"accountName": "SYSTEM",
"domainName": "NT AUTHORITY",
"userSid": "S-1-5-18",
"azureAdUserId": null,
"userPrincipalName": null,
"displayName": "System"
}
},
{
"@odata.type": "#microsoft.graph.security.registryKeyEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"registryKey": "SYSTEM\\CONTROLSET001\\CONTROL\\WMI\\AUTOLOGGER\\SENSEAUDITLOGGER",
"registryHive": "HKEY_LOCAL_MACHINE",
"roles": [],
"detailedRoles": [],
"tags": []
}
],
"systemTags" : [
"Defender Experts"
],
"additionalData": {
"key1": "value1",
"key2": "value2"
}
}
}
Create Comment for Alert
Create a comment for an existing alert based on the specified alert id property.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Id | Jinja-templated text containing the alert Id | Required |
| Comment | Jinja-templated text containing the comment | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.context": "https://graph.microsoft.com/beta/$metadata#security/alerts_v2('da637865765418431569_-773071023')/comments",
"value": [
{
"comment": "test",
"createdByDisplayName": "[email protected]",
"createdDateTime": "2022-10-13T07:08:30.1606766Z"
},
{
"comment": "Demo for docs",
"createdByDisplayName": "[email protected]",
"createdDateTime": "2022-10-13T07:08:40.3825324Z"
}
]
}
}
Update Alert
Update the properties of an alert object in an organization based on the specified alert id property.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Id | Jinja-templated text containing the alert Id | Required |
| Assignee | Jinja-templated text containing the assignee for alert. Owner of the incident, or null if no owner is assigned. | Optional |
| Status | Jinja-templated text containing the status of alert. Possible values are: new, inProgress, resolved, unknownFutureValue. | Optional |
| Classification | Jinja-templated text containing the classification of alert. Possible values are: unknown, falsePositive, truePositive, informationalExpectedActivity, unknownFutureValue. | Optional |
| Determination | Jinja-templated text containing the determination of alert. Possible values are: unknown, apt, malware, securityPersonnel, securityTesting, unwantedSoftware, other, multiStagedAttack, compromisedUser, phishing, maliciousUserActivity, clean, insufficientData, confirmedUserActivity, lineOfBusinessApplication, unknownFutureValue | Optional |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.type": "#microsoft.graph.security.alert",
"id": "da637578995287051192_756343937",
"providerAlertId": "da637578995287051192_756343937",
"incidentId": "28282",
"status": "new",
"severity": "low",
"classification": "unknown",
"determination": "unknown",
"serviceSource": "microsoftDefenderForEndpoint",
"detectionSource": "antivirus",
"productName": "Microsoft Defender for Endpoint",
"detectorId": "e0da400f-affd-43ef-b1d5-afc2eb6f2756",
"tenantId": "b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"title": "Suspicious execution of hidden file",
"description": "A hidden file has been launched. This activity could indicate a compromised host. Attackers often hide files associated with malicious tools to evade file system inspection and defenses.",
"recommendedActions": "Collect artifacts and determine scope\n�\tReview the machine timeline for suspicious activities that may have occurred before and after the time of the alert, and record additional related artifacts (files, IPs/URLs) \n�\tLook for the presence of relevant artifacts on other systems. Identify commonalities and differences between potentially compromised systems.\n�\tSubmit relevant files for deep analysis and review resulting detailed behavioral information.\n�\tSubmit undetected files to the MMPC malware portal\n\nInitiate containment & mitigation \n�\tContact the user to verify intent and initiate local remediation actions as needed.\n�\tUpdate AV signatures and run a full scan. The scan might reveal and remove previously-undetected malware components.\n�\tEnsure that the machine has the latest security updates. In particular, ensure that you have installed the latest software, web browser, and Operating System versions.\n�\tIf credential theft is suspected, reset all relevant users passwords.\n�\tBlock communication with relevant URLs or IPs at the organization�s perimeter.",
"category": "DefenseEvasion",
"assignedTo": null,
"alertWebUrl": "https://security.microsoft.com/alerts/da637578995287051192_756343937?tid=b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"incidentWebUrl": "https://security.microsoft.com/incidents/28282?tid=b3c1b5fc-828c-45fa-a1e1-10d74f6d6e9c",
"actorDisplayName": null,
"threatDisplayName": null,
"threatFamilyName": null,
"mitreTechniques": [
"T1564.001"
],
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"lastUpdateDateTime": "2021-05-02T14:19:01.3266667Z",
"resolvedDateTime": null,
"firstActivityDateTime": "2021-04-26T07:45:50.116Z",
"lastActivityDateTime": "2021-05-02T07:56:58.222Z",
"comments": [],
"evidence": [
{
"@odata.type": "#microsoft.graph.security.deviceEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"firstSeenDateTime": "2020-09-12T07:28:32.4321753Z",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"azureAdDeviceId": null,
"deviceDnsName": "tempDns",
"osPlatform": "Windows10",
"osBuild": 22424,
"version": "Other",
"healthStatus": "active",
"riskScore": "medium",
"rbacGroupId": 75,
"rbacGroupName": "UnassignedGroup",
"onboardingStatus": "onboarded",
"defenderAvStatus": "unknown",
"ipInterfaces": [
"1.1.1.1"
],
"loggedOnUsers": [],
"roles": [
"compromised"
],
"detailedRoles": [
"Main device"
],
"tags": [
"Test Machine"
],
"vmMetadata": {
"vmId": "ca1b0d41-5a3b-4d95-b48b-f220aed11d78",
"cloudProvider": "azure",
"resourceId": "/subscriptions/8700d3a3-3bb7-4fbe-a090-488a1ad04161/resourceGroups/WdatpApi-EUS-STG/providers/Microsoft.Compute/virtualMachines/NirLaviTests",
"subscriptionId": "8700d3a3-3bb7-4fbe-a090-488a1ad04161"
}
},
{
"@odata.type": "#microsoft.graph.security.fileEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"detectionStatus": "detected",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"roles": [],
"detailedRoles": [
"Referred in command line"
],
"tags": [],
"fileDetails": {
"sha1": "5f1e8acedc065031aad553b710838eb366cfee9a",
"sha256": "8963a19fb992ad9a76576c5638fd68292cffb9aaac29eb8285f9abf6196a7dec",
"fileName": "MsSense.exe",
"filePath": "C:\\Program Files\\temp",
"fileSize": 6136392,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
}
},
{
"@odata.type": "#microsoft.graph.security.processEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"processId": 4780,
"parentProcessId": 668,
"processCommandLine": "\"MsSense.exe\"",
"processCreationDateTime": "2021-08-12T12:43:19.0772577Z",
"parentProcessCreationDateTime": "2021-08-12T07:39:09.0909239Z",
"detectionStatus": "detected",
"mdeDeviceId": "73e7e2de709dff64ef64b1d0c30e67fab63279db",
"roles": [],
"detailedRoles": [],
"tags": [],
"imageFile": {
"sha1": "5f1e8acedc065031aad553b710838eb366cfee9a",
"sha256": "8963a19fb992ad9a76576c5638fd68292cffb9aaac29eb8285f9abf6196a7dec",
"fileName": "MsSense.exe",
"filePath": "C:\\Program Files\\temp",
"fileSize": 6136392,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
},
"parentProcessImageFile": {
"sha1": null,
"sha256": null,
"fileName": "services.exe",
"filePath": "C:\\Windows\\System32",
"fileSize": 731744,
"filePublisher": "Microsoft Corporation",
"signer": null,
"issuer": null
},
"userAccount": {
"accountName": "SYSTEM",
"domainName": "NT AUTHORITY",
"userSid": "S-1-5-18",
"azureAdUserId": null,
"userPrincipalName": null,
"displayName": "System"
}
},
{
"@odata.type": "#microsoft.graph.security.registryKeyEvidence",
"createdDateTime": "2021-04-27T12:19:27.7211305Z",
"verdict": "unknown",
"remediationStatus": "none",
"remediationStatusDetails": null,
"registryKey": "SYSTEM\\CONTROLSET001\\CONTROL\\WMI\\AUTOLOGGER\\SENSEAUDITLOGGER",
"registryHive": "HKEY_LOCAL_MACHINE",
"roles": [],
"detailedRoles": [],
"tags": []
}
],
"systemTags" : [
"Defender Experts"
],
"additionalData": {
"key1": "value1",
"key2": "value2"
}
}
}
Search for Drive Items
Search the hierarchy of items for items matching a query.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Site Hostname | Jinja-templated text containing the site hostname. Example abc.sharepoint.com | Required |
| Site Name | Jinja-templated text containing the site name. Example Devo-Sample-IncidentResponse | Required |
| File Name | Jinja-templated text containing the file name. | Required |
Output
JSON containing the following items:
{
"has_error": false,
"error": null,
"result": {
"@odata.context": "https://graph.microsoft.com/v1.0/$metadata#Collection(driveItem)",
"value": [
{
"@microsoft.graph.downloadUrl": "https://sample.file.download.url",
"createdBy": {
"user": {
"email": "[email protected]",
"id": "123",
"displayName": "SAMPLE"
}
},
"createdDateTime": "2024-02-18T11:31:43Z",
"eTag": "123",
"id": "01M",
"lastModifiedBy": {
"user": {
"email": "[email protected]",
"id": "123",
"displayName": "SAMPLE"
}
},
"lastModifiedDateTime": "2024-09-18T11:33:56Z",
"name": "filename.csv",
"parentReference": {
"driveType": "documentLibrary",
"driveId": "driveId",
"id": "id",
"name": "Documents",
"path": "/drives/driveId/root:",
"siteId": "steId"
},
"webUrl": "URL",
"cTag": "ctag",
"file": {
"hashes": {
"quickXorHash": "hash"
},
"mimeType": "application"
},
"fileSystemInfo": {
"createdDateTime": "2024-09-18T11:31:43Z",
"lastModifiedDateTime": "2024-09-18T11:33:56Z"
},
"shared": {
"scope": "users"
},
"size": 5005
}
]
}
}
List Group Members
List all members in group with optional filtering, searching, and property selection capabilities.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Group Id | Jinja-templated text containing the group Id | Required |
| Limit | Maximum number of group members to fetch. Maximum allowed is 10000. (Default is 100) | Optional |
| Select Query | Jinja-templated text containing the select query to choose specific user properties. Examples: 'displayName,mail,userPrincipalName' or 'displayName,department,jobTitle' (Default is all properties) | Optional |
| Filter | Jinja-templated text containing the filter query to filter group members. Examples: 'userType eq ''Member''' (exclude guests), 'department eq ''IT''' (specific department), 'startswith(displayName,''John'')' (names starting with John) | Optional |
| Search Query | Jinja-templated text containing the search query to find specific members. Only works on displayName and description properties. Examples: 'displayName:John' (find Johns), 'description:Engineering' (find by description), '"John Smith"' (exact name match) | Optional |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Add Group Member
Add member in group.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Group Id | Jinja-templated text containing the group Id | Required |
| Member Id | Jinja-templated text containing the member Id from directory objects | Required |
Output
JSON containing the following items:
{
"result": {
"message": "Successfully Added the member to group."
},
"error": null,
"has_error":false,
}
Remove Group Members
Remove member from group.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Group Id | Jinja-templated text containing the group Id | Required |
| Member Id | Jinja-templated text containing the member Id from directory objects | Required |
Output
JSON containing the following items:
{
"result": {
"message": "Successfully Removed the member from group."
},
"error": null,
"has_error":false,
}
Create Message
Create a draft of a new message.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) whom you want to update. Example: {{user_principal_name}} | Required |
| Mail Body | Jinja templated JSON containing the mail body in form of graph's message resource type. Example {"subject":"Did you see last night's game?","importance":"Low","body":{"contentType":"HTML","content":"They were awesome!"},"toRecipients":[{"emailAddress":{"address":"[email protected]"}}]} | Required |
| Attachment | Jinja templated string containing one or more file IDs to attachment. (Can be a comma separated string of lhub_file_id values or a json dict in the format of {"<lhub_id>":"<file_name>"}) | Optional |
Output
JSON containing the following items:
{
"result": {
"@odata.context":"https://graph.microsoft.com/v1.0/$metadata#users('94447c6e-ea4c-494c-a9ed-d905e366c5cb')/messages/$entity",
"@odata.etag":"W/\"CQAAABYAAABK4UfANE/UR5clSilZtIuWAAC1vdti\"",
"id":"AAMkADNlNYjSAAA=",
"createdDateTime":"2017-07-22T01:53:56Z",
"lastModifiedDateTime":"2017-07-22T01:53:57Z",
"changeKey":"CQAAABYAAABK4UfANE/UR5clSilZtIuWAAC1vdti",
"categories":[
],
"receivedDateTime":"2017-07-22T01:53:57Z",
"sentDateTime":"2017-07-22T01:53:57Z",
"hasAttachments":false,
"internetMessageId":"<[email protected]>",
"subject":"Did you see last night's game?",
"bodyPreview":"They were awesome!",
"importance":"low",
"parentFolderId":"AAMkADNlNWAAAAAAEPAAA=",
"conversationId":"AAQkADNlNFdXGBnqtY=",
"conversationIndex":"AQHTe7/VAniOJVgCxEmtF1z6ZY1rFQ==",
"isDeliveryReceiptRequested":false,
"isReadReceiptRequested":false,
"isRead":true,
"isDraft":true,
"webLink":"https://outlook.office365.com/owa/?ItemID=AAMkADNlNYjSAAA%3D&exvsurl=1&viewmodel=ReadMessageItem",
"inferenceClassification":"focused",
"body":{
"contentType":"html",
"content":"<html>\r\n<head>\r\n<meta http-equiv=\"Content-Type\" content=\"text/html; charset=utf-8\">\r\n<meta content=\"text/html; charset=us-ascii\">\r\n</head>\r\n<body>\r\nThey were <b>awesome</b>!\r\n</body>\r\n</html>\r\n"
},
"toRecipients":[
{
"emailAddress":{
"name":"Adele Vance",
"address":"[email protected]"
}
}
],
"ccRecipients":[
],
"bccRecipients":[
],
"replyTo":[
]
},
"error": null,
"has_error":false,
}
Create Chat
Create a new chat object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id) of the participating members. Example [email protected],[email protected] | Required |
| Chat Type | Select submission type of chat. | Required |
| Chat topic | Jinja templated string containing the title of the chat. The chat title can be provided only if the chat is of group type. | Optional |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Delete Chat
Soft-delete a chat. When invoked with delegated permissions, this operation only works for tenant admins and Teams service admins.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Chat Id | Jinja templated string containing the chat ID | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
List Messages in Chat.
Retrieve the list of messages in a chat.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Chat Id | Jinja templated string containing the chat ID | Required |
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example [email protected] | Required |
| Chat Query Filter | Jinja templated text containing the query filter. Example: '$top=2&$orderby=lastModifiedDateTime desc&$filter=lastModifiedDateTime gt 2022-09-22T00:00:00.000Z and lastModifiedDateTime lt 2022-09-24T00:00:00.000Z' | Optional |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Get Message in Chat.
Retrieve the list of messages in a chat.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Chat Id | Jinja templated string containing the chat ID | Required |
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example [email protected] | Required |
| Message Id | Jinja templated text containing the message ID | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Send Message in Chat.
Send a new chat message in the specified chat.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Chat Id | Jinja templated string containing the chat ID | Required |
| User's principal name or user's unique identifier(id) | Jinja-templated text containing the user's principal name or user's unique identifier(id). Example [email protected] | Required |
| Message | Jinja templated text containing the message. Example: 'Hello!' | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
List Incident.
Get a list of incident objects that Microsoft 365 Defender created to track attacks in an organization.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Query Filter | Jinja templated text containing the filter. Example: '$filter={property}+eq+'{property-value}'' | Optional |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Get Incident.
Retrieve the properties and relationships of an incident object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja templated text containing the incident ID. Example: {incidentId} | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Create Comment on Incident.
Create a comment for an existing incident based on the specified incident id.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja templated text containing the incident ID. Example: {incidentId} | Required |
| Comment | Jinja templated text containing the comment. Example: 'Demo for docs' | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Update Incident.
Update the properties of an incident object.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja templated text containing the incident ID. Example: {incidentId} | Required |
| Assigned To | Jinja templated text containing the assignee. Example: {assignee} | Required |
| Classification | Jinja templated text containing the specification for the incident. Possible values are: unknown, falsePositive, truePositive, informationalExpectedActivity, unknownFutureValue. | Required |
| Determination | Jinja templated text containing the determination of the incident. Possible values are: unknown, apt, malware, securityPersonnel, securityTesting, unwantedSoftware, other, multiStagedAttack, compromisedAccount, phishing, maliciousUserActivity, notMalicious, notEnoughDataToValidate, confirmedUserActivity, lineOfBusinessApplication, unknownFutureValue. | Required |
| Status | Jinja templated text containing the status of the incident. Possible values are: active, resolved, redirected, unknownFutureValue. | Required |
| Custom Tags | Jinja templated JSON containing the array of custom tags associated with an incident. | Required |
| Summary | Jinja templated text containing the summary. Example: {summary} | Required |
| Resolving Comment | Jinja templated text containing the resolution of the incident. | Required |
| Severity | Jinja templated text containing the severity. Possible values are: unknown, informational, low, medium, high, unknownFutureValue. | Required |
| Display Name | Jinja templated text containing the display name. | Required |
| Description | Jinja templated text containing the description. | Required |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Graph Explorer
Make arbitrary HTTP requests to Microsoft Graph API endpoints.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| HTTP Method | HTTP method for the request | Required |
| URL | Complete Microsoft Graph API URL (e.g., 'https://graph.microsoft.com/v1.0/users', 'https://graph.microsoft.com/beta/security/alerts'). | Required |
| Query Parameters | JSON object containing query parameters (e.g., {"$filter": "displayName eq 'value'", "$top": 10}). Supports column templating. | Optional |
| Request Body | JSON request body for POST, PUT, PATCH requests. | Optional |
| Response Format | How to format the response data | Optional |
| Result Limit | Maximum number of results to return for GET requests. Default is 100 and maximum allowed value is 5000 | Optional |
| Time between consecutive API requests (in millis) | Time to wait between consecutive API requests in milliseconds (Default is 0 millisecond) | Optional |
Output
JSON containing the following items:
{
"result": {},
"error": null,
"has_error":false,
}
Release Notes
v3.14.4- Added new action microsoft graph explorerv3.14.1- Minor Bug fixes.v3.14.0- Added new Chat and Incident actions.v3.13.9- Bug fixv3.13.4- Added support with optional filtering & searching inList Groups Membersactionv3.13.2- AddedAttachmentfield inCreate Messageactionv3.13.1- Unmasked client IDv3.13.0- Added new actions:List Group Members,Add Group Member,Remove Group MembersandCreate Messagev3.11.4- Bug fix for Python3 compatible issue at the connection levelv3.11.1- Added new actionSearch for Drive Itemsv3.11.0- Added 4 new actionsList Alerts,Get Alert,Create Comment for AlertandUpdate Alertv3.10.1- Added 9 new actionsList Message Rule,Get Message Rule,Create Message Rule,Update Message Rule,Delete Message Rule,List Devices,Get Device,List Register Owner of DeviceandList Register Users of Devicev3.8.1- Added optional params of body in actionCreate reply all.v3.8.0- Added new actionSend Draft.v3.7.1- Added new actionAdd attachment.v3.6.5- Added new actionList users V2with jinja support.v3.6.4- Bug Fix for filter functionality inList usersaction.v3.6.2- Added 2 new actions:Reply AllandCreate Reply Allv3.5.1- Added Select Query field in 2 actions:List UsersandGet Userv3.4.0- Added 2 new actions:Get User Registration DetailsandGet User Mailbox Settingsv3.3.1- Added 21 new actions:List Password Methods,Get Password Method,List Phone Methods,Get Phone Method,Delete Phone Method,Update Phone Method,Add Phone Method,Enable SMS Sign-in,Disable SMS Sign-in,List Microsoft Authenticator Methods,Get Microsoft Authenticator Method,Delete Microsoft Authenticator Method,List FIDO2 Authentication Method,Get FIDO2 Authentication Method,Delete FIDO2 Authenticator Method,List Software OATH Authentication Method,Get Software OATH Authentication Method,Delete Software OATH Authentication Method,List Windows Hello for Business Authentication Method,Get Windows Hello for Business Authentication MethodandDelete Windows Hello for Business Authentication Method.v3.2.3- Bug fix -List Useraction not working.v3.1.1- Bug fix inList Messageaction: Limited Mailbox Folder listing.v3.1.0- Added 1 new action:Update User.v3.0.0- Updated architecture to support IO via filesystemv2.2.0- Added 1 new action :Revoke Sign-in Sessions.v2.1.0- Added BCC optional field inSend Messageaction and bug fix for unusual behaviour of OData queries inList Messageaction.v2.0.4- Bug fix - Download Attachment if ContentBytes is not present in the attachment forList Messagesaction.v1.5.7- Bug fix - support of nested folders inMove MessageandList Messagesaction.v1.5.6- Bug fix - encoding issue in mail's header.v1.5.5- Bug fix - handled case for not returning file id for some type of attachments.v1.5.4- Added 3 actions:Send Message,List MessagesandMove Message, deprecated oldList Messagesaction.
Updated 5 months ago