Azure Sentinel
Version: 2.2.17
Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.
Connect Azure Sentinel with LogicHub
- Navigate to Automations > Integrations.
- Search for Azure Sentinel.
- Click Details, then the + icon. Enter the required information in the following fields.
- Label: Enter a connection name.
- Reference Values: Define variables here to templatize integration connections and actions. For example, you can use https://www.{{hostname}}.com where, hostname is a variable defined in this input. For more information on how to add data, see 'Add Data' Input Type for Integrations.
- Verify SSL: Select option to verify connecting server's SSL certificate (Default is Verify SSL Certificate).
- Remote Agent: Run this integration using the LogicHub Remote Agent.
- Tenant ID: Tenant/directory ID for Azure Sentinel.
- Client ID: Client id for Azure Sentinel.
- Client Secret: Client secret for Azure Sentinel.
- After you've entered all the details, click Connect.
Actions for Azure Sentinel
Execute Query
Executes an analytics query for data.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Workspace Id | Column name from the parent table that contains the ID of the workspace. | Required |
| Query | Column name from the parent table that contains the query to execute. Example: Usage | take 10. | Required |
| Start Date | Column name from the parent table that contains start date. Example: YYYY-MM-DD (default is last 30 Days). | Optional |
| End Date | Column name from the parent table that contains end date. Example: YYYY-MM-DD (default is the last 30 days). | Optional |
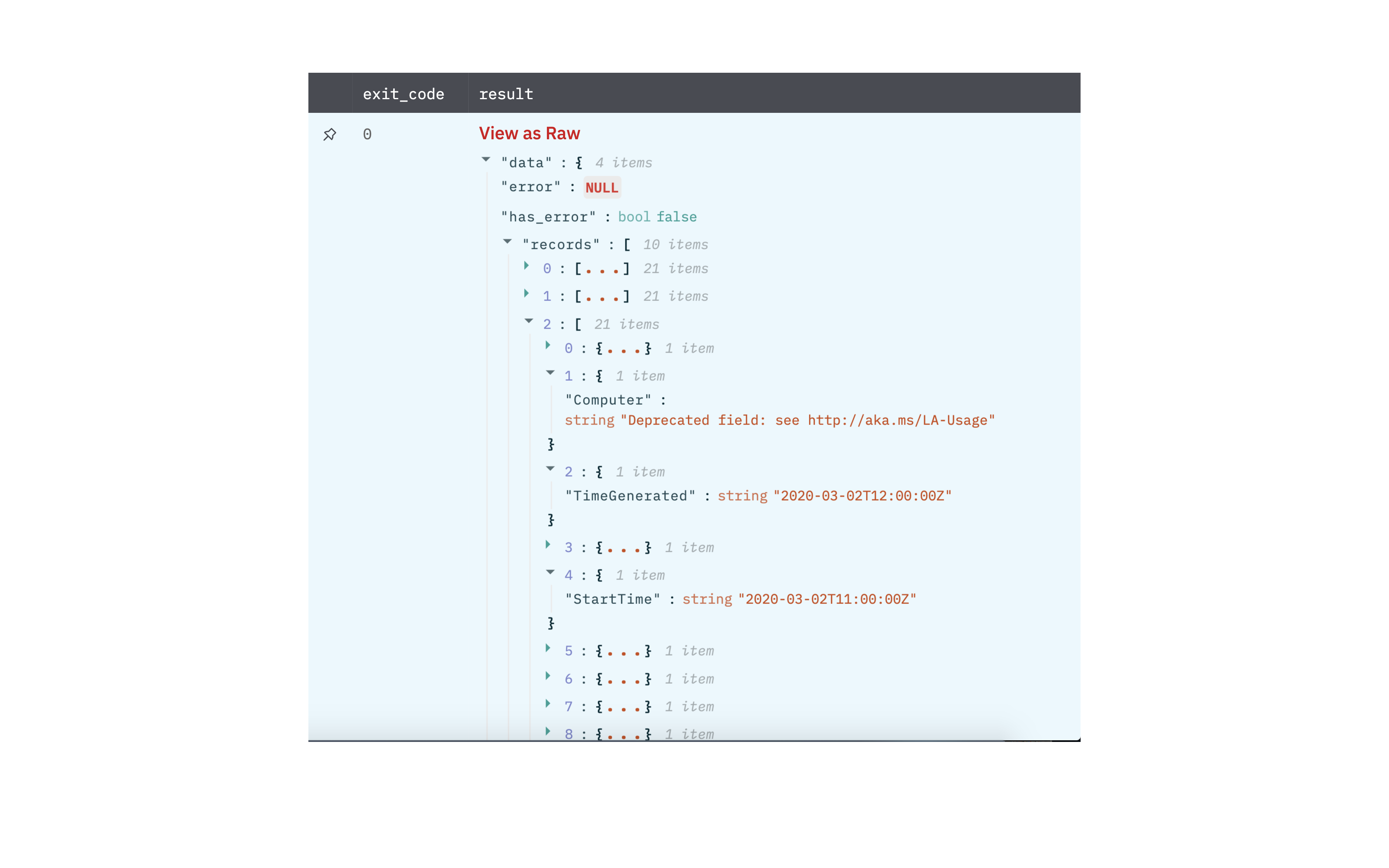
Output
A JSON object containing multiple rows of result:
- has_error: True/False
- error: message/null
- result: Query Result
List Alert Rules
List alert rules.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5basdfsadf/resourceGroups/integon/providers/Microsoft.OperationalInsights/workspaces/teseg/providers/Microsoft.SecurityInsights/alertRules/BuiltInFusion",
"name": "BuiltInFusion",
"etag": "\"25001913-0000-0100-0000-62asdfasdf00\"",
"type": "Microsoft.SecurityInsights/alertRules",
"kind": "MicrosoftSecurityIncidentCreation",
"properties": {
"productFilter": "Microsoft Cloud App Security",
"severitiesFilter": null,
"displayNamesFilter": null,
"displayNamesExcludeFilter": null,
"displayName": "testing displayname",
"enabled": true,
"description": null,
"alertRuleTemplateName": null,
"lastModifiedUtc": "2022-07-07T10:26:30.0222996Z"
}
}
],
"error": null,
"has_error": false
}
Get Alert Rule
Get alert rule by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule ID | Jinja-templated text containing the alert rule ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5asdfasd1d5b/resourceGroups/iation/providers/Microsoft.OperationalInsights/workspaces/tenteg/providers/Microsoft.SecurityInsights/alertRules/BuiltInFusion",
"name": "BuiltInFusion",
"etag": "\"25001913-0000-0100-0000-6asdfsad0000\"",
"type": "Microsoft.SecurityInsights/alertRules",
"kind": "MicrosoftSecurityIncidentCreation",
"properties": {
"productFilter": "Microsoft Cloud App Security",
"severitiesFilter": null,
"displayNamesFilter": null,
"displayNamesExcludeFilter": null,
"displayName": "testing displayname",
"enabled": true,
"description": null,
"alertRuleTemplateName": null,
"lastModifiedUtc": "2022-07-07T10:26:30.0222996Z"
},
"error": null,
"has_error": false
}
Delete Alert Rule
Delete alert rule by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule ID | Jinja-templated text containing the alert rule ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted.",
"error": null,
"has_error": false
}
Create or Update Alert Rule
Create or update alert rule by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule ID | Jinja-templated text containing the alert rule ID for azure sentinel | Required |
| Alert Rule Object | Jinja-templated text containing the alert rule object for azure sentinel. Example '{"kind": "Fusion","properties.alertRuleTemplateName": "f7asdfd-2ffb-45tb-b102-4asdf015c8","properties.enabled": true}' | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5asdfasd1d5b/resourceGroups/iation/providers/Microsoft.OperationalInsights/workspaces/tenteg/providers/Microsoft.SecurityInsights/alertRules/BuiltInFusion",
"name": "BuiltInFusion",
"etag": "\"25001913-0000-0100-0000-6asdfsad0000\"",
"type": "Microsoft.SecurityInsights/alertRules",
"kind": "MicrosoftSecurityIncidentCreation",
"properties": {
"productFilter": "Microsoft Cloud App Security",
"severitiesFilter": null,
"displayNamesFilter": null,
"displayNamesExcludeFilter": null,
"displayName": "testing displayname",
"enabled": true,
"description": null,
"alertRuleTemplateName": null,
"lastModifiedUtc": "2022-07-07T10:26:30.0222996Z"
},
"error": null,
"has_error": false
}
List Actions
List actions by alert rule ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule ID | Jinja-templated text containing the alert rule ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5asdf1d5b/resourceGroups/integn/providers/Microsoft.OperationalInsights/workspaces/teteg/providers/Microsoft.SecurityInsights/alertRules/asicustomalertsv3_builtinfusiontest_ij_newaction_ij/actions/newAction_IJ",
"name": "newAction_IJ",
"etag": "\"a70255cc-0000-0300-0000-62c000\"",
"type": "Microsoft.SecurityInsights/alertRules/actions",
"properties": {
"workflowId": "cd3765391efd4854asd1d48d7",
"logicAppResourceId": "/subscriptions/44a1188f-486a-40f3-b7b6-asdfc911d5b/resourceGroups/inttion/providers/Microsoft.Logic/workflows/MyAlerts"
}
}
],
"error": null,
"has_error": false
}
Get Action
Get action by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule ID | Jinja-templated text containing the alert rule ID for azure sentinel | Required |
| Action ID | Jinja-templated text containing the action ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value":{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5asdf1d5b/resourceGroups/integn/providers/Microsoft.OperationalInsights/workspaces/teteg/providers/Microsoft.SecurityInsights/alertRules/asicustomalertsv3_builtinfusiontest_ij_newaction_ij/actions/newAction_IJ",
"name": "newAction_IJ",
"etag": "\"a70255cc-0000-0300-0000-62c000\"",
"type": "Microsoft.SecurityInsights/alertRules/actions",
"properties": {
"workflowId": "cd3765391efd4854asd1d48d7",
"logicAppResourceId": "/subscriptions/44a1188f-486a-40f3-b7b6-asdfc911d5b/resourceGroups/inttion/providers/Microsoft.Logic/workflows/MyAlerts"
}
},
"error": null,
"has_error": false
}
Delete Action
Delete action by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule ID | Jinja-templated text containing the alert rule ID for azure sentinel | Required |
| Action ID | Jinja-templated text containing the action ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted.",
"error": null,
"has_error": false
}
Create or Update Action
Create or update action.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule ID | Jinja-templated text containing the alert rule ID for azure sentinel | Required |
| Action ID | Jinja-templated text containing the action ID for azure sentinel | Required |
| Action Object | Jinja-templated text containing the action object for azure sentinel. Example '{"kind": "Fusion","properties.alertRuleTemplateName": "f7asdfd-2ffb-45tb-b102-4asdf015c8","properties.enabled": true}' | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value":{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5asdf1d5b/resourceGroups/integn/providers/Microsoft.OperationalInsights/workspaces/teteg/providers/Microsoft.SecurityInsights/alertRules/asicustomalertsv3_builtinfusiontest_ij_newaction_ij/actions/newAction_IJ",
"name": "newAction_IJ",
"etag": "\"a70255cc-0000-0300-0000-62c000\"",
"type": "Microsoft.SecurityInsights/alertRules/actions",
"properties": {
"workflowId": "cd3765391efd4854asd1d48d7",
"logicAppResourceId": "/subscriptions/44a1188f-486a-40f3-b7b6-asdfc911d5b/resourceGroups/inttion/providers/Microsoft.Logic/workflows/MyAlerts"
}
},
"error": null,
"has_error": false
}
List Alert Rule Templates
List alert rule templates.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5basdfasdfd5b/resourceGroups/intion/providers/Microsoft.OperationalInsights/workspaces/testeg/providers/Microsoft.SecurityInsights/alertRules/BuiltInFusion",
"name": "BuiltInFusion",
"etag": "\"240035cc-0000-0100-0000-6asdfs950000\"",
"type": "Microsoft.SecurityInsights/alertRules",
"kind": "Fusion",
"properties": {
"displayName": "Advanced Multistage Attack Detection",
"description": "Microsoft Sentinel uses Fusion, a correlation engine based on scalable machine learning algorithms, to automatically detect multistage attacks by identifying combinations of anomalous behaviors and suspicious activities that are observed at various stages of the kill chain. On the basis of these discoveries, Azure Sentinel generates incidents that would otherwise be very difficult to catch. By design, these incidents are low-volume, high-fidelity, and high-severity, which is why this detection is turned ON by default.\n\nSince Fusion correlates multiple signals from various products to detect advanced multistage attacks, successful Fusion detections are presented as Fusion incidents on the Microsoft Sentinel Incidents page. This rule covers the following detections:\n- Fusion for emerging threats\n- Fusion for ransomware\n- Scenario-based Fusion detections (122 scenarios)\n\nTo enable these detections, we recommend you configure the following data connectors for best results:\n- Out-of-the-box anomaly detections\n- Azure Active Directory Identity Protection\n- Azure Defender\n- Azure Defender for IoT\n- Microsoft 365 Defender\n- Microsoft Cloud App Security \n- Microsoft Defender for Endpoint\n- Microsoft Defender for Identity\n- Microsoft Defender for Office 365\n- Scheduled analytics rules, both built-in and those created by your security analysts. Analytics rules must contain kill-chain (tactics) and entity mapping information in order to be used by Fusion.\n\nFor the full description of each detection that is supported by Fusion, go to https://aka.ms/SentinelFusion.",
"alertRuleTemplateName": "f71aba3d-28fb-450b-b192-4easdf015c8",
"tactics": [
"Collection",
"CommandAndControl",
"PrivilegeEscalation"
],
"severity": "High",
"enabled": true,
"lastModifiedUtc": "2022-07-07T04:35:33.2698249Z"
}
},
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5bfasdfasd5b/resourceGroups/intion/providers/Microsoft.OperationalInsights/workspaces/teseg/providers/Microsoft.SecurityInsights/alertRules/BuiltInFusion",
"name": "BuiltInFusionTest_IJ",
"etag": "\"25001913-0000-0100-0000-62asdf0000\"",
"type": "Microsoft.SecurityInsights/alertRules",
"kind": "MicrosoftSecurityIncidentCreation",
"properties": {
"productFilter": "Microsoft Cloud App Security",
"severitiesFilter": null,
"displayNamesFilter": null,
"displayNamesExcludeFilter": null,
"displayName": "testing displayname",
"enabled": true,
"description": null,
"alertRuleTemplateName": null,
"lastModifiedUtc": "2022-07-07T10:26:30.0222996Z"
}
}
],
"error": null,
"has_error": false
}
Get Alert Rule Template
Get alert rule template.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Alert Rule Template ID | Jinja-templated text containing the alert rule template ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": {
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5basdfasdfd5b/resourceGroups/intion/providers/Microsoft.OperationalInsights/workspaces/testeg/providers/Microsoft.SecurityInsights/alertRules/BuiltInFusion",
"name": "BuiltInFusion",
"etag": "\"240035cc-0000-0100-0000-6asdfs950000\"",
"type": "Microsoft.SecurityInsights/alertRules",
"kind": "Fusion",
"properties": {
"displayName": "Advanced Multistage Attack Detection",
"description": "Microsoft Sentinel uses Fusion, a correlation engine based on scalable machine learning algorithms, to automatically detect multistage attacks by identifying combinations of anomalous behaviors and suspicious activities that are observed at various stages of the kill chain. On the basis of these discoveries, Azure Sentinel generates incidents that would otherwise be very difficult to catch. By design, these incidents are low-volume, high-fidelity, and high-severity, which is why this detection is turned ON by default.\n\nSince Fusion correlates multiple signals from various products to detect advanced multistage attacks, successful Fusion detections are presented as Fusion incidents on the Microsoft Sentinel Incidents page. This rule covers the following detections:\n- Fusion for emerging threats\n- Fusion for ransomware\n- Scenario-based Fusion detections (122 scenarios)\n\nTo enable these detections, we recommend you configure the following data connectors for best results:\n- Out-of-the-box anomaly detections\n- Azure Active Directory Identity Protection\n- Azure Defender\n- Azure Defender for IoT\n- Microsoft 365 Defender\n- Microsoft Cloud App Security \n- Microsoft Defender for Endpoint\n- Microsoft Defender for Identity\n- Microsoft Defender for Office 365\n- Scheduled analytics rules, both built-in and those created by your security analysts. Analytics rules must contain kill-chain (tactics) and entity mapping information in order to be used by Fusion.\n\nFor the full description of each detection that is supported by Fusion, go to https://aka.ms/SentinelFusion.",
"alertRuleTemplateName": "f71aba3d-28fb-450b-b192-4easdf015c8",
"tactics": [
"Collection",
"CommandAndControl",
"PrivilegeEscalation"
],
"severity": "High",
"enabled": true,
"lastModifiedUtc": "2022-07-07T04:35:33.2698249Z"
}
}
"error": null,
"has_error": false
}
List Automation Rules
List automation rules.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6asdfc911d5b/resourceGroups/inrion/providers/Microsoft.OperationalInsights/workspaces/teteg/providers/Microsoft.SecurityInsights/AutomationRules/newone",
"name": "newone",
"etag": "\"1f00cd3b-0000-0100-0000-62casdf000\"",
"type": "Microsoft.SecurityInsights/AutomationRules",
"properties": {
"displayName": "hello",
"order": 1,
"triggeringLogic": {
"isEnabled": true,
"triggersOn": "Incidents",
"triggersWhen": "Created",
"conditions": []
},
"actions": [
{
"order": 1,
"actionType": "ModifyProperties",
"actionConfiguration": {
"severity": "High",
"status": null,
"classification": null,
"classificationReason": null,
"classificationComment": null,
"owner": null,
"labels": null
}
}
],
"lastModifiedTimeUtc": "2022-07-07T06:59:20Z",
"createdTimeUtc": "2022-07-07T06:59:20Z",
"lastModifiedBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8asdfe2c68ff",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
},
"createdBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8b8d5asdf",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
}
}
},
{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5basdfd5b/resourceGroups/intion/providers/Microsoft.OperationalInsights/workspaces/teseg/providers/Microsoft.SecurityInsights/AutomationRules/testij",
"name": "testij",
"etag": "\"1f005462-0000-0100-0000-62c7asdf00\"",
"type": "Microsoft.SecurityInsights/AutomationRules",
"properties": {
"displayName": "hello IJ",
"order": 1,
"triggeringLogic": {
"isEnabled": true,
"triggersOn": "Incidents",
"triggersWhen": "Created",
"conditions": []
},
"actions": [
{
"order": 1,
"actionType": "ModifyProperties",
"actionConfiguration": {
"severity": "High",
"status": null,
"classification": null,
"classificationReason": null,
"classificationComment": null,
"owner": null,
"labels": null
}
}
],
"lastModifiedTimeUtc": "2022-07-08T04:34:20Z",
"createdTimeUtc": "2022-07-08T04:34:20Z",
"lastModifiedBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8basdf68ff",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
},
"createdBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8basdfc68ff",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
}
}
}
],
"error": null,
"has_error": false
}
Get Automation Rule
Get automation rule by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Automation Rule ID | Jinja-templated text containing the automation rule ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value":{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5basdfd5b/resourceGroups/intion/providers/Microsoft.OperationalInsights/workspaces/teseg/providers/Microsoft.SecurityInsights/AutomationRules/testij",
"name": "testij",
"etag": "\"1f005462-0000-0100-0000-62c7asdf00\"",
"type": "Microsoft.SecurityInsights/AutomationRules",
"properties": {
"displayName": "hello IJ",
"order": 1,
"triggeringLogic": {
"isEnabled": true,
"triggersOn": "Incidents",
"triggersWhen": "Created",
"conditions": []
},
"actions": [
{
"order": 1,
"actionType": "ModifyProperties",
"actionConfiguration": {
"severity": "High",
"status": null,
"classification": null,
"classificationReason": null,
"classificationComment": null,
"owner": null,
"labels": null
}
}
],
"lastModifiedTimeUtc": "2022-07-08T04:34:20Z",
"createdTimeUtc": "2022-07-08T04:34:20Z",
"lastModifiedBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8basdf68ff",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
},
"createdBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8basdfc68ff",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
}
}
},
"error": null,
"has_error": false
}
Delete Automation Rule
Delete automation rule by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Automation Rule ID | Jinja-templated text containing the automation rule ID for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted.",
"error": null,
"has_error": false
}
Create or Update Automation Rule
Create or update automation rule.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Automation Rule ID | Jinja-templated text containing the automation rule ID for azure sentinel | Required |
| Automation Rule Object | Jinja-templated text containing the automation object for azure sentinel. Example '{"kind": "Fusion","properties.alertRuleTemplateName": "f7asdfd-2ffb-45tb-b102-4asdf015c8","properties.enabled": true}' | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value":{
"id": "/subscriptions/44a1188f-486a-40f3-b7b6-5basdfd5b/resourceGroups/intion/providers/Microsoft.OperationalInsights/workspaces/teseg/providers/Microsoft.SecurityInsights/AutomationRules/testij",
"name": "testij",
"etag": "\"1f005462-0000-0100-0000-62c7asdf00\"",
"type": "Microsoft.SecurityInsights/AutomationRules",
"properties": {
"displayName": "hello IJ",
"order": 1,
"triggeringLogic": {
"isEnabled": true,
"triggersOn": "Incidents",
"triggersWhen": "Created",
"conditions": []
},
"actions": [
{
"order": 1,
"actionType": "ModifyProperties",
"actionConfiguration": {
"severity": "High",
"status": null,
"classification": null,
"classificationReason": null,
"classificationComment": null,
"owner": null,
"labels": null
}
}
],
"lastModifiedTimeUtc": "2022-07-08T04:34:20Z",
"createdTimeUtc": "2022-07-08T04:34:20Z",
"lastModifiedBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8basdf68ff",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
},
"createdBy": {
"objectId": "8792fc6e-1ddd-407f-b522-8basdfc68ff",
"email": null,
"name": "External application - Sentinel",
"userPrincipalName": null
}
}
},
"error": null,
"has_error": false
}
List Bookmarks
List bookmarks.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/afbd324f-6c48-459c-8710-8d1e1cd03812",
"name": "afbd324f-6c48-459c-8710-8d1e1cd03812",
"type": "Microsoft.SecurityInsights/Entities",
"kind": "Bookmark",
"properties": {
"displayName": "SecurityEvent - 868f40f4698d",
"created": "2020-06-17T15:34:01.4265524+00:00",
"updated": "2020-06-17T15:34:01.4265524+00:00",
"createdBy": {
"objectId": "b03ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"updatedBy": {
"objectId": "b03ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"eventTime": "2020-06-17T15:34:01.4265524+00:00",
"labels": [],
"query": "SecurityEvent\r\n| take 1\n",
"queryResult": "{\"TimeGenerated\":\"2020-05-24T01:24:25.67Z\",\"Account\":\"\\\\ADMINISTRATOR\",\"AccountType\":\"User\",\"Computer\":\"SecurityEvents\",\"EventSourceName\":\"Microsoft-Windows-Security-Auditing\",\"Channel\":\"Security\",\"Task\":12544,\"Level\":\"16\",\"EventID\":4625,\"Activity\":\"4625 - An account failed to log on.\",\"AuthenticationPackageName\":\"NTLM\",\"FailureReason\":\"%%2313\",\"IpAddress\":\"176.113.115.73\",\"IpPort\":\"0\",\"LmPackageName\":\"-\",\"LogonProcessName\":\"NtLmSsp \",\"LogonType\":3,\"LogonTypeName\":\"3 - Network\",\"Process\":\"-\",\"ProcessId\":\"0x0\",\"__entityMapping\":{\"\\\\ADMINISTRATOR\":\"Account\",\"SecurityEvents\":\"Host\"}}",
"additionalData": {
"ETag": "\"3b00acab-0000-0d00-0000-5f15e4ed0000\"",
"EntityId": "afbd324f-6c48-459c-8710-8d1e1cd03812"
},
"friendlyName": "SecurityEvent - 868f40f4698d"
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/bbbd324f-6c48-459c-8710-8d1e1cd03812",
"name": "bbbd324f-6c48-459c-8710-8d1e1cd03812",
"type": "Microsoft.SecurityInsights/Entities",
"kind": "Bookmark",
"properties": {
"displayName": "SecurityEvent - 868f40f4698d",
"created": "2020-06-17T15:34:01.4265524+00:00",
"updated": "2020-06-17T15:34:01.4265524+00:00",
"createdBy": {
"objectId": "303ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"updatedBy": {
"objectId": "b03ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"eventTime": "2020-06-17T15:34:01.4265524+00:00",
"labels": [],
"query": "SecurityEvent\r\n| take 1\n",
"queryResult": "{\"TimeGenerated\":\"2020-05-24T01:24:25.67Z\",\"Account\":\"\\\\ADMINISTRATOR\",\"AccountType\":\"User\",\"Computer\":\"SecurityEvents\",\"EventSourceName\":\"Microsoft-Windows-Security-Auditing\",\"Channel\":\"Security\",\"Task\":12544,\"Level\":\"16\",\"EventID\":4625,\"Activity\":\"4625 - An account failed to log on.\",\"AuthenticationPackageName\":\"NTLM\",\"FailureReason\":\"%%2313\",\"IpAddress\":\"176.113.115.73\",\"IpPort\":\"0\",\"LmPackageName\":\"-\",\"LogonProcessName\":\"NtLmSsp \",\"LogonType\":3,\"LogonTypeName\":\"3 - Network\",\"Process\":\"-\",\"ProcessId\":\"0x0\",\"__entityMapping\":{\"\\\\ADMINISTRATOR\":\"Account\",\"SecurityEvents\":\"Host\"}}",
"additionalData": {
"ETag": "\"3b00acab-0000-0d00-0000-5f15e4ed0000\"",
"EntityId": "afbd324f-6c48-459c-8710-8d1e1cd03812"
},
"friendlyName": "SecurityEvent - 868f40f4698d"
}
}
],
"has_error": false,
"error": null
}
Get Bookmark
Get Bookmark by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Bookmark ID | Jinja-template text containing the bookmark ID for azure sentinel | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": {
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"name": "73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"type": "Microsoft.SecurityInsights/bookmarks",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"displayName": "My bookmark",
"createdBy": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"name": "john doe"
},
"updatedBy": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"name": "john doe"
},
"updated": "2021-09-01T13:15:30Z",
"created": "2021-09-01T13:15:30Z",
"notes": "Found a suspicious activity",
"labels": [
"Tag1",
"Tag2"
],
"query": "SecurityEvent | where TimeGenerated > ago(1d) and TimeGenerated < ago(2d)",
"queryResult": "Security Event query result",
"incidentInfo": {
"incidentId": "DDA55F97-170B-40B9-B8ED-CBFD05481E7D",
"severity": "Low",
"title": "New case 1",
"relationName": "4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0018"
},
"tactics": [
"Execution"
],
"techniques": [
"T1609"
],
"entityMappings": [
{
"entityType": "Account",
"fieldMappings": [
{
"identifier": "Fullname",
"value": "[email protected]"
}
]
}
]
}
},
"has_error": false,
"error": null
}
Delete Bookmark
Delete bookmark by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Bookmark ID | Jinja-template text containing the bookmark ID for azure sentinel | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted."
"has_error": false,
"error": null
}
Create or Update Bookmark
Create or update bookmark.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Bookmark ID | Jinja-template text containing the bookmark ID for azure sentinel | Required |
| Bookmark Object | Jinja-template text containing the bookmark object for azure sentinel. Example '{"kind": "Fusion","properties.alertRuleTemplateName": "f7asdfd-2ffb-45tb-b102-4asdf015c8","properties.enabled": true}' | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value":{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"name": "73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"type": "Microsoft.SecurityInsights/bookmarks",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"displayName": "My bookmark",
"createdBy": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"name": "john doe"
},
"updatedBy": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"name": "john doe"
},
"updated": "2021-09-01T13:15:30Z",
"created": "2021-09-01T13:15:30Z",
"notes": "Found a suspicious activity",
"labels": [
"Tag1",
"Tag2"
],
"query": "SecurityEvent | where TimeGenerated > ago(1d) and TimeGenerated < ago(2d)",
"queryResult": "Security Event query result",
"tactics": [
"Execution"
],
"techniques": [
"T1609"
],
"entityMappings": [
{
"entityType": "Account",
"fieldMappings": [
{
"identifier": "Fullname",
"value": "[email protected]"
}
]
}
]
}
},
"has_error": false,
"error": null
}
List Data Connectors
List data connectors.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/763f9fa1-c2d3-4fa2-93e9-bccd4899aa12",
"name": "763f9fa1-c2d3-4fa2-93e9-bccd4899aa12",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "AzureSecurityCenter",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"subscriptionId": "d0cfe6b2-9ac0-4464-9919-dccaee2e48c0",
"dataTypes": {
"alerts": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/c345bf40-8509-4ed2-b947-50cb773aaf04",
"name": "c345bf40-8509-4ed2-b947-50cb773aaf04",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "ThreatIntelligence",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"indicators": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/c39bb458-02a7-4b3f-b0c8-71a1d2692652",
"name": "c39bb458-02a7-4b3f-b0c8-71a1d2692652",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "ThreatIntelligenceTaxii",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"workspaceId": "8b014a77-4695-4ef4-96bb-6623afb121a2",
"friendlyName": "My TI Taxii Connector",
"taxiiServer": "https://mytaxiiserver.com/taxiing/v2/api",
"collectionId": "e0b1f32d-1188-48f7-a7a3-de71924e4b5e",
"userName": "",
"password": "",
"pollingFrequency": "OnceAMinute",
"dataTypes": {
"taxiiClient": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/f0cd27d2-5f03-4c06-ba31-d2dc82dcb51d",
"name": "f0cd27d2-5f03-4c06-ba31-d2dc82dcb51d",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "AzureActiveDirectory",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"alerts": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"name": "73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "Office365",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"sharePoint": {
"state": "Enabled"
},
"exchange": {
"state": "Enabled"
},
"teams": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/b96d014d-b5c2-4a01-9aba-a8058f629d42",
"name": "b96d014d-b5c2-4a01-9aba-a8058f629d42",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "MicrosoftCloudAppSecurity",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"alerts": {
"state": "Enabled"
},
"discoveryLogs": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/07e42cb3-e658-4e90-801c-efa0f29d3d44",
"name": "07e42cb3-e658-4e90-801c-efa0f29d3d44",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "AzureAdvancedThreatProtection",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"alerts": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/c345bf40-8509-4ed2-b947-50cb773aaf04",
"name": "c345bf40-8509-4ed2-b947-50cb773aaf04",
"type": "Microsoft.SecurityInsights/dataConnectors",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"kind": "AmazonWebServicesCloudTrail",
"properties": {
"awsRoleArn": "myAwsRoleArn",
"dataTypes": {
"logs": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/afef3743-0c88-469c-84ff-ca2e87dc1e48",
"name": "afef3743-0c88-469c-84ff-ca2e87dc1e48",
"type": "Microsoft.SecurityInsights/dataConnectors",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"kind": "AmazonWebServicesS3",
"properties": {
"destinationTable": "AWSVPCFlow",
"roleArn": "arn:aws:iam::072643944673:role/RoleName",
"sqsUrls": [
"https://sqs.us-west-1.amazonaws.com/111111111111/sqsTestName"
],
"dataTypes": {
"logs": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/06b3ccb8-1384-4bcc-aec7-852f6d57161b",
"name": "06b3ccb8-1384-4bcc-aec7-852f6d57161b",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "MicrosoftDefenderAdvancedThreatProtection",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"alerts": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/3d3e955e-33eb-401d-89a7-251c81ddd660",
"name": "3d3e955e-33eb-401d-89a7-251c81ddd660",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "OfficeATP",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"alerts": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/3d3e955e-33eb-401d-89a7-251c81ddd660",
"name": "3d3e955e-33eb-401d-89a7-251c81ddd660",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "Office365Project",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"logs": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/3d3e955e-33eb-401d-89a7-251c81ddd660",
"name": "3d3e955e-33eb-401d-89a7-251c81ddd660",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "OfficePowerBI",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"logs": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/3d3e955e-33eb-401d-89a7-251c81ddd660",
"name": "c2541efb-c9a6-47fe-9501-87d1017d1512",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "Dynamics365",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"tenantId": "2070ecc9-b4d5-4ae4-adaa-936fa1954fa8",
"dataTypes": {
"dynamics365CdsActivities": {
"state": "Enabled"
}
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"name": "316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"etag": "\"1a00b074-0000-0100-0000-606ef5bd0000\"",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "GenericUI",
"properties": {
"connectorUiConfig": {
"title": "Qualys Vulnerability Management (CCP DEMO)",
"publisher": "Qualys",
"descriptionMarkdown": "The [Qualys Vulnerability Management (VM)](https://www.qualys.com/apps/vulnerability-management/) data connector provides the capability to ingest vulnerability host detection data into Azure Sentinel through the Qualys API. The connector provides visibility into host detection data from vulerability scans. This connector provides Azure Sentinel the capability to view dashboards, create custom alerts, and improve investigation ",
"customImage": "The image connector content",
"graphQueriesTableName": "QualysHostDetection_CL",
"graphQueries": [
{
"metricName": "Total data received",
"legend": "{{graphQueriesTableName}}",
"baseQuery": "{{graphQueriesTableName}}"
}
],
"sampleQueries": [
{
"description": "Top 10 Vulerabilities detected",
"query": "{{graphQueriesTableName}}\n | mv-expand todynamic(Detections_s)\n | extend Vulnerability = tostring(Detections_s.Results)\n | summarize count() by Vulnerability\n | top 10 by count_"
}
],
"dataTypes": [
{
"name": "{{graphQueriesTableName}}",
"lastDataReceivedQuery": "{{graphQueriesTableName}}\n | summarize Time = max(TimeGenerated)\n | where isnotempty(Time)"
}
],
"connectivityCriteria": [
{
"type": "IsConnectedQuery",
"value": [
"{{graphQueriesTableName}}\n | summarize LastLogReceived = max(TimeGenerated)\n | project IsConnected = LastLogReceived > ago(30d)"
]
}
],
"availability": {
"status": 1,
"isPreview": true
},
"permissions": {
"resourceProvider": [
{
"provider": "Microsoft.OperationalInsights/workspaces",
"permissionsDisplayText": "read and write permissions on the workspace are required.",
"providerDisplayName": "Workspace",
"scope": "Workspace",
"requiredPermissions": {
"write": true,
"read": true,
"delete": true
}
},
{
"provider": "Microsoft.OperationalInsights/workspaces/sharedKeys",
"permissionsDisplayText": "read permissions to shared keys for the workspace are required. [See the documentation to learn more about workspace keys](https://docs.microsoft.com/azure/azure-monitor/platform/agent-windows#obtain-workspace-id-and-key).",
"providerDisplayName": "Keys",
"scope": "Workspace",
"requiredPermissions": {
"action": true
}
}
],
"customs": [
{
"name": "Microsoft.Web/sites permissions",
"description": "Read and write permissions to Azure Functions to create a Function App is required. [See the documentation to learn more about Azure Functions](https://docs.microsoft.com/azure/azure-functions/)."
},
{
"name": "Qualys API Key",
"description": "A Qualys VM API username and password is required. [See the documentation to learn more about Qualys VM API](https://www.qualys.com/docs/qualys-api-vmpc-user-guide.pdf)."
}
]
},
"instructionSteps": [
{
"title": "",
"description": ">**NOTE:** This connector uses Azure Functions to connect to Qualys VM to pull its logs into Azure Sentinel. This might result in additional data ingestion costs. Check the [Azure Functions pricing page](https://azure.microsoft.com/pricing/details/functions/) for details."
},
{
"title": "",
"description": ">**(Optional Step)** Securely store workspace and API authorization key(s) or token(s) in Azure Key Vault. Azure Key Vault provides a secure mechanism to store and retrieve key values. [Follow these instructions](https://docs.microsoft.com/azure/app-service/app-service-key-vault-references) to use Azure Key Vault with an Azure Function App."
},
{
"title": "",
"description": "**STEP 1 - Configuration steps for the Qualys VM API**\n\n1. Log into the Qualys Vulnerability Management console with an administrator account, select the **Users** tab and the **Users** subtab. \n2. Click on the **New** drop-down menu and select **Users..**\n3. Create a username and password for the API account. \n4. In the **User Roles** tab, ensure the account role is set to **Manager** and access is allowed to **GUI** and **API**\n4. Log out of the administrator account and log into the console with the new API credentials for validation, then log out of the API account. \n5. Log back into the console using an administrator account and modify the API accounts User Roles, removing access to **GUI**. \n6. Save all changes."
},
{
"title": "",
"description": "**STEP 2 - Choose ONE from the following two deployment options to deploy the connector and the associated Azure Function**\n\n>**IMPORTANT:** Before deploying the Qualys VM connector, have the Workspace ID and Workspace Primary Key (can be copied from the following), as well as the Qualys VM API Authorization Key(s), readily available.",
"instructions": [
{
"parameters": {
"fillWith": [
"WorkspaceId"
],
"label": "Workspace ID"
},
"type": "CopyableLabel"
},
{
"parameters": {
"fillWith": [
"PrimaryKey"
],
"label": "Primary Key"
},
"type": "CopyableLabel"
}
]
},
{
"title": "Option 1 - Azure Resource Manager (ARM) Template",
"description": "Use this method for automated deployment of the Qualys VM connector using an ARM Tempate.\n\n1. Click the **Deploy to Azure** button below. \n\n\t[](https://aka.ms/sentinelqualysvmazuredeploy)\n2. Select the preferred **Subscription**, **Resource Group** and **Location**. \n3. Enter the **Workspace ID**, **Workspace Key**, **API Username**, **API Password** , update the **URI**, and any additional URI **Filter Parameters** (each filter should be separated by an \"&\" symbol, no spaces.) \n> - Enter the URI that corresponds to your region. The complete list of API Server URLs can be [found here](https://www.qualys.com/docs/qualys-api-vmpc-user-guide.pdf#G4.735348) -- There is no need to add a time suffix to the URI, the Function App will dynamically append the Time Value to the URI in the proper format. \n - The default **Time Interval** is set to pull the last five (5) minutes of data. If the time interval needs to be modified, it is recommended to change the Function App Timer Trigger accordingly (in the function.json file, post deployment) to prevent overlapping data ingestion. \n> - Note: If using Azure Key Vault secrets for any of the values above, use the`@Microsoft.KeyVault(SecretUri={Security Identifier})`schema in place of the string values. Refer to [Key Vault references documentation](https://docs.microsoft.com/azure/app-service/app-service-key-vault-references) for further details. \n4. Mark the checkbox labeled **I agree to the terms and conditions stated above**. \n5. Click **Purchase** to deploy."
},
{
"title": "Option 2 - Manual Deployment of Azure Functions",
"description": "Use the following step-by-step instructions to deploy the Quayls VM connector manually with Azure Functions."
},
{
"title": "",
"description": "**1. Create a Function App**\n\n1. From the Azure Portal, navigate to [Function App](https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.Web%2Fsites/kind/functionapp), and select **+ Add**.\n2. In the **Basics** tab, ensure Runtime stack is set to **Powershell Core**. \n3. In the **Hosting** tab, ensure the **Consumption (Serverless)** plan type is selected.\n4. Make other preferrable configuration changes, if needed, then click **Create**."
},
{
"title": "",
"description": "**2. Import Function App Code**\n\n1. In the newly created Function App, select **Functions** on the left pane and click **+ New Function**.\n2. Select **Timer Trigger**.\n3. Enter a unique Function **Name** and leave the default cron schedule of every 5 minutes, then click **Create**.\n5. Click on **Code + Test** on the left pane. \n6. Copy the [Function App Code](https://aka.ms/sentinelqualysvmazurefunctioncode) and paste into the Function App `run.ps1` editor.\n7. Click **Save**."
},
{
"title": "",
"description": "**3. Configure the Function App**\n\n1. In the Function App, select the Function App Name and select **Configuration**.\n2. In the **Application settings** tab, select **+ New application setting**.\n3. Add each of the following seven (7) application settings individually, with their respective string values (case-sensitive): \n\t\tapiUsername\n\t\tapiPassword\n\t\tworkspaceID\n\t\tworkspaceKey\n\t\turi\n\t\tfilterParameters\n\t\ttimeInterval\n> - Enter the URI that corresponds to your region. The complete list of API Server URLs can be [found here](https://www.qualys.com/docs/qualys-api-vmpc-user-guide.pdf#G4.735348). The `uri` value must follow the following schema: `https://<API Server>/api/2.0/fo/asset/host/vm/detection/?action=list&vm_processed_after=` -- There is no need to add a time suffix to the URI, the Function App will dynamically append the Time Value to the URI in the proper format.\n> - Add any additional filter parameters, for the `filterParameters` variable, that need to be appended to the URI. Each parameter should be seperated by an \"&\" symbol and should not include any spaces.\n> - Set the `timeInterval` (in minutes) to the value of `5` to correspond to the Timer Trigger of every `5` minutes. If the time interval needs to be modified, it is recommended to change the Function App Timer Trigger accordingly to prevent overlapping data ingestion.\n> - Note: If using Azure Key Vault, use the`@Microsoft.KeyVault(SecretUri={Security Identifier})`schema in place of the string values. Refer to [Key Vault references documentation](https://docs.microsoft.com/azure/app-service/app-service-key-vault-references) for further details.\n4. Once all application settings have been entered, click **Save**."
},
{
"title": "",
"description": "**4. Configure the host.json**.\n\nDue to the potentially large amount of Qualys host detection data being ingested, it can cause the execution time to surpass the default Function App timeout of five (5) minutes. Increase the default timeout duration to the maximum of ten (10) minutes, under the Consumption Plan, to allow more time for the Function App to execute.\n\n1. In the Function App, select the Function App Name and select the **App Service Editor** blade.\n2. Click **Go** to open the editor, then select the **host.json** file under the **wwwroot** directory.\n3. Add the line `\"functionTimeout\": \"00:10:00\",` above the `managedDependancy` line \n4. Ensure **SAVED** appears on the top right corner of the editor, then exit the editor.\n\n> NOTE: If a longer timeout duration is required, consider upgrading to an [App Service Plan](https://docs.microsoft.com/azure/azure-functions/functions-scale#timeout)"
}
]
}
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"name": "316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"etag": "\"1a00b074-0000-0100-0000-606ef5bd0000\"",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "APIPolling",
"properties": {
"connectorUiConfig": {
"title": "GitHub Enterprise Audit Log",
"publisher": "GitHub",
"descriptionMarkdown": "The GitHub audit log connector provides the capability to ingest GitHub logs into Azure Sentinel. By connecting GitHub audit logs into Azure Sentinel, you can view this data in workbooks, use it to create custom alerts, and improve your investigation process.",
"graphQueriesTableName": "GitHubAuditLogPolling_CL",
"graphQueries": [
{
"metricName": "Total events received",
"legend": "GitHub audit log events",
"baseQuery": "{{graphQueriesTableName}}"
}
],
"sampleQueries": [
{
"description": "All logs",
"query": "{{graphQueriesTableName}}\n | take 10 <change>"
}
],
"dataTypes": [
{
"name": "{{graphQueriesTableName}}",
"lastDataReceivedQuery": "{{graphQueriesTableName}}\n | summarize Time = max(TimeGenerated)\n | where isnotempty(Time)"
}
],
"connectivityCriteria": [
{
"type": "SentinelKindsV2",
"value": []
}
],
"availability": {
"status": 1,
"isPreview": true
},
"permissions": {
"resourceProvider": [
{
"provider": "Microsoft.OperationalInsights/workspaces",
"permissionsDisplayText": "read and write permissions are required.",
"providerDisplayName": "Workspace",
"scope": "Workspace",
"requiredPermissions": {
"write": true,
"read": true,
"delete": true
}
}
],
"customs": [
{
"name": "GitHub API personal token Key",
"description": "You need access to GitHub personal token, the key should have 'admin:org' scope"
}
]
},
"instructionSteps": [
{
"title": "Connect GitHub Enterprise Audit Log to Azure Sentinel",
"description": "Enable GitHub audit Logs. \n Follow [this](https://docs.github.com/en/github/authenticating-to-github/keeping-your-account-and-data-secure/creating-a-personal-access-token) to create or find your personal key",
"instructions": [
{
"parameters": {
"enable": "true",
"userRequestPlaceHoldersInput": [
{
"displayText": "Organization Name",
"requestObjectKey": "apiEndpoint",
"placeHolderName": "{{placeHolder1}}",
"placeHolderValue": ""
}
]
},
"type": "APIKey"
}
]
}
]
},
"pollingConfig": {
"auth": {
"authType": "APIKey",
"apiKeyIdentifier": "token",
"apiKeyName": "Authorization"
},
"request": {
"apiEndpoint": "https://api.github.com/organizations/{{placeHolder1}}/audit-log",
"rateLimitQps": 50,
"queryWindowInMin": 15,
"httpMethod": "Get",
"queryTimeFormat": "yyyy-MM-ddTHH:mm:ssZ",
"retryCount": 2,
"timeoutInSeconds": 60,
"headers": {
"Accept": "application/json",
"User-Agent": "Scuba"
},
"queryParameters": {
"phrase": "created:{_QueryWindowStartTime}..{_QueryWindowEndTime}"
}
},
"paging": {
"pagingType": "LinkHeader",
"pageSizeParaName": "per_page"
},
"response": {
"eventsJsonPaths": [
"$"
]
}
}
}
}
],
"has_error": false,
"error": null
}
Get Data Connector
Get Data Connector by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Data Connector ID | Jinja-template text containing the data connector ID for azure sentinel | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": {
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"name": "316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"etag": "\"1a00b074-0000-0100-0000-606ef5bd0000\"",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "APIPolling",
"properties": {
"connectorUiConfig": {
"title": "GitHub Enterprise Audit Log",
"publisher": "GitHub",
"descriptionMarkdown": "The GitHub audit log connector provides the capability to ingest GitHub logs into Azure Sentinel. By connecting GitHub audit logs into Azure Sentinel, you can view this data in workbooks, use it to create custom alerts, and improve your investigation process.",
"customImage": "The image connector content",
"graphQueriesTableName": "GitHubAuditLogPolling_CL",
"graphQueries": [
{
"metricName": "Total events received",
"legend": "GitHub audit log events",
"baseQuery": "{{graphQueriesTableName}}"
}
],
"sampleQueries": [
{
"description": "All logs",
"query": "{{graphQueriesTableName}}\n | take 10 <change>"
}
],
"dataTypes": [
{
"name": "{{graphQueriesTableName}}",
"lastDataReceivedQuery": "{{graphQueriesTableName}}\n | summarize Time = max(TimeGenerated)\n | where isnotempty(Time)"
}
],
"connectivityCriteria": [
{
"type": "SentinelKindsV2",
"value": []
}
],
"availability": {
"status": 1,
"isPreview": true
},
"permissions": {
"resourceProvider": [
{
"provider": "Microsoft.OperationalInsights/workspaces",
"permissionsDisplayText": "read and write permissions are required.",
"providerDisplayName": "Workspace",
"scope": "Workspace",
"requiredPermissions": {
"write": true,
"read": true,
"delete": true
}
}
],
"customs": [
{
"name": "GitHub API personal token Key",
"description": "You need access to GitHub personal token, the key should have 'admin:org' scope"
}
]
},
"instructionSteps": [
{
"title": "Connect GitHub Enterprise Audit Log to Azure Sentinel",
"description": "Enable GitHub audit Logs. \n Follow [this](https://docs.github.com/en/github/authenticating-to-github/keeping-your-account-and-data-secure/creating-a-personal-access-token) to create or find your personal key",
"instructions": [
{
"parameters": {
"enable": "true",
"userRequestPlaceHoldersInput": [
{
"displayText": "Organization Name",
"requestObjectKey": "apiEndpoint",
"placeHolderName": "{{placeHolder1}}",
"placeHolderValue": ""
}
]
},
"type": "APIKey"
}
]
}
]
},
"pollingConfig": {
"auth": {
"authType": "APIKey",
"apiKeyIdentifier": "token",
"apiKeyName": "Authorization"
},
"request": {
"apiEndpoint": "https://api.github.com/organizations/{{placeHolder1}}/audit-log",
"rateLimitQps": 50,
"queryWindowInMin": 15,
"httpMethod": "Get",
"queryTimeFormat": "yyyy-MM-ddTHH:mm:ssZ",
"retryCount": 2,
"timeoutInSeconds": 60,
"headers": {
"Accept": "application/json",
"User-Agent": "Scuba"
},
"queryParameters": {
"phrase": "created:{_QueryWindowStartTime}..{_QueryWindowEndTime}"
}
},
"paging": {
"pagingType": "LinkHeader",
"pageSizeParaName": "per_page"
},
"response": {
"eventsJsonPaths": [
"$"
]
}
}
}
},
"has_error": false,
"error": null
}
Delete Data Connector
Delete data connector by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Data Connector ID | Jinja-template text containing the data connector ID for azure sentinel | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted.",
"has_error": false,
"error": null
}
Create or Update Data Connector
Create or update data connector.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Data Connector ID | Jinja-template text containing the data connector ID for azure sentinel | Required |
| Data Connector Object | Jinja-template text containing the bookmark object for azure sentinel. Example '{"kind": "Fusion","properties.alertRuleTemplateName": "f7asdfd-2ffb-45tb-b102-4asdf015c8","properties.enabled": true}' | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/dataConnectors/316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"name": "316ec55e-7138-4d63-ab18-90c8a60fd1c8",
"etag": "\"1a00b074-0000-0100-0000-606ef5bd0000\"",
"type": "Microsoft.SecurityInsights/dataConnectors",
"kind": "APIPolling",
"properties": {
"connectorUiConfig": {
"title": "GitHub Enterprise Audit Log",
"publisher": "GitHub",
"descriptionMarkdown": "The GitHub audit log connector provides the capability to ingest GitHub logs into Azure Sentinel. By connecting GitHub audit logs into Azure Sentinel, you can view this data in workbooks, use it to create custom alerts, and improve your investigation process.",
"graphQueriesTableName": "GitHubAuditLogPolling_CL",
"graphQueries": [
{
"metricName": "Total events received",
"legend": "GitHub audit log events",
"baseQuery": "{{graphQueriesTableName}}"
}
],
"sampleQueries": [
{
"description": "All logs",
"query": "{{graphQueriesTableName}}\n | take 10 <change>"
}
],
"dataTypes": [
{
"name": "{{graphQueriesTableName}}",
"lastDataReceivedQuery": "{{graphQueriesTableName}}\n | summarize Time = max(TimeGenerated)\n | where isnotempty(Time)"
}
],
"connectivityCriteria": [
{
"type": "SentinelKindsV2",
"value": []
}
],
"availability": {
"status": 1,
"isPreview": true
},
"permissions": {
"resourceProvider": [
{
"provider": "Microsoft.OperationalInsights/workspaces",
"permissionsDisplayText": "read and write permissions are required.",
"providerDisplayName": "Workspace",
"scope": "Workspace",
"requiredPermissions": {
"write": true,
"read": true,
"delete": true
}
}
],
"customs": [
{
"name": "GitHub API personal token Key",
"description": "You need access to GitHub personal token, the key should have 'admin:org' scope"
}
]
},
"instructionSteps": [
{
"title": "Connect GitHub Enterprise Audit Log to Azure Sentinel",
"description": "Enable GitHub audit Logs. \n Follow [this](https://docs.github.com/en/github/authenticating-to-github/keeping-your-account-and-data-secure/creating-a-personal-access-token) to create or find your personal key",
"instructions": [
{
"parameters": {
"enable": "true",
"userRequestPlaceHoldersInput": [
{
"displayText": "Organization Name",
"requestObjectKey": "apiEndpoint",
"placeHolderName": "{{placeHolder1}}",
"placeHolderValue": ""
}
]
},
"type": "APIKey"
}
]
}
]
},
"pollingConfig": {
"auth": {
"authType": "APIKey",
"apiKeyIdentifier": "token",
"apiKeyName": "Authorization"
},
"request": {
"apiEndpoint": "https://api.github.com/organizations/{{placeHolder1}}/audit-log",
"rateLimitQps": 50,
"queryWindowInMin": 15,
"httpMethod": "Get",
"queryTimeFormat": "yyyy-MM-ddTHH:mm:ssZ",
"retryCount": 2,
"timeoutInSeconds": 60,
"headers": {
"Accept": "application/json",
"User-Agent": "Scuba"
},
"queryParameters": {
"phrase": "created:{_QueryWindowStartTime}..{_QueryWindowEndTime}"
}
},
"paging": {
"pagingType": "LinkHeader",
"pageSizeParaName": "per_page"
},
"response": {
"eventsJsonPaths": [
"$"
]
}
},
"has_error": false,
"error": null
}
List Incidents
List incidents.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Filter | Jinja-template JSON containing the filter for azure sentinel. Example '{"filter":"{{filter}}","$orderby":"{{orderby}}","$top":"{{top}}"}' | Optional |
| Limit | Jinja-template JSON containing the limit for azure sentinel. (Default is 10000) | Optional |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"name": "73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"type": "Microsoft.SecurityInsights/incidents",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"lastModifiedTimeUtc": "2019-01-01T13:15:30Z",
"createdTimeUtc": "2019-01-01T13:15:30Z",
"lastActivityTimeUtc": "2019-01-01T13:05:30Z",
"firstActivityTimeUtc": "2019-01-01T13:00:30Z",
"description": "This is a demo incident",
"title": "My incident",
"owner": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"userPrincipalName": "[email protected]",
"assignedTo": "john doe",
"ownerType": "User"
},
"severity": "High",
"classification": "FalsePositive",
"classificationComment": "Not a malicious activity",
"classificationReason": "IncorrectAlertLogic",
"status": "Closed",
"incidentUrl": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"incidentNumber": 3177,
"labels": [],
"providerName": "Azure Sentinel",
"providerIncidentId": "3177",
"relatedAnalyticRuleIds": [
"/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/alertRules/fab3d2d4-747f-46a7-8ef0-9c0be8112bf7",
"/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/alertRules/8deb8303-e94d-46ff-96e0-5fd94b33df1a"
],
"additionalData": {
"alertsCount": 0,
"bookmarksCount": 0,
"commentsCount": 3,
"alertProductNames": [],
"tactics": [
"Persistence"
],
"techniques": [
"T1053"
],
"providerIncidentUrl": "https://security.microsoft.com/incidents/3177?tid=5b5a146c-eba8-46af-96f8-e31b50d15a3f"
}
}
}
],
"has_error": false,
"error": null
}
List Incident Alerts
List incident alerts.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja-template text containing the incident ID for azure sentinel. | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/bd794837-4d29-4647-9105-6339bfdb4e6a/resourceGroups/myRG/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/Entities/baa8a239-6fde-4ab7-a093-d09f7b75c58c",
"name": "baa8a239-6fde-4ab7-a093-d09f7b75c58c",
"type": "Microsoft.SecurityInsights/Entities",
"kind": "SecurityAlert",
"properties": {
"systemAlertId": "baa8a239-6fde-4ab7-a093-d09f7b75c58c",
"tactics": [],
"alertDisplayName": "myAlert",
"confidenceLevel": "Unknown",
"severity": "Low",
"vendorName": "Microsoft",
"productName": "Azure Security Center",
"alertType": "myAlert",
"processingEndTime": "2020-07-20T18:21:53.6158361Z",
"status": "New",
"endTimeUtc": "2020-07-20T18:21:53.6158361Z",
"startTimeUtc": "2020-07-20T18:21:53.6158361Z",
"timeGenerated": "2020-07-20T18:21:53.6158361Z",
"resourceIdentifiers": [
{
"type": "LogAnalytics",
"workspaceId": "c8c99641-985d-4e4e-8e91-fb3466cd0e5b",
"subscriptionId": "bd794837-4d29-4647-9105-6339bfdb4e6a",
"resourceGroup": "myRG"
}
],
"additionalData": {
"AlertMessageEnqueueTime": "2020-07-20T18:21:57.304Z"
},
"friendlyName": "myAlert"
}
}
],
"has_error": false,
"error": null
}
List Incident Bookmarks
List incident bookmarks.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja-template text containing the incident ID for azure sentinel. | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
"value": [
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/afbd324f-6c48-459c-8710-8d1e1cd03812",
"name": "afbd324f-6c48-459c-8710-8d1e1cd03812",
"type": "Microsoft.SecurityInsights/Entities",
"kind": "Bookmark",
"properties": {
"displayName": "SecurityEvent - 868f40f4698d",
"created": "2020-06-17T15:34:01.4265524+00:00",
"updated": "2020-06-17T15:34:01.4265524+00:00",
"createdBy": {
"objectId": "b03ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"updatedBy": {
"objectId": "b03ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"eventTime": "2020-06-17T15:34:01.4265524+00:00",
"labels": [],
"query": "SecurityEvent\r\n| take 1\n",
"queryResult": "{\"TimeGenerated\":\"2020-05-24T01:24:25.67Z\",\"Account\":\"\\\\ADMINISTRATOR\",\"AccountType\":\"User\",\"Computer\":\"SecurityEvents\",\"EventSourceName\":\"Microsoft-Windows-Security-Auditing\",\"Channel\":\"Security\",\"Task\":12544,\"Level\":\"16\",\"EventID\":4625,\"Activity\":\"4625 - An account failed to log on.\",\"AuthenticationPackageName\":\"NTLM\",\"FailureReason\":\"%%2313\",\"IpAddress\":\"176.113.115.73\",\"IpPort\":\"0\",\"LmPackageName\":\"-\",\"LogonProcessName\":\"NtLmSsp \",\"LogonType\":3,\"LogonTypeName\":\"3 - Network\",\"Process\":\"-\",\"ProcessId\":\"0x0\",\"__entityMapping\":{\"\\\\ADMINISTRATOR\":\"Account\",\"SecurityEvents\":\"Host\"}}",
"additionalData": {
"ETag": "\"3b00acab-0000-0d00-0000-5f15e4ed0000\"",
"EntityId": "afbd324f-6c48-459c-8710-8d1e1cd03812"
},
"friendlyName": "SecurityEvent - 868f40f4698d"
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/bbbd324f-6c48-459c-8710-8d1e1cd03812",
"name": "bbbd324f-6c48-459c-8710-8d1e1cd03812",
"type": "Microsoft.SecurityInsights/Entities",
"kind": "Bookmark",
"properties": {
"displayName": "SecurityEvent - 868f40f4698d",
"created": "2020-06-17T15:34:01.4265524+00:00",
"updated": "2020-06-17T15:34:01.4265524+00:00",
"createdBy": {
"objectId": "303ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"updatedBy": {
"objectId": "b03ca914-5eb6-45e5-9417-fe0797c372fd",
"email": "[email protected]",
"name": "user"
},
"eventTime": "2020-06-17T15:34:01.4265524+00:00",
"labels": [],
"query": "SecurityEvent\r\n| take 1\n",
"queryResult": "{\"TimeGenerated\":\"2020-05-24T01:24:25.67Z\",\"Account\":\"\\\\ADMINISTRATOR\",\"AccountType\":\"User\",\"Computer\":\"SecurityEvents\",\"EventSourceName\":\"Microsoft-Windows-Security-Auditing\",\"Channel\":\"Security\",\"Task\":12544,\"Level\":\"16\",\"EventID\":4625,\"Activity\":\"4625 - An account failed to log on.\",\"AuthenticationPackageName\":\"NTLM\",\"FailureReason\":\"%%2313\",\"IpAddress\":\"176.113.115.73\",\"IpPort\":\"0\",\"LmPackageName\":\"-\",\"LogonProcessName\":\"NtLmSsp \",\"LogonType\":3,\"LogonTypeName\":\"3 - Network\",\"Process\":\"-\",\"ProcessId\":\"0x0\",\"__entityMapping\":{\"\\\\ADMINISTRATOR\":\"Account\",\"SecurityEvents\":\"Host\"}}",
"additionalData": {
"ETag": "\"3b00acab-0000-0d00-0000-5f15e4ed0000\"",
"EntityId": "afbd324f-6c48-459c-8710-8d1e1cd03812"
},
"friendlyName": "SecurityEvent - 868f40f4698d"
}
}
],
"has_error": false,
"error": null
}
List Incident Entities
List incident entities.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja-template text containing the incident ID for azure sentinel. | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"entities": [
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/Entities/e1d3d618-e11f-478b-98e3-bb381539a8e1",
"name": "e1d3d618-e11f-478b-98e3-bb381539a8e1",
"type": "Microsoft.SecurityInsights/Entities",
"kind": "Account",
"properties": {
"friendlyName": "administrator",
"accountName": "administrator",
"ntDomain": "domain"
}
}
],
"metaData": [
{
"entityKind": "Account",
"count": 1
}
],
"has_error": false,
"error": null
}
Get Incident
Get incident by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja-template text containing the incident ID for azure sentinel. | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"name": "73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"type": "Microsoft.SecurityInsights/incidents",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0000\"",
"properties": {
"lastModifiedTimeUtc": "2019-01-01T13:15:30Z",
"createdTimeUtc": "2019-01-01T13:15:30Z",
"lastActivityTimeUtc": "2019-01-01T13:05:30Z",
"firstActivityTimeUtc": "2019-01-01T13:00:30Z",
"description": "This is a demo incident",
"title": "My incident",
"owner": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"userPrincipalName": "[email protected]",
"assignedTo": "john doe",
"ownerType": "User"
},
"severity": "High",
"classification": "FalsePositive",
"classificationComment": "Not a malicious activity",
"classificationReason": "InaccurateData",
"status": "Closed",
"incidentUrl": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"incidentNumber": 3177,
"labels": [],
"providerName": "Azure Sentinel",
"providerIncidentId": "3177",
"relatedAnalyticRuleIds": [
"/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/alertRules/fab3d2d4-747f-46a7-8ef0-9c0be8112bf7"
],
"additionalData": {
"alertsCount": 0,
"bookmarksCount": 0,
"commentsCount": 3,
"alertProductNames": [],
"tactics": [
"InitialAccess",
"Persistence"
],
"techniques": [
"T1091",
"T1133",
"T1053"
],
"providerIncidentUrl": "https://security.microsoft.com/incidents/3177?tid=5b5a146c-eba8-46af-96f8-e31b50d15a3f"
}
},
"has_error": false,
"error": null
}
Delete Incident
Delete incident by its ID.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja-template text containing the incident ID for azure sentinel. | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"message": "Deleted Successfully.",
"has_error": false,
"error": null
}
Create or Update Incident
Create or update incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident ID | Jinja-template text containing the incident ID for azure sentinel | Required |
| Incident Object | Jinja-template text containing the incident object for azure sentinel. Example '{"kind": "Fusion","properties.alertRuleTemplateName": "f7asdfd-2ffb-45tb-b102-4asdf015c8","properties.enabled": true}' | Required |
| Subscription ID | Jinja-template text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-template text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-template text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-template text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"name": "73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"type": "Microsoft.SecurityInsights/incidents",
"etag": "\"0300bf09-0000-0000-0000-5c37296e0001\"",
"properties": {
"lastModifiedTimeUtc": "2019-01-01T13:15:30Z",
"createdTimeUtc": "2019-01-01T13:15:30Z",
"lastActivityTimeUtc": "2019-01-01T13:05:30Z",
"firstActivityTimeUtc": "2019-01-01T13:00:30Z",
"description": "This is a demo incident",
"title": "My incident",
"owner": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"userPrincipalName": "[email protected]",
"assignedTo": "john doe",
"ownerType": "User"
},
"severity": "High",
"classification": "FalsePositive",
"classificationComment": "Not a malicious activity",
"classificationReason": "IncorrectAlertLogic",
"status": "Closed",
"incidentUrl": "https://portal.azure.com/#asset/Microsoft_Azure_Security_Insights/Incident/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5",
"incidentNumber": 3177,
"labels": [],
"providerName": "Azure Sentinel",
"providerIncidentId": "3177",
"relatedAnalyticRuleIds": [],
"additionalData": {
"alertsCount": 0,
"bookmarksCount": 0,
"commentsCount": 3,
"alertProductNames": [],
"tactics": [],
"techniques": [],
"providerIncidentUrl": "https://security.microsoft.com/incidents/3177?tid=5b5a146c-eba8-46af-96f8-e31b50d15a3f"
}
},
"has_error": false,
"error": null
}
Get Incident Comments
Gets a comment for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident Comment Id | Jinja-templated text containing the incident comment Id. | Required |
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5/comments/4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"name": "4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"etag": "\"190057d0-0000-0d00-0000-5c6f5adb0000\"",
"type": "Microsoft.SecurityInsights/incidents/comments",
"properties": {
"message": "Some message",
"createdTimeUtc": "2019-01-01T13:15:30Z",
"lastModifiedTimeUtc": "2019-01-03T11:10:30Z",
"author": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"name": "john doe",
"userPrincipalName": "[email protected]"
}
},
"has_error": false,
"error": null
}
List Incident Comments
Gets all comments for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5/comments/4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"name": "4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"etag": "\"190057d0-0000-0d00-0000-5c6f5adb0000\"",
"type": "Microsoft.SecurityInsights/incidents/comments",
"properties": {
"message": "Some message",
"createdTimeUtc": "2019-01-01T13:15:30Z",
"lastModifiedTimeUtc": "2019-01-03T11:10:30Z",
"author": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"name": "john doe",
"userPrincipalName": "[email protected]"
}
}
}
],
"has_error": false,
"error": null
}
Delete Incident Comments
Deletes a comment for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident Comment Id | Jinja-templated text containing the incident comment Id. | Required |
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted.",
"has_error": false,
"error": null
}
Create Or Update Incident Comments
Creates or updates a comment for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident Comment Id | Jinja-templated text containing the incident comment Id. | Required |
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Incident Comment Object | Jinja-templated JSON containing the incident comment object for azure sentinel. Example '{"properties": {"message": "Some message"}}' | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/73e01a99-5cd7-4139-a149-9f2736ff2ab5/comments/4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"name": "4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"etag": "\"190057d0-0000-0d00-0000-5c6f5adb0000\"",
"type": "Microsoft.SecurityInsights/incidents/comments",
"properties": {
"message": "Some message",
"createdTimeUtc": "2019-01-01T13:15:30Z",
"lastModifiedTimeUtc": "2019-01-03T13:15:30Z",
"author": {
"objectId": "2046feea-040d-4a46-9e2b-91c2941bfa70",
"email": "[email protected]",
"name": "john doe",
"userPrincipalName": "[email protected]"
}
},
"has_error": false,
"error": null
}
Get Incident Relations
Gets a relation for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Relation Name | Jinja-templated text containing the relation name. | Required |
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/afbd324f-6c48-459c-8710-8d1e1cd03812/relations/4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"name": "4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"type": "Microsoft.SecurityInsights/incidents/relations",
"etag": "190057d0-0000-0d00-0000-5c6f5adb0000",
"properties": {
"relatedResourceId": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/2216d0e1-91e3-4902-89fd-d2df8c535096",
"relatedResourceName": "2216d0e1-91e3-4902-89fd-d2df8c535096",
"relatedResourceType": "Microsoft.SecurityInsights/bookmarks"
},
"has_error": false,
"error": null
}
List Incident Relations
Gets all relations for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"value": [
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/afbd324f-6c48-459c-8710-8d1e1cd03812/relations/4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"name": "4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"type": "Microsoft.SecurityInsights/incidents/relations",
"etag": "190057d0-0000-0d00-0000-5c6f5adb0000",
"properties": {
"relatedResourceId": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/2216d0e1-91e3-4902-89fd-d2df8c535096",
"relatedResourceName": "2216d0e1-91e3-4902-89fd-d2df8c535096",
"relatedResourceType": "Microsoft.SecurityInsights/bookmarks"
}
},
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/afbd324f-6c48-459c-8710-8d1e1cd03812/relations/9673a17d-8bc7-4ca6-88ee-38a4f3efc032",
"name": "9673a17d-8bc7-4ca6-88ee-38a4f3efc032",
"type": "Microsoft.SecurityInsights/incidents/relations",
"etag": "6f714025-dd7c-46aa-b5d0-b9857488d060",
"properties": {
"relatedResourceId": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/entities/1dd267cd-8a1f-4f6f-b92c-da43ac8819af",
"relatedResourceName": "1dd267cd-8a1f-4f6f-b92c-da43ac8819af",
"relatedResourceType": "Microsoft.SecurityInsights/entities",
"relatedResourceKind": "SecurityAlert"
}
}
],
"has_error": false,
"error": null
}
Delete Incident Relations
Deletes a relation for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Relation Name | Jinja-templated text containing the relation name. | Required |
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted.",
"has_error": false,
"error": null
}
Create Or Update Incident Relations
Creates or updates a relation for a given incident.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Relation Name | Jinja-templated text containing the relation name. | Required |
| Incident Id | Jinja-templated text containing the incident Id. | Required |
| Incident Relation Object | Jinja-templated JSON containing the incident comment object for azure sentinel. Example '{"properties": {"relatedResourceId": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalInsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/2216d0e1-91e3-4902-89fd-d2df8c535096"}}' | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| Api Version | Jinja-templated text containing the API version for azure sentinel (Default is '2021-10-01') | Optional |
Output
JSON containing the following items:
{
"id": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/incidents/afbd324f-6c48-459c-8710-8d1e1cd03812/relations/4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"name": "4bb36b7b-26ff-4d1c-9cbe-0d8ab3da0014",
"type": "Microsoft.SecurityInsights/incidents/relations",
"etag": "190057d0-0000-0d00-0000-5c6f5adb0000",
"properties": {
"relatedResourceId": "/subscriptions/d0cfe6b2-9ac0-4464-9919-dccaee2e48c0/resourceGroups/myRg/providers/Microsoft.OperationalIinsights/workspaces/myWorkspace/providers/Microsoft.SecurityInsights/bookmarks/2216d0e1-91e3-4902-89fd-d2df8c535096",
"relatedResourceName": "2216d0e1-91e3-4902-89fd-d2df8c535096",
"relatedResourceType": "Microsoft.SecurityInsights/bookmarks"
},
"has_error": false,
"error": null
}
List Watchlist Items
Get all watchlist items by watchlist alias.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Watchlist Alias | Jinja-templated text containing the watchlist alias for azure sentinel | Required |
| Subscription Id | Jinja-templated text containing the subscription Id for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2022-11-01') | Optional |
| Limit | Jinja-templated text containing the limit for azure sentinel. (Default is 100) | Optional |
Output
JSON containing the following items:
{
"value":[
{
"id":"/subscriptions/74e2fd3f-10a9-415c-8989-f76f58ea418d/resourceGroups/test-integ/providers/Microsoft.OperationalInsights/workspaces/test-integ/providers/Microsoft.SecurityInsights/Watchlists/highValueAsset/WatchlistItems/a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"name":"a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"etag":"\"5800ec71-0000-0100-0000-641812ce0000\"",
"type":"Microsoft.SecurityInsights/Watchlists/WatchlistItems",
"systemData":{
"createdAt":"2023-03-20T08:01:17.0907117Z",
"createdBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"createdByType":"Application",
"lastModifiedAt":"2023-03-20T08:01:17.0907117Z",
"lastModifiedBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"lastModifiedByType":"Application"
},
"properties":{
"watchlistItemType":"watchlist-item",
"watchlistItemId":"a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"tenantId":"80a36173-9e4c-47ae-b5ae-4d5fd8f4b657",
"isDeleted":false,
"created":"2023-03-20T08:01:17.0907117+00:00",
"updated":"2023-03-20T08:01:17.0907117+00:00",
"createdBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"updatedBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"itemsKeyValue":{
"header1":"value1",
"header2":"value2"
},
"entityMapping":{
}
}
}
],
"error":null,
"has_error":false
}
Get Watchlist Item
Get watchlist item by its Id.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Watchlist Alias | Jinja-templated text containing the watchlist alias for azure sentinel | Required |
| Watchlist Item Id | Jinja-templated text containing the watchlist item Id for azure sentinel | Required |
| Subscription Id | Jinja-templated text containing the subscription Id for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2022-11-01') | Optional |
Output
JSON containing the following items:
{
"id":"/subscriptions/74e2fd3f-10a9-415c-8989-f76f58ea418d/resourceGroups/test-integ/providers/Microsoft.OperationalInsights/workspaces/test-integ/providers/Microsoft.SecurityInsights/Watchlists/highValueAsset/WatchlistItems/a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"name":"a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"etag":"\"5800ec71-0000-0100-0000-641812ce0000\"",
"type":"Microsoft.SecurityInsights/Watchlists/WatchlistItems",
"systemData":{
"createdAt":"2023-03-20T08:01:17.0907117Z",
"createdBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"createdByType":"Application",
"lastModifiedAt":"2023-03-20T08:01:17.0907117Z",
"lastModifiedBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"lastModifiedByType":"Application"
},
"properties":{
"watchlistItemType":"watchlist-item",
"watchlistItemId":"a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"tenantId":"80a36173-9e4c-47ae-b5ae-4d5fd8f4b657",
"isDeleted":false,
"created":"2023-03-20T08:01:17.0907117+00:00",
"updated":"2023-03-20T08:01:17.0907117+00:00",
"createdBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"updatedBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"itemsKeyValue":{
"header1":"value1",
"header2":"value2"
},
"entityMapping":{
}
},
"error":null,
"has_error":false
}
Delete Watchlist Item
Delete watchlist item by its Id.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Watchlist Alias | Jinja-templated text containing the watchlist alias for azure sentinel | Required |
| Watchlist Item Id | Jinja-templated text containing the watchlist item Id for azure sentinel | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2022-11-01') | Optional |
Output
JSON containing the following items:
{
"msg": "Successfully deleted.",
"has_error": false,
"error": null
}
Create or Update Watchlist Item
Create or update watchlist_item.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Watchlist Alias | Jinja-templated text containing the watchlist alias for azure sentinel | Required |
| Watchlist Item Id | Jinja-templated text containing the watchlist item Id for azure sentinel | Required |
| Action Object | Jinja-templated text containing the action object for azure sentinel. Example '{"etag": "0300bf09-0000-0000-0000-5c37296e0000", "properties": { "itemsKeyValue": { "Gateway subnet": "10.0.255.224/27", "Web Tier": "10.0.1.0/24", "Business tier": "10.0.2.0/24", "Data tier": "10.0.2.0/24", "Private DMZ in": "10.0.0.0/27", "Public DMZ out": "10.0.0.96/27"}}}' | Required |
| Subscription ID | Jinja-templated text containing the subscription ID for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2022-11-01') | Optional |
Output
JSON containing the following items:
{
"id":"/subscriptions/74e2fd3f-10a9-415c-8989-f76f58ea418d/resourceGroups/test-integ/providers/Microsoft.OperationalInsights/workspaces/test-integ/providers/Microsoft.SecurityInsights/Watchlists/testAsset/WatchlistItems/a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"name":"a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"etag":"\"7400e556-0000-0100-0000-641ae19a0000\"",
"type":"Microsoft.SecurityInsights/Watchlists/WatchlistItems",
"systemData":{
"createdAt":"2023-03-22T11:08:10.3500856Z",
"createdBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"createdByType":"Application",
"lastModifiedAt":"2023-03-22T11:08:10.3500856Z",
"lastModifiedBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"lastModifiedByType":"Application"
},
"properties":{
"watchlistItemType":"watchlist-item",
"watchlistItemId":"a26d3a54-d84c-4dcb-85a8-796493f9ad86",
"tenantId":"80a36173-9e4c-47ae-b5ae-4d5fd8f4b657",
"isDeleted":false,
"created":"2023-03-22T11:08:10.3500856+00:00",
"updated":"2023-03-22T11:08:10.3500856+00:00",
"createdBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"updatedBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"itemsKeyValue":{
"header1":"10.0.55.24/27",
"header2":"10.0.1.1/24"
},
"entityMapping":{
}
},
"error":null,
"has_error":false
}
List Watchlist
Get all watchlist.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required |
|---|---|---|
| Subscription Id | Jinja-templated text containing the subscription Id for azure sentinel | Optional |
| Resource Group Name | Jinja-templated text containing the resource group name for azure sentinel | Optional |
| Workspace | Jinja-templated text containing the workspace for azure sentinel | Optional |
| API Version | Jinja-templated text containing the API version for azure sentinel (Default is '2022-11-01') | Optional |
Output
JSON containing the following items:
{
"value":[
{
"id":"/subscriptions/74e2fd3f-10a9-415c-8989-f76f58ea418d/resourceGroups/test-integ/providers/Microsoft.OperationalInsights/workspaces/test-integ/providers/Microsoft.SecurityInsights/Watchlists/highValueAsset",
"name":"highValueAsset",
"type":"Microsoft.SecurityInsights/Watchlists",
"systemData":{
"createdAt":"2023-03-20T08:01:17.0907117Z",
"createdBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"createdByType":"Application",
"lastModifiedAt":"2023-03-20T08:01:17.0907117Z",
"lastModifiedBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"lastModifiedByType":"Application"
},
"properties":{
"watchlistId":"39cb57cf-37ef-480c-b6a7-2318bd14c659",
"displayName":"High Value Assets Watchlist",
"provider":"Microsoft",
"source":"Local file",
"itemsSearchKey":"header1",
"created":"2023-03-20T08:01:17.0907117+00:00",
"updated":"2023-03-20T08:01:17.0907117+00:00",
"createdBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"updatedBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"description":"Watchlist from CSV content",
"watchlistType":"watchlist",
"watchlistAlias":"highValueAsset",
"isDeleted":false,
"labels":[
],
"tenantId":"80a36173-9e4c-47ae-b5ae-4d5fd8f4b657",
"numberOfLinesToSkip":0,
"uploadStatus":"Complete"
}
},
{
"id":"/subscriptions/74e2fd3f-10a9-415c-8989-f76f58ea418d/resourceGroups/test-integ/providers/Microsoft.OperationalInsights/workspaces/test-integ/providers/Microsoft.SecurityInsights/Watchlists/testAsset",
"name":"testAsset",
"type":"Microsoft.SecurityInsights/Watchlists",
"systemData":{
"createdAt":"2023-03-20T08:56:01.879566Z",
"createdBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"createdByType":"Application",
"lastModifiedAt":"2023-03-20T08:56:01.879566Z",
"lastModifiedBy":"f7be553d-2bc7-4211-be04-7859b9fd150d",
"lastModifiedByType":"Application"
},
"properties":{
"watchlistId":"4e3ff120-f6aa-4d51-baa2-47c17fdcac12",
"displayName":"High Value Assets Watchlist",
"provider":"Microsoft",
"source":"Local file",
"itemsSearchKey":"header1",
"created":"2023-03-20T08:56:01.879566+00:00",
"updated":"2023-03-20T08:56:01.879566+00:00",
"createdBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"updatedBy":{
"objectId":"7aec28d0-7341-4efa-8147-6293798dc9d2",
"name":"f7be553d-2bc7-4211-be04-7859b9fd150d"
},
"description":"Watchlist from CSV content",
"watchlistType":"watchlist",
"watchlistAlias":"testAsset",
"isDeleted":false,
"labels":[
],
"tenantId":"80a36173-9e4c-47ae-b5ae-4d5fd8f4b657",
"numberOfLinesToSkip":0,
"uploadStatus":"Complete"
}
}
],
"error":null,
"has_error":false
}
Batch Query
Executes a batch of Analytics queries for data.
Input Field
Choose a connection that you have previously created and then fill in the necessary information in the following input fields to complete the connection.
| Input Name | Description | Required | ||
|---|---|---|---|---|
| Body | Jinja-templated JSON containing the batch query data for azure sentinel. Example '{"requests": [{"id": "1","body": {"query": "AppRequests | take 2"},"path": "/query","method": "POST","workspace": "d2d0e126-fa1e-4b0a-b647-250cdd471e68"},{"id": "2","body": {"query": "AppRequests | take 3"},"path": "/query","method": "POST","workspace": "d2d0e126-fa1e-4b0a-b647-250cdd471e68"}]}' | Required |
Output
JSON containing the following items:
{
"responses":[
{
"id":"1",
"status":200,
"body":{
"tables":[
{
"name":"PrimaryResult",
"columns":[
{
"name":"TenantId",
"type":"string"
},
{
"name":"Computer",
"type":"string"
},
{
"name":"TimeGenerated",
"type":"datetime"
},
{
"name":"SourceSystem",
"type":"string"
},
{
"name":"StartTime",
"type":"datetime"
},
{
"name":"EndTime",
"type":"datetime"
},
{
"name":"ResourceUri",
"type":"string"
},
{
"name":"LinkedResourceUri",
"type":"string"
},
{
"name":"DataType",
"type":"string"
},
{
"name":"Solution",
"type":"string"
},
{
"name":"BatchesWithinSla",
"type":"long"
},
{
"name":"BatchesOutsideSla",
"type":"long"
},
{
"name":"BatchesCapped",
"type":"long"
},
{
"name":"TotalBatches",
"type":"long"
},
{
"name":"AvgLatencyInSeconds",
"type":"real"
},
{
"name":"Quantity",
"type":"real"
},
{
"name":"QuantityUnit",
"type":"string"
},
{
"name":"IsBillable",
"type":"bool"
},
{
"name":"MeterId",
"type":"string"
},
{
"name":"LinkedMeterId",
"type":"string"
},
{
"name":"Type",
"type":"string"
}
],
"rows":[
]
}
]
}
},
{
"id":"2",
"status":403,
"body":{
"error":{
"message":"The provided authentication is not valid for this resource",
"code":"InvalidTokenError",
"correlationId":"aa169800-6742-4c12-a7ea-78e332d30e16",
"innererror":{
"code":"InvalidAuthenticationTokenTenant",
"message":"The access token is from the wrong issuer."
}
}
}
}
],
"error":null,
"has_error":false
}
Release Notes
v2.2.18- UTF-8 encoded the data string in all requests.v2.2.17- AddedLimitfunctionality inList Watchlist Itemsaction.v2.2.16- Unmasking Client ID in the connection params for better identification of connection in the connection pool.v2.2.13- Unmasking Tenant ID in the connection params for better identification of connection in the connection pool.v2.2.11- Added limit result optional field inList Incidentsaction.v2.2.1- Added debug logs inExecute Queryaction.v2.2.0- AddedBatch Queryaction.v2.1.1- UpdatedQueryaction: Theapi.loganalytics.ioendpoint is being replaced byapi.loganalytics.azure.com.v2.1.0- Added 5 new actions:List Watchlist Items,Get Watchlist Item,Delete Watchlist Item,Create or Update Watchlist ItemandList Watchlist.v2.0.0- Updated architecture to support IO via filesystemv1.3.3- Added 8 new actions:Create Or Update Incident Relations,Delete Incident Relations,List Incident Relations,Get Incident Relations,Create Or Update Incident Comments,Delete Incident Comments,List Incident CommentsandGet Incident Comments.v1.2.1- Added 15 new actions:Create or Update Bookmark,Create or Update Data Connector,Create or Update Incident,DELETE Bookmark,DELETE Data Connector,Delete Incident,Get Bookmark,Get Data Connector,Get Incident,List Bookmarks,List Data Connector,List Incident Alerts,List Bookmarks,List Incident EntitiesandList Incidents.v1.1.9- Bug fix forExecute queryaction throwing error when there are double quotes in the query.v1.1.4- Added 14 new actions -List Alert Rules,Get Alert Rule,Delete Alert Rule,Create Or Update Alert Rule,List Actions,Get Action,Delete Action,Create Or Update Action,List Alert Rule Templates,Get Alert Rule Template,List Automation Rules,Get Automation Rules,Delete Automation RuleandCreate Or Update Automation Rule
Updated 10 days ago