Bitdefender
Version: 2.0.0
Bitdefender provides anti-virus software, internet security software, endpoint security software, and other cyber security products and services.
Connect with Bitdefender with LogicHub
- Navigate to Automations > Integrations.
- Search for Bitdefender.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- URL: The URL to connect to the Bitdefender.
- API Key: The API Key to connect to the Bitdefender.
- After you've entered all the details, click Connect.
Actions for Bitdefender
Get Reports List
Retrieves the list of scheduled reports.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Report Name | Enter the value for name of report. | Optional |
| Report Type | Select the type of report (Default is All). | Optional |
| Maximum Results | Maximum number of events to return as response to this call (default is 100,000). | Optional |
Output
A JSON object containing following items:
- has_error: True/False
- error: message/null
- result: List of reports
{
"error": null,
"has_error": false,
"id": "5ea7217a7289817dd601c44",
"name": "Audit Report",
"occurrence": 6,
"type": 67
}
Download Report by ID
Downloads the report by ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Report Name | Jinja-templated text containing the id of report. | Required |
| Instance URL Type | Select type of instance url (Default is Last Instance URL). | Optional |
| File Type | Select type of file to download (Default is both CSV and PDF). | Optional |
| Automatically Parse CSV Files | Select the value to automatically parse CSV files (Default is True). | Optional |
| Header Names | If a CSV file will not have headers, provide a comma-separated list of headers to use (Default is File Headers). | Optional |
| Columns to Keep | If you only need specific columns, provide a comma-separated list of column names, and the rest will be dropped from the results (Default is All Columns). | Optional |
| Automatically Stripping Out All Non-ascii Characters | Select the value to automatically stripping out all non-ascii characters (Default is False). | Optional |
Output
JSON containing following items:
- has_error: True/False
- error: message/null
- result: File Details.
{
"result": {
"csv": {
"lhub_file_id": "8e7902669baa74c5435ea9e68.csv",
"original_file_name": "Activity Report-2020-02-04 02-09-08.csv"
},
"pdf": {
"lhub_file_id": "85cb9f94fefbe96a7a52d7b7a15.pdf",
"original_file_name": " Activity Report-2020-02-04 02-09-08.pdf"
}
},
"error": null,
"has_error": false
}
Download Report by Name
Downloads the report by name.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Report Name | Jinja-templated text containing the name of report. | Required |
| Instance URL Type | Select type of instance url (Default is Last Instance URL). | Optional |
| File Type | Select type of file to download (Default is both CSV and PDF). | Optional |
| Automatically Parse CSV Files | Select the value to automatically parse CSV files (Default is True). | Optional |
| Header Names | If a CSV file will not have headers, provide a comma-separated list of headers to use (Default is File Headers). | Optional |
| Columns to Keep | If you only need specific columns, provide a comma-separated list of column names, and the rest will be dropped from the results (Default is All Columns). | Optional |
| Automatically Stripping Out All Non-ascii Characters | Select the value to automatically stripping out all non-ascii characters (Default is False). | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: File Details.
{
"result": {
"csv": {
"lhub_file_id": "8e7902669baa74c5435ea9e68.csv",
"original_file_name": "Activity Report-2020-02-04 02-09-08.csv"
},
"pdf": {
"lhub_file_id": "85cb9f94fefbe96a7a52d7b7a15.pdf",
"original_file_name": " Activity Report-2020-02-04 02-09-08.pdf"
}
},
"error": null,
"has_error": false
}
Get Quarantine List
Retrieves the quarantine list from the instance.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Service Name | Select the name of the service (Default is Computers and Virtual Machines). | Optional |
| Endpoint ID | Select column that contains the ID of the computer for which you want to retrieve the quarantined items. If not passed, the action returns the items quarantined in the entire network. | Optional |
| Filters | Jinja Template for filters to be used when querying the quarantine items list. Example {"threatName":"{{threat_column_name}}"}. | Optional |
| Maximum Results | Maximum number of events to return as a response to this call (default is 100,000). | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Quarantine List
{
"actionStatus": 0,
"canBeRemoved": true,
"canBeRestored": true,
"companyId": "5ca593a8765368039301e156",
"details": {
"filePath": "/samples/classic/c100.php"
},
"endpointIP": "192.168.2.34",
"endpointId": "",
"endpointName": "ep_OS",
"error": null,
"has_error": false,
"id": "5cb4ff789817c004cf6e3df3",
"quarantinedOn": "2019-04-19T03:36:45",
"threatName": "Backdoor.PHP.AMB"
}
Create Scan Task
This method creates a new scan task.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Target IDs | Jinja-templated query containing comma separated list with the IDs of the targets to scan. The target ID can designate an endpoint or a container. | Required |
| Name | Jinja-templated text for name of the task. | Required |
| Type | Select option for type. (Default is Full Scan). | Required |
| Custom Scan Settings | Jinja-templated query containing custom scan settings containing information such as scan depth and scan path(s). This should be set only when 'Type' parameter has value '4 - Custom Scan'. When set for other types, the values will be ignored. Parameter $customScanSettings must contain the following properties: int $scanDepth The scan profile. Available options: 1- aggressive; 2-normal; 3- permissive;, and array $scanPath The list of target paths to be scanned. Example: {"scanDepth":1,"scanPath":["LocalDrives"]} | Required |
To get Target ID and Mac ID please use inspect element feature of google chrome.
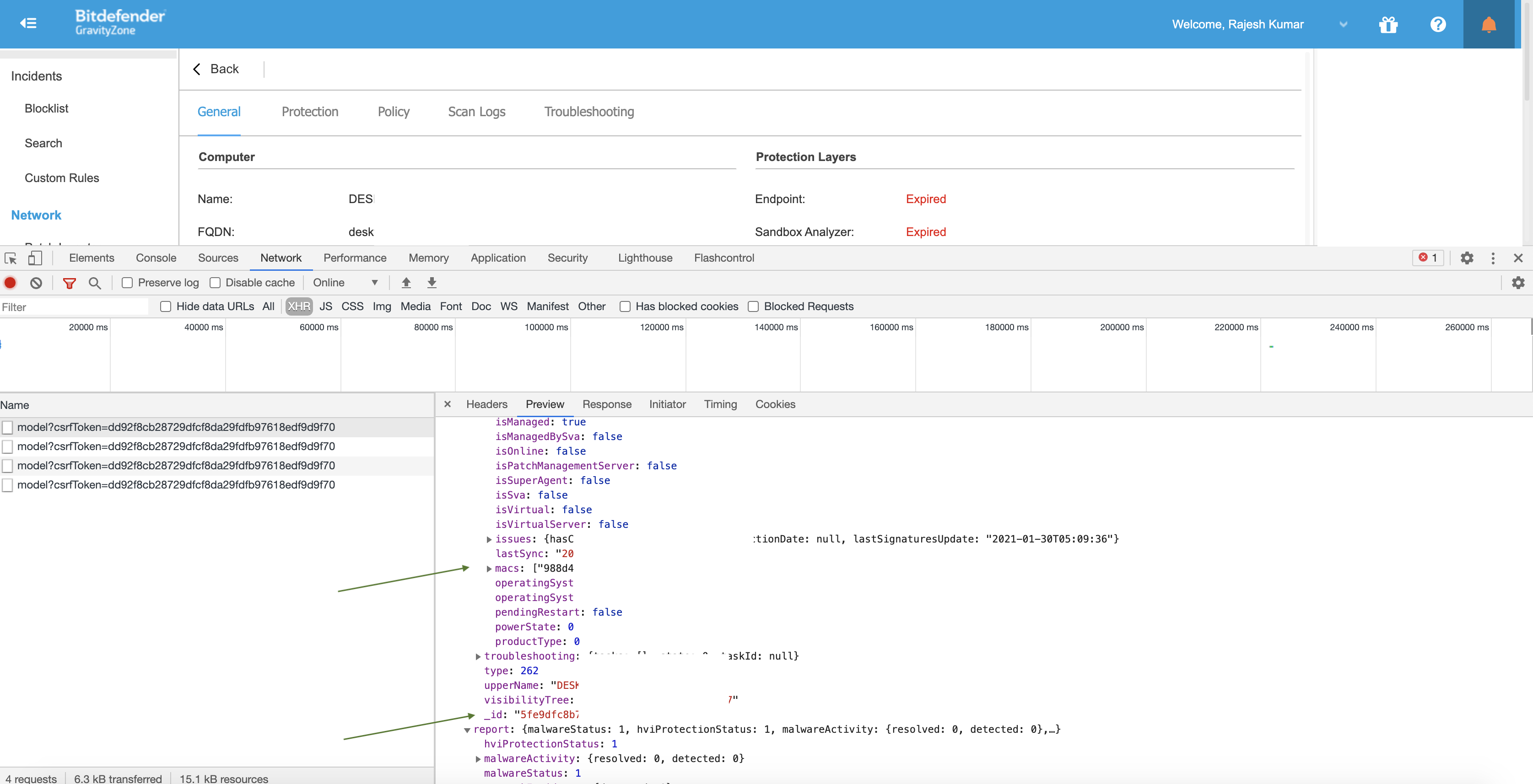
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: True/False
{
"result": {
"id": "787b5e36-89a8-4353-88b9-6b7a32e9c87g",
"jsonrpc": "2.0",
"result": true
},
"error": null,
"has_error": false
}
Create Scan Task By MAC
Use this method to generate a scan task for managed endpoints identified by their MAC address.
Input Field
| Input Name | Description | Required |
|---|---|---|
| MAC Addresses | Jinja-templated query containing comma separated list of MAC addresses of the endpoints to be scanned. You can specify at most 100 MAC addresses at once. | Required |
| Name | Jinja-templated text for name of the task. | Optional |
| Type | Select option for type. (Default is Full Scan). | Optional |
| Custom Scan Settings | Jinja-templated query containing custom scan settings containing information such as scan depth and scan path(s). This should be set only when 'Type' parameter has value '4 - Custom Scan'. When set for other types, the values will be ignored. Parameter $customScanSettings must contain the following properties: int $scanDepth The scan profile. Available options: 1- aggressive; 2-normal; 3- permissive;, and array $scanPath The list of target paths to be scanned. Example: {"scanDepth":1,"scanPath":["LocalDrives"]} | Required |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: True/False
{
"result": {
"id": "787b5e36-89a8-4353-88b9-6b7a32e9c87g",
"jsonrpc": "2.0",
"result": true
},
"error": null,
"has_error": false
}
Get Scan Tasks List
This method returns the list of scan tasks.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Name | Jinja-templated query containing name of the task. Filter the list of tasks by task name. Use the asterisk symbol(*) in front of the keyword to search its appearance anywhere in the name. If omitted, only results where the name starts with the keyword will be returned. | Required |
| Status | Select option for status. (Default is All). | Optional |
| Maximum Results | Maximum number of events to return as response to this call (default is 100,000). | Optional |
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Tasks List
{
"error": null,
"has_error": false,
"id": "601ad4557481acf63696a",
"name": "Task1",
"startDate": "2020-02-03T10:50:29",
"status": 1
}
Release Notes
v2.0.0- Updated architecture to support IO via filesystem
Updated over 2 years ago