Automate your Tasks using Playbooks
Playbooks enable you to automate your security processes, including threat hunting, detections, investigations, and remediation responses - without coding!
Playbooks can ingest events or other data, process it, and take actions conditionally. You can also connect with external tools to enrich the information within the playbook and take action in those tools, such as creating tickets.
LogicHub Playbook designer can be explored by creating and editing in two different modes
Information
By default, playbooks open in Easy Mode.
To change the default mode, navigate to User Profile in the left navigation pane and under the Preferences drop-down menu > PLAYBOOK EDITOR use the toggle option to activate or deactivate the
Open playbooks in Advanced mode by default.
Uses of a Playbook
Playbook allows you to build a sequential step of actions to automate your tasks and detect threats. Some of the tasks or steps you can do in a playbook are ingesting data, executing automation, doing calculations, tasks, scoring, filtering, and enriching with external threat intelligence.
Following are some of the major uses of playbooks:
- Automated triaging to minimize alert fatigue
- Automated Incident Response
- Threat Detection and Threat Hunting
- Create a Dashboard widget
- Event type and Baseline to use as the data source in other playbooks
- Custom list to store and reuse the data in playbooks.
A wide range of steps is available in LogicHub to create most or all needed playbooks.
Guidelines
As you are building your playbook, keep in mind the following:
-
Get Event Data: Automation is usually done based on something that has happened. Whether it be logs of events from an enterprise tool or a SIEM, you can also run it on alerts already generated by another security tool. So normally, the first step of the playbook is to retrieve these events from those tools. You can do this in two ways: Event types and Integrations.
-
Identify Events/Alerts of Interest: The next step in building a playbook is to identify the events of interest. You can take action once you identify them. For example, creating a ticket when someone logs in from Russia. You can manipulate and scan the information available in the events to identify such events. To assist in the identification, you can enrich these events with the available integrations. For example, IPScan provides you with the location of an IP address. Once you get the information, you can start filtering them out.
-
Take an Action: Once you have filtered out events of interest, against each action, you can take various kinds of actions like enrichment, blacklisting IP, asking user input, creating tickets/cases within LogicHub, or outside, and many other actions using the integrations provided.
-
Streaming the Playbook: After you build the playbook, you have to stream it to automate the process you defined in the playbook to run it periodically.
Example of a Playbook
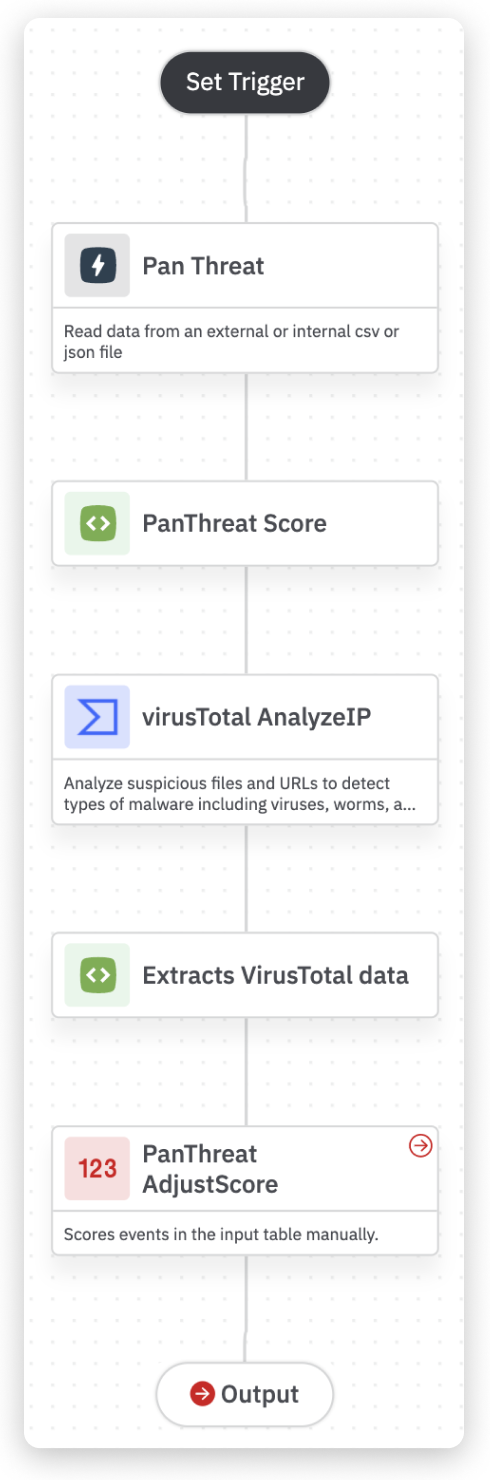
The following playbook triage flags suspicious URLs from a set of alerts.
|
How to Build a Playbook
To help you create a workflow in the playbook, we’ve broken down the process into a series of steps. The following sections will guide you through the initial setup, adding, and customizing steps.
Explore each section in the following steps to build a playbook.
- Guide to Playbook Builder
- Add a Step to Import Events
- Add a Step to Transform Data
- Add a Step to Take an Action in Integration
- Add a Step to Ask User Input
- Add a Step to Create Cases and Alerts
- Activate Playbook using Streams
Managing Playbooks
The playbooks you have permission to view will be available under My Library > Playbooks. In addition, all the playbooks that you created and shared by other users will be listed on the playbook listing page.
The playbooks and other entities will also appear in the My Library > Personal folder.
In the Personal folder, you will be able to view all the entities including the playbook that you created and those that are shared with you.
In the Playbook listing page, you will be able to view only the playbooks that you created and those that are shared with you.
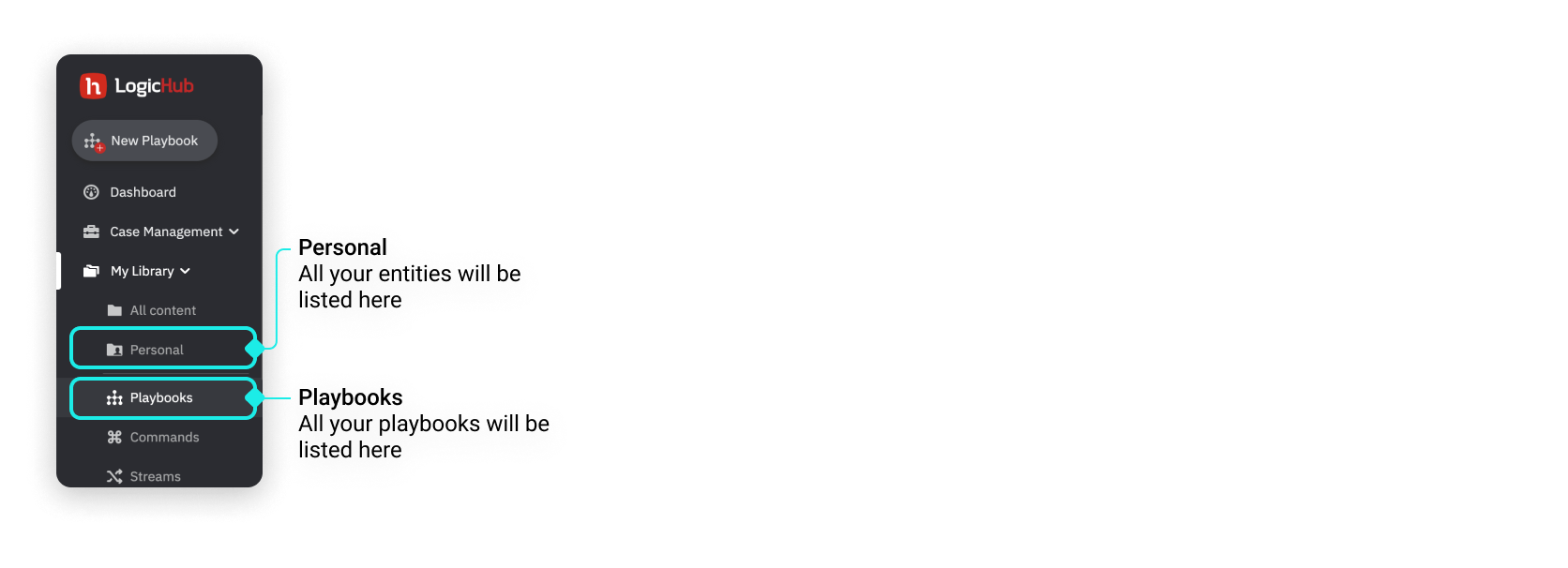
You can choose to manage the playbooks just like you manage your files on your computer or personal cloud storage. And, you can share your Playbooks with other members of your company. In addition, owners and administrators can choose to restrict playbook permissions to certain members and manage access to certain playbooks.
Related
What's Next
📍 Introduction to Playbooks
🔗 Guide to Playbook Builder
🔗 Add a Step to Import Events
🔗 Add a Step to Transform Data
🔗 Add a Step to Take Action in Integration
🔗 Add a Step to Ask User Input
🔗 Add a Step to Create Cases and Alerts
🔗 Activate Playbook using Streams
Updated over 2 years ago