Anomali
Version: 4.0.14
Anomali is a Threat Intelligence Platform that enables businesses to integrate security products and leverage threat data to defend against cyber threats.
Connect Anomali with LogicHub
- Navigate to Automations > Integrations.
- Search for Anomali.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- Base URL (Optional): Leave Empty For Default): Specify the base URL of the Anomali server. Leave empty for default Anomali server. Example: https://192.168.1.1:443 or https://yourhostname.example.com.
- API Key: API key for connecting to Anomali.
- Username: Username for connecting to Anomali.
- After you've entered all the details, click Connect.
Actions for Anomali
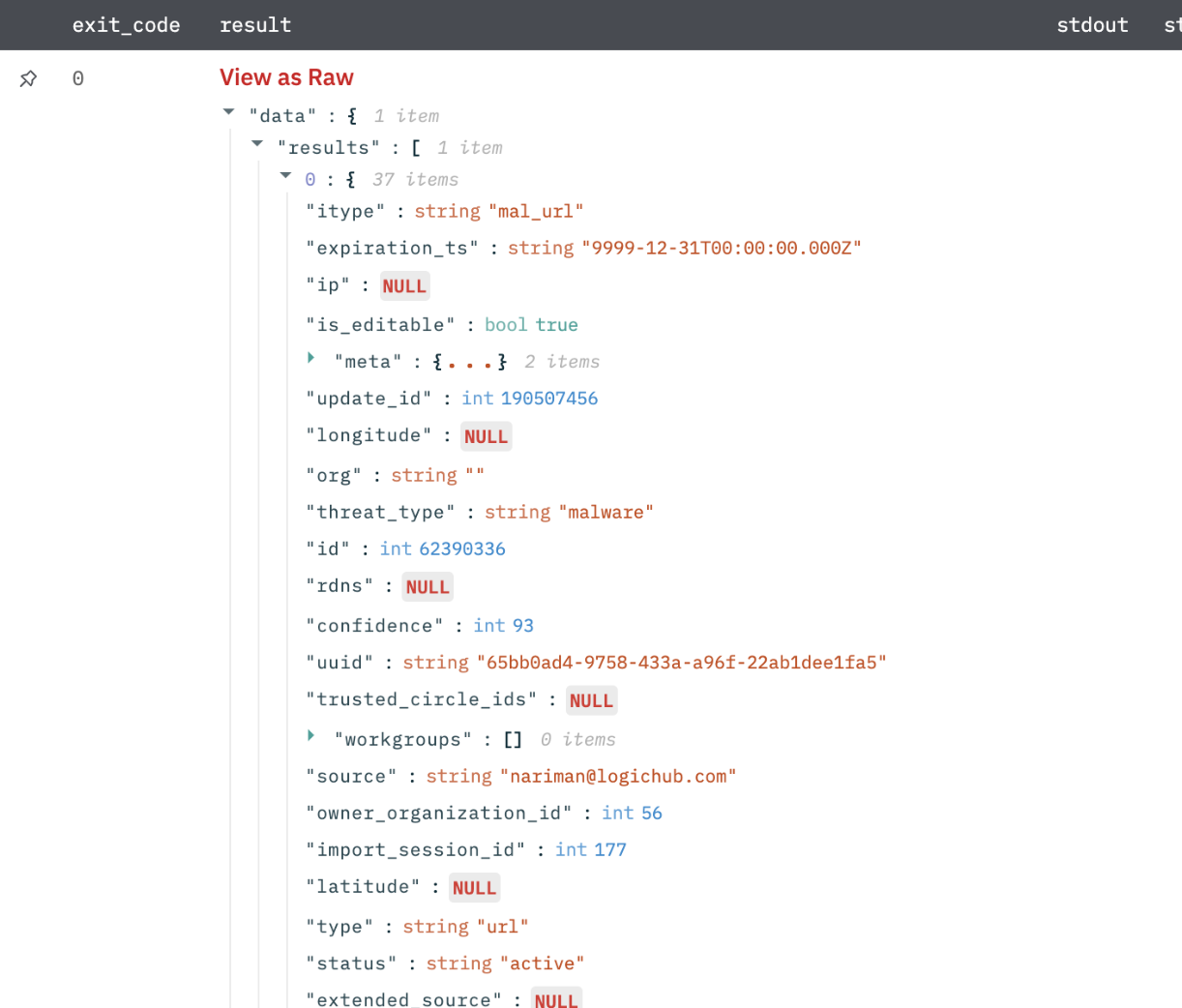
URL Scan
Submits a URL or IP address to Anomali for lookup against their threat intelligence database. Based on the results, automate how Incident Response is handled.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Column name | Column name from the parent table containing URL. | Required |
Output
Scan results in JSON format.
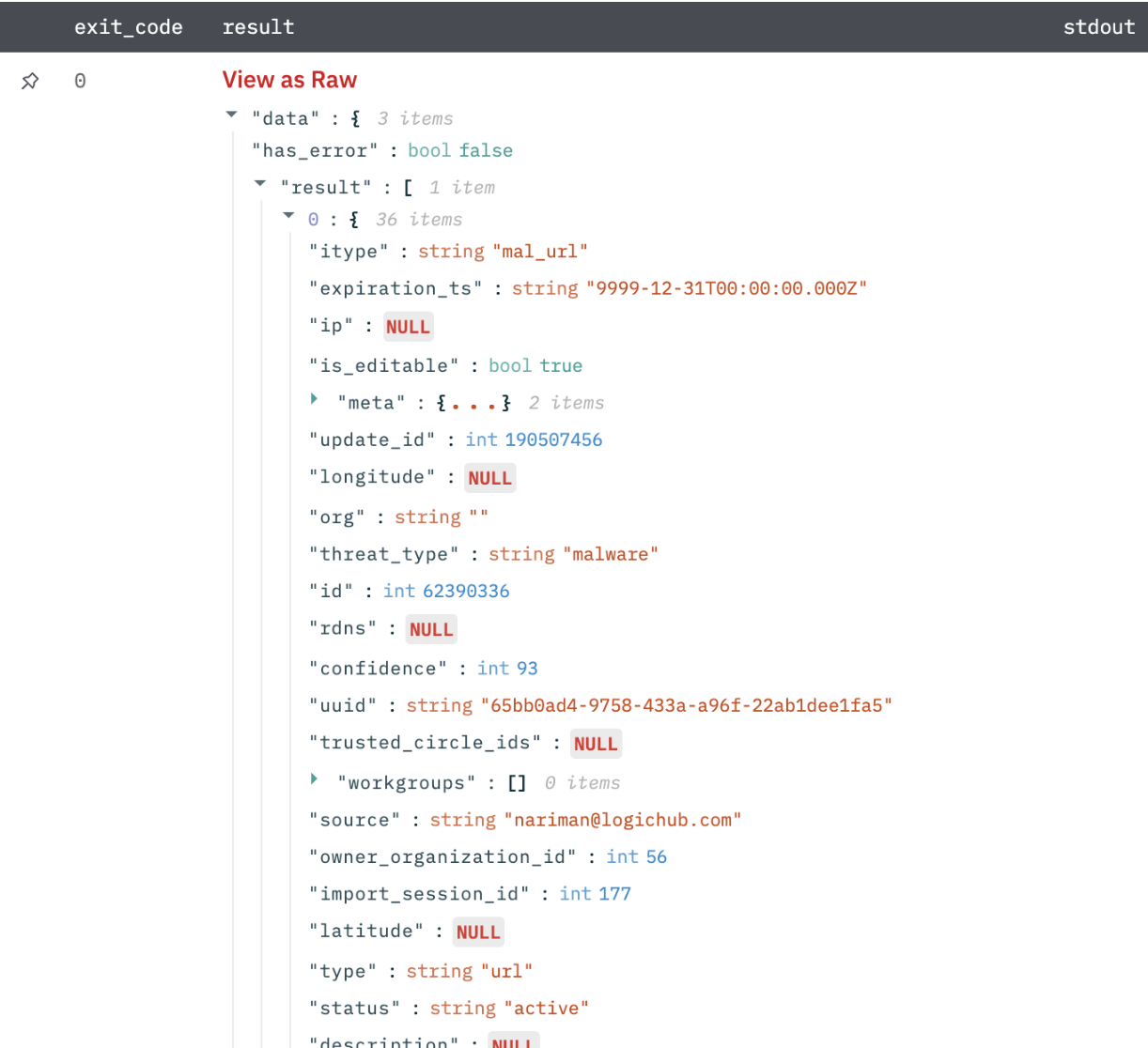
Get Reputation
Submits a URL/ IP/ Domain/ md5 of a file/email address to Anomali for lookup against their threat intelligence database. Based on the results, automate how Incident Response is handled.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Observable Column name | Column name from parent table containing observable such as IP address/domain/URL and so on. | Required |
| Select Observable Type | URL/ IP/ Domain/ md5 of a file/email | Required |
Output
Reputation results in JSON format.
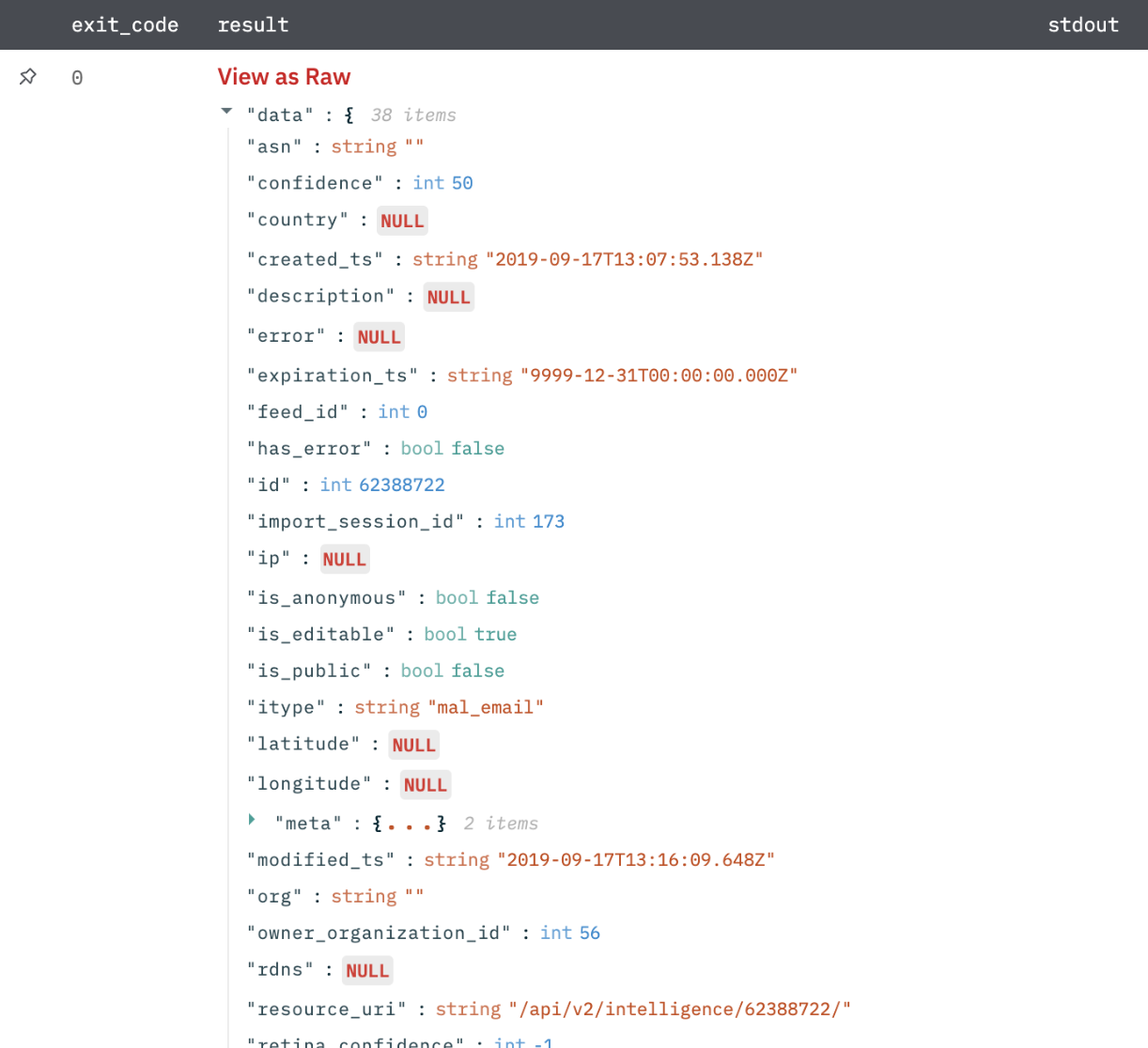
Get Intelligence
Get intelligence from Threatstream. You can specify the criteria by which the intelligence should be retrieved.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Jinja Template For Filter Criteria | Provide jinja-template for filter Criteria. Example: q=(confidence>={{confidencevalue}}+AND+(itype="apt_ip"+OR+itype="bot ip"+OR+itype="c2_ip")) | Required |
| Explode Results | Select whether to return separate rows for each result or a single row containing all results. Default is Separate Rows. | Optional |
Output
Intelligence search results in JSON format.
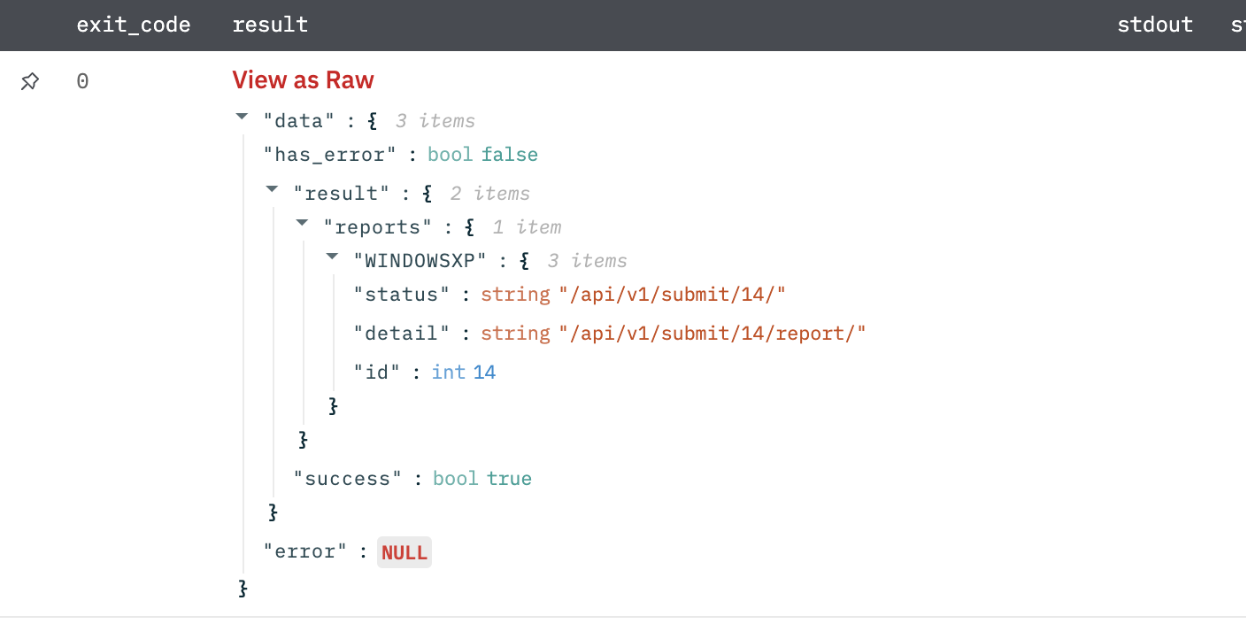
Submit File or URL
Submit files or URLs to the ThreatStream-hosted Sandbox.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Submission Column Name | Column name from parent table that contains file or URL. | Required |
| Sandbox Submission Type | Select File / URL. | Required |
| Select Platform | Platform on which the submitted URL or file will be run. Example: WINDOWS7 / WINDOWSXP. | |
| Sandbox Submission Classification | Classification of the Sandbox submission—public or private. Default is private. | Optional |
| Use Premium Sandbox | Specify whether the premium sandbox should be used for detonation. Default is False. | Optional |
| Jinja Template for Detail | Jinja Template for a comma-separated list that provides additional details for the indicator. This information is displayed in the Tag column of the ThreatStream UI. Example: {{tag1}},{{tag2}} | Optional |
Output
Submission results in JSON format.
Get Submission Status
Get the status of the submitted file or URL.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Submission Id Column Name | Column name from parent table that contains submission ID. | Required |
| Should Wait | Should wait till status is done. Default is False. By default, it will return the current status. | Optional |
Output
Status results in JSON format.
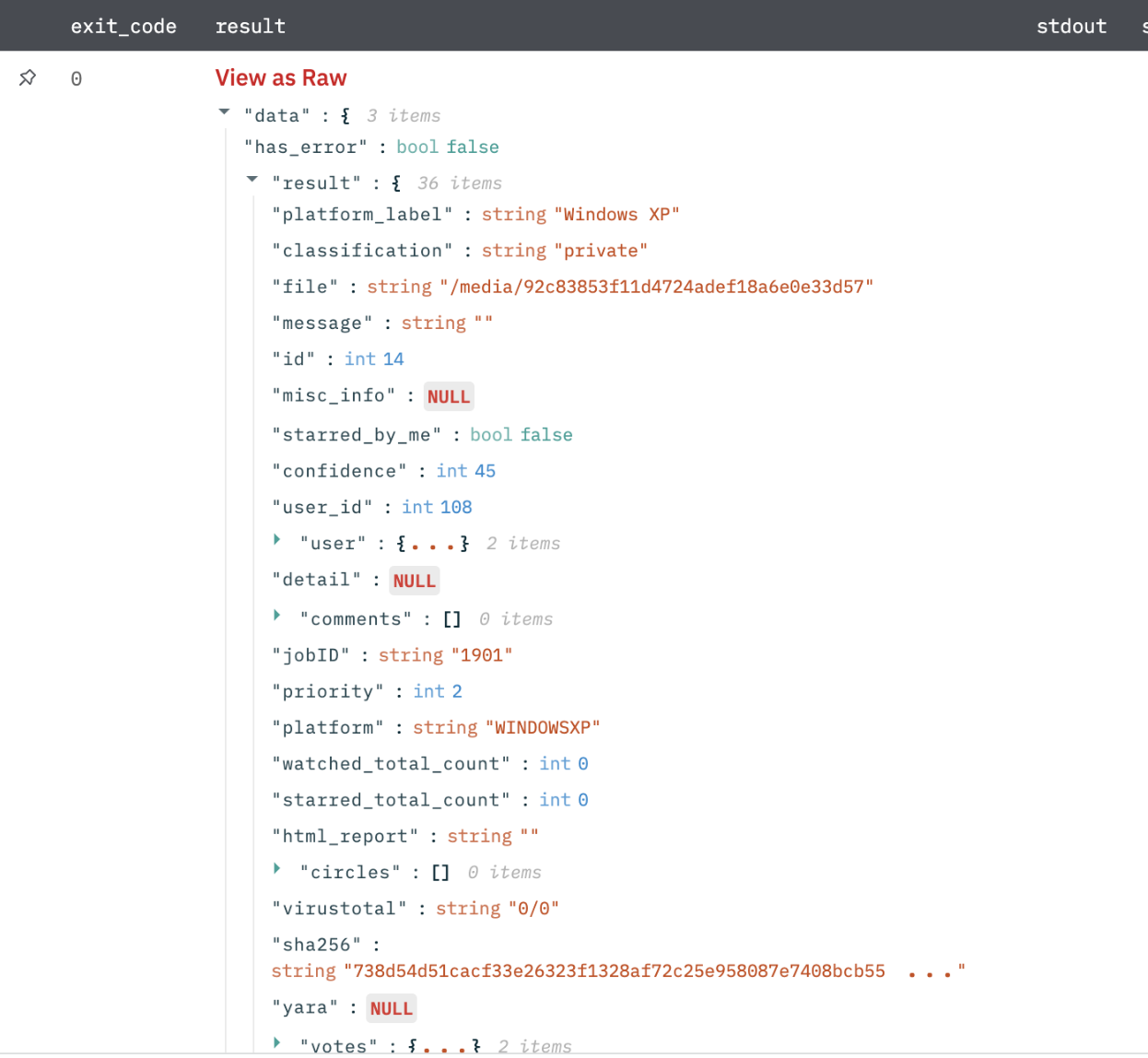
Get Submission Report
Get a submission report of the submitted file or URL.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Submission Id Column Name | Column name from parent table that contains submission ID. | Required |
| Should Wait | Should wait till the report is generated. Default is False. | Optional |
Output
Report data in JSON format.
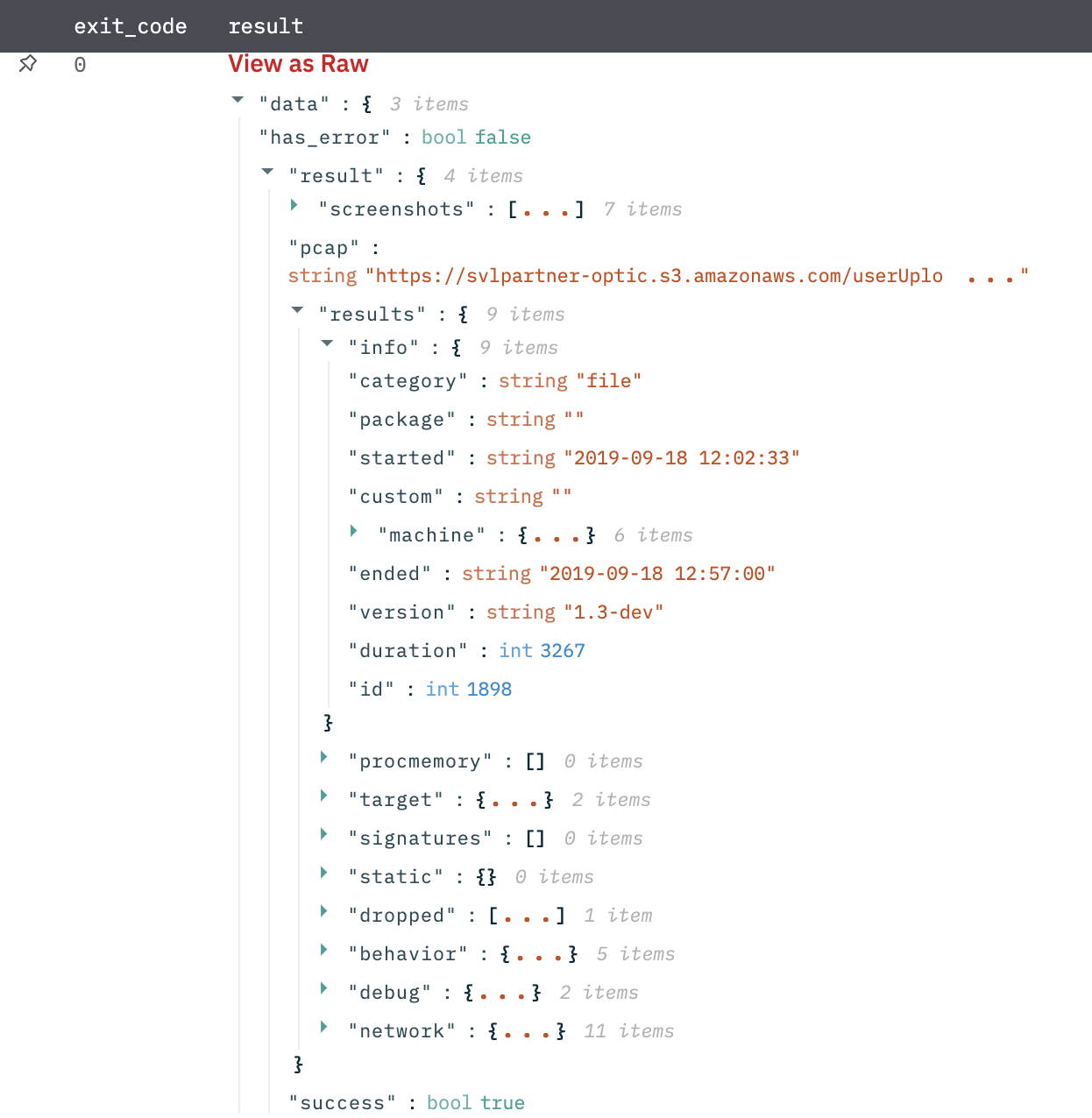
Create Threat Model Entity
Create threat model entities that is, actors, campaigns, incidents, signatures, TTPs, and vulnerabilities.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Entity Name Column Name | Column name from parent table that contains entity name. The name should be unique for an entity. | Required |
| Model Entity Type | Select a model entity type. Example: Actor, Campaign, Incident, and so on. | Required |
| Is Public | Whether the entity is public or private. Default is False. | Required |
| TLP Column Name | Column name from parent table that contains TLP. TLP is the Traffic Light Protocol designation for the entity i.e. Red, Amber, Green, White. | Optional |
| Jinja Template For Description | Jinja Template for description. Example: This is sample {{desc}}. | Optional |
| Jinja Template For Tags | Jinja Template for comma-separated list of tags. Example: {{tag1}},{{tag2}}. | Optional |
| Jinja Template For Additional Param in Json Format | Jinja Template for additional parameters in JSON format. Example: {"intelligence": [{{intelligence_id_list}}]}. | Optional |
Output
A JSON object containing multiple rows of results:
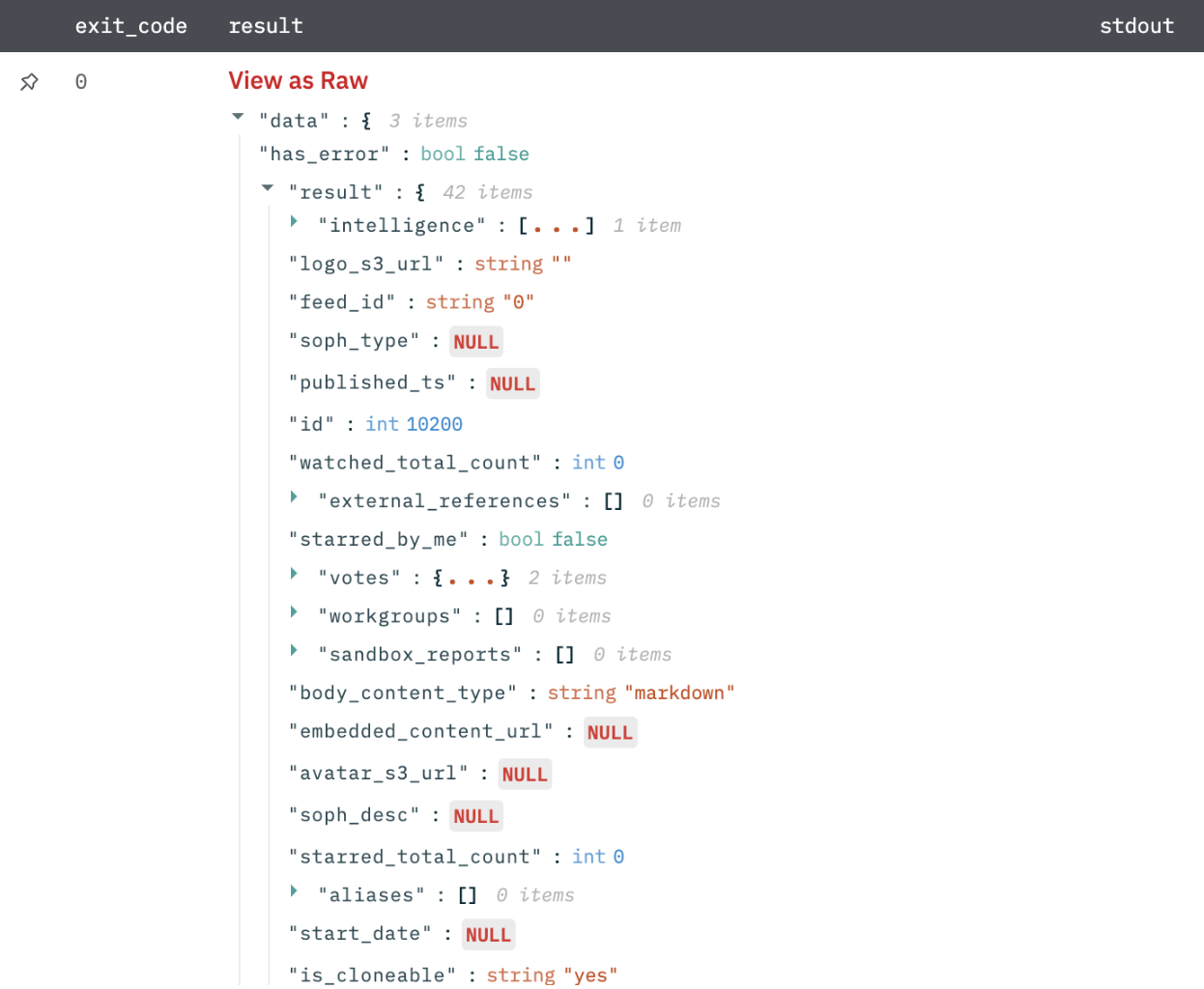
Update Threat Model Entity
Update threat model entities that are, actors, campaigns, incidents, signatures, TTPs, and vulnerabilities.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Entity Id Column Name | Column name from parent table that contains entity ID. | Required |
| Model Entity Type | Select a model entity type. Example: Actor, Campaign, Incident, and so on. | Required |
| Entity Name Column Name | Column name from parent table that contains entity name. The name should be unique for an entity. | Optional |
| TLP Column Name | Column name from parent table that contains TLP. TLP is Traffic Light Protocol designation for the entity that is, red, amber, green, white. | Optional |
| Jinja Template For Description | Jinja Template for description. Example: This is sample {{desc}} | Required |
| Jinja Template For Tags | Jinja Template for comma-separated list of tags. Example: {{tag1}},{{tag2}} | Optional |
| Jinja Template For Additional Param in Json Format) | Jinja Template for additional parameters in json format. Example: {"intelligence": [{{intelligence_id_list}}] } | Optional |
Output
A JSON object containing multiple rows of results:
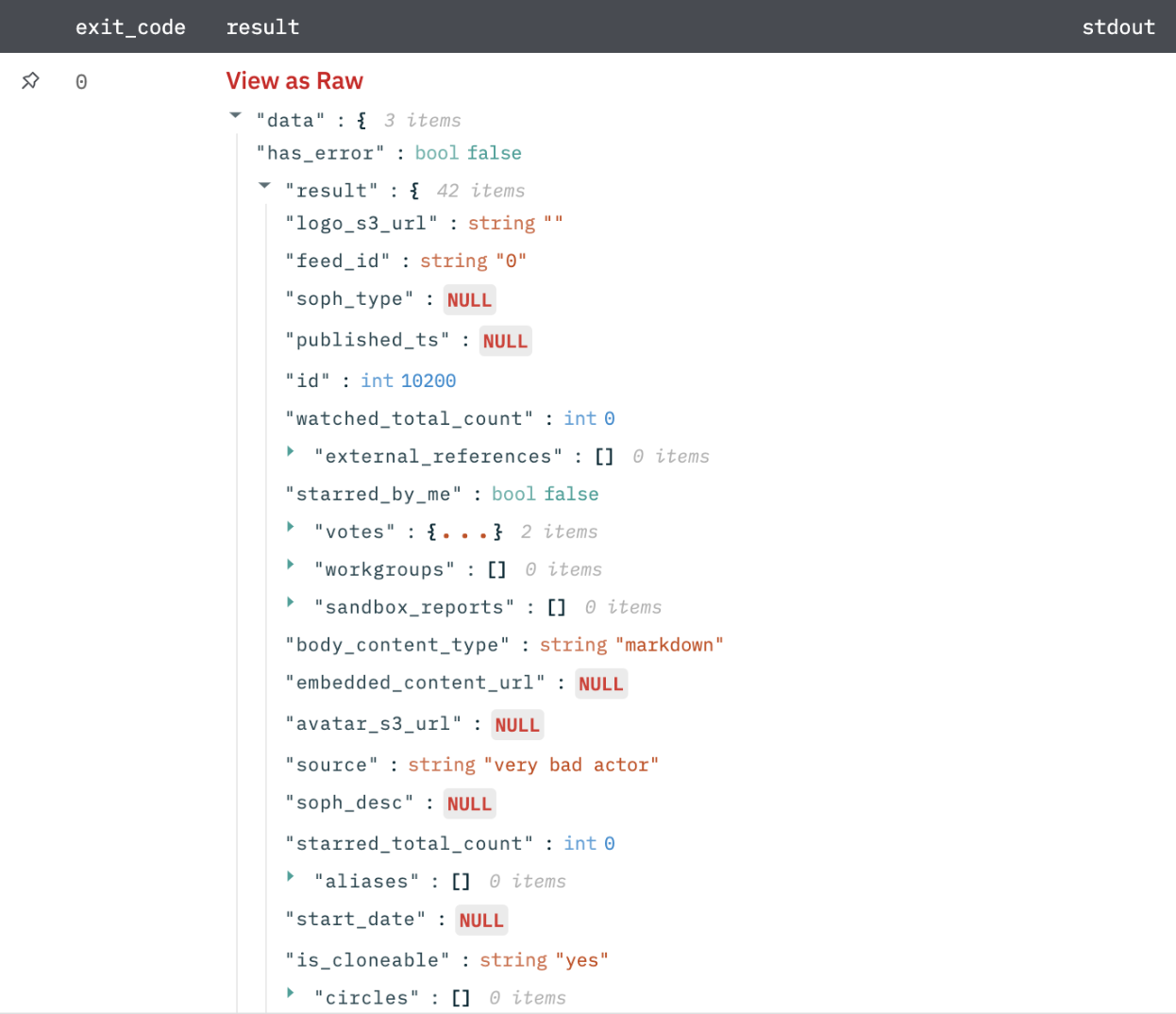
Get List of Models
Get list of threat model entities that is, actors, campaigns, incidents, signatures, TTPs, and vulnerabilities.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Model Entity Type | Select a model entity type. Example: Actor, Campaign, Incident, and so on. | Required |
| Jinja template for filters in JSON Format | Provide Jinja template for filters in JSON format. Example: {"tlp":"{{tlp}}"} | Optional |
| Explode Results | Select whether to return separate rows for each result or a single row containing all results. Default is Separate Rows. | Optional |
Output
A JSON object containing multiple rows of results:
Get Model Description
Get details of model entities that is, actors, campaigns, incidents, signatures, TTPs, and vulnerabilities.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Entity Id Column Name | Column name from parent table that contains entity ID. | Required |
| Model Entity Type | Select a model entity type. Example: Actor, Campaign, Incident, and so on. | Required |
Output
A JSON object containing multiple rows of results:
Import With Manual Approval
Import threat data (observables) into ThreatStream and require the approval of the imported data through the ThreatStream UI.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| File Id | Column name from parent table that contains file id. | Required |
| Classification | Select a classification of the observable (default is Private). | Optional |
| Severity | Select severity of the observable (default is Low). | Optional |
| Source Confidence Weight | The ratio between the amount of the source confidence of each observable and the ThreatStream confidence (default is 100). | Optional |
| Confidence | Level of certainty that an observable is of the reported indicator type (default is 100). | Optional |
| IP Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_ip). | Optional |
| Domain Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_domain). | Optional |
| URL Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_url). | Optional |
| Email Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_email). | Optional |
| MD5 Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_md5). | Optional |
| Trusted Circles | Comma-separated IDs of the trusted circle to which this threat data should be imported (default is no association). | Optional |
Output
A JSON object containing multiple rows of results:
Import With Manual Approval V2
Import threat data (observables) into ThreatStream and require the approval of the imported data through the ThreatStream UI.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| File Id | Jinja-templated text for the file id. Example: {{file_id}} | Optional |
| Classification | Select a classification of the observable (default is Private). | Optional |
| Severity | Select severity of the observable (default is Low). | Optional |
| Source Confidence Weight | Jinja-templated number containing the ratio between the amount of the source confidence of each observable and the ThreatStream confidence. | Optional |
| Confidence | Jinja-templated number containing the level of certainty that an observable is of the reported indicator type (default is 100). | Optional |
| IP Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_ip). | Optional |
| Domain Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_domain). | Optional |
| URL Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_url). | Optional |
| Email Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_email). | Optional |
| MD5 Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_md5). | Optional |
| Threat Type | Jinja-templated text containing the Type of threat associated with the imported observables. (Default is malware_md5) | Optional |
| TLP | Jinja-templated text containing the Traffic Light Protocol designation for the intelligence. | Optional |
| Intelligence Source | Jinja-templated text containing the Source from which the intelligence originated. | Optional |
| Expiration TS | Jinja-templated text containing the Time stamp of when intelligence will expire on ThreatStream, in UTC format. For example, 2017-01-26T00:00:00 (Default is 90 days from the current date and if you want to set it as never then leave this blank and select the never option down below) | Optional |
| Trusted Circles | Jinja-templated text containing the Comma-separated IDs of the trusted circle to which this threat data should be imported (default is no association). | Optional |
| Tags | Jinja-templated JSON containing the Comma-separated JSON object for tags. Example [{"name": "my_tag", "tlp": "red"},{"name":"my_tag2"}]. Note : Adding public tags may be restricted by your org admin | Optional |
| Set Expiration to never | Select if expiration should be set to never. (Default is No) | Optional |
Output
A JSON object containing multiple rows of results:

Import With Manual Approval V3
Import threat data (observables) into ThreatStream and require the approval of the imported data through the ThreatStream UI.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| File Id | Jinja-templated text for the file id. Example: {{file_id}} | Optional |
| Classification | Select a classification of the observable (default is Private). | Optional |
| Severity | Select severity of the observable (default is Low). | Optional |
| Source Confidence Weight | Jinja-templated number containing the ratio between the amount of the source confidence of each observable and the ThreatStream confidence. | Optional |
| Confidence | Jinja-templated number containing the level of certainty that an observable is of the reported indicator type (default is 100). | Optional |
| IP Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_ip). | Optional |
| Domain Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_domain). | Optional |
| URL Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_url). | Optional |
| Email Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_email). | Optional |
| MD5 Mapping | Jinja-templated text containing the Indicator type to assign if a specific type is not associated with an observable (default is mal_md5). | Optional |
| Threat Type | Jinja-templated text containing the Type of threat associated with the imported observables. (Default is malware_md5) | Optional |
| TLP | Jinja-templated text containing the Traffic Light Protocol designation for the intelligence. | Optional |
| Intelligence Source | Jinja-templated text containing the Source from which the intelligence originated. | Optional |
| Expiration TS | Jinja-templated text containing the Time stamp of when intelligence will expire on ThreatStream, in UTC format. For example, 2017-01-26T00:00:00 (Default is 90 days from the current date and if you want to set it as never then leave this blank and select the never option down below) | Optional |
| Trusted Circles | Jinja-templated text containing the Comma-separated IDs of the trusted circle to which this threat data should be imported (default is no association). | Optional |
| Tags | Jinja-templated JSON containing the Comma-separated JSON object for tags. Example [{"name": "my_tag", "tlp": "red"},{"name":"my_tag2"}]. Note : Adding public tags may be restricted by your org admin | Optional |
| Set Expiration to never | Select if expiration should be set to never. (Default is No) | Optional |
Output
A JSON object containing multiple rows of results:

Import Without Manual Approval
Import threat data (observables) into ThreatStream without the approval of the imported data through the ThreatStream UI.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| File Id | Column name from parent table that contains entity ID. | Required |
| Classification | Select a classification of the observable (default is Private). | Optional |
| Severity | Select severity of the observable (default is Low). | Optional |
| Source Confidence Weight | The ratio between the amount of the source confidence of each observable and the ThreatStream confidence (default is 100). | Optional |
| Confidence | Level of certainty that an observable is of the reported indicator type (default is 100). | Optional |
| IP Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_ip). | Optional |
| Domain Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_domain). | Optional |
| URL Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_url). | Optional |
| Email Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_email). | Optional |
| MD5 Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_md5). | Optional |
| Trusted Circles | Comma-separated IDs of the trusted circle to which this threat data should be imported (default is no association). | Optional |
Output
A JSON object containing multiple rows of results:
Import Without Manual Approval V2
Import threat data (observables) into ThreatStream without the approval of the imported data through the ThreatStream UI.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| File Id | Column name from parent table that contains entity ID. | Required |
| Classification | Select a classification of the observable (default is Private). | Optional |
| Severity | Select severity of the observable (default is Low). | Optional |
| Source Confidence Weight | The ratio between the amount of the source confidence of each observable and the ThreatStream confidence (default is 100). | Optional |
| Confidence | Level of certainty that an observable is of the reported indicator type (default is 100). | Optional |
| IP Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_ip). | Optional |
| Domain Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_domain). | Optional |
| URL Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_url). | Optional |
| Email Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_email). | Optional |
| MD5 Mapping | Indicator type to assign if a specific type is not associated with an observable (default is mal_md5). | Optional |
| Trusted Circles | Comma-separated IDs of the trusted circle to which this threat data should be imported (default is no association). | Optional |
Output
A JSON object containing multiple rows of results:

Search Threat Models
Retrieve threat model from ThreatStream.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Search String | Jinja-templated search string. Example: {{financial_column_name}}, {{services_column_name}}. | Optional |
| Threat Model Type | Select the type of threat model (default is All types). | Optional |
| Result Limit | Result limit (default is 1000). | Optional |
| Result Offset | Result offset (default is 0). | Optional |
Output
A JSON object containing multiple rows of results:
Get Threat Model By Indicator IDs
Get threat model details by indicator ids from ThreatStream.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Indicator IDs | Column name from parent table that contains comma-separated indicator IDs. | Required |
| Threat Model Type | Select the type of threat model. | Required |
| Result Limit | Result limit (Default is 1000). | Optional |
| Result Offset | Result offset (Default is 0). | Optional |
Output
A JSON object containing multiple rows of results:
Get Associations for Threat Model
Get association details for the threat model from ThreatStream.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Threat Model ID | Column name from parent table that contains the ID of the threat model. | Required |
| Threat Model Type | Select the type of threat model. | Required |
| Threat Model Association Type | Select the association type of threat model. | Required |
| Result Limit | Result limit (Default is 1000). | Optional |
| Result Offset | Result offset (Default is 0). | Optional |
Output
A JSON object containing multiple rows of results:
Add Attachment To Threat Model Entity
Add attachment to threat model entities i.e. actors, campaigns, incidents, signatures, TTPs, and vulnerabilities.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Entity Id | Jinja template for Entity id. | Required |
| Model Entity Type | Select a model entity type | Required |
| File Id | Jinja template for file id to be uploaded. e.g. {{file_id}} | Required |
| File Name | Jinja template for file name to be uploaded. e.g. {{file_name}} | Required |
| Time between consecutive API requests (in millis) | Time to wait between consecutive API requests in milliseconds (Default is 0 milliseconds) | Optional |
Output
JSON containing the following items:
{
"has_error": false,
"result": {
"created_ts": "2022-09-22T06:28:57.089",
"tip_report": 435,
"filename": "testData.csv",
"signed_url": "https://ts-optic.s3.amazonaws.com/userUploads/2022-09-22/202_userId-20772_testData.csv?Signature=M3NC33OB",
"modified_ts": "2022-09-22T06:28:57.049",
"user": {
"name": "",
"is_readonly": false,
"is_active": true,
"email": "[email protected]",
"must_change_password": false,
"can_share_intelligence": true,
"organization": {
"resource_uri": "/api/v1/userorganization/24/",
"id": "284",
"name": "Test company"
},
"avatar_s3_url": null,
"nickname": null,
"id": "272",
"resource_uri": "/api/v1/user/272/"
},
"content_type": "",
"signed_thumbnail_url": null,
"s3_thumbnail_url": null,
"s3_url": "http://ts-optic.s3.amazonaws.com/userUploads/2022-09-22/202_06_userId-272_testData.csv",
"id": "1403"
},
"error": null
}
Release Notes
v4.0.14- Added newimport with manual approval v3andimport without manual approval v2actions.Also, deprecatedimport with manual approval v2andimport without manual approvalactionsv4.0.11- AddedExpiration time to neveras an optional parameter inimport with manual approval v2action.v4.0.8- AddedTagsoptional parameter inimport with manual approval v2action.v4.0.0- Updated architecture to support IO via filesystemv3.3.1- Added new action -Add Attachment To Threat Model Entity.v3.2.0- Updated the authentication mechanism in all actions.v3.1.2- Bug Fix - Resolved the 0 value of confidence in import with manual approval v2 action.v3.1.1- Bug Fix - Resolved the default value of confidence in import with manual approval v2 action.v3.1.0- Added new action import with manual approval v2.v3.0.2- Added a few parameters to the import with approval action.
Updated 10 months ago