Detections
Detection is the process of analyzing the complete security ecosystem to identify any malicious activity. If a threat is identified, mitigating measures must be taken to effectively neutralize it before it can exploit any existing vulnerabilities.
In LogicHub, use cases are used to manage detections. A use case is a package containing a playbook, dashboard, and commands; and the associated resources required for the use case to work. The use cases are based on MITRE detection coverage and risk management systems. LogicHub allows you to deploy the use cases by importing them and then setting up the playbook created to work in your environment.
How Detection Works in LogicHub
The playbook is the key functionality that LogicHub provides for automating your tasks. Using Playbook, you can create a triage to identify malicious activities. A playbook is part of a use case that can cover more than one detection, and one detection can be covered by multiple use cases.
A playbook can be used to identify a faulty login or malicious activity. One playbook can identify multiple detections, such as:
- Identification of a faulty login
- Detection of login attempts from malicious IP addresses
- Theft of information from a server
These are some examples of malicious activities that a playbook can handle. One playbook can handle all three detections, or more, in a single instance. (1 Playbook > 3 Detections).
LogicHub provides a unified view of the entire list of detections on the Detections page. On this page, you can choose from the following views, which you can change at any time:
- All Detections
- All Use Cases
- MITRE Coverage
Let's take a closer look at each of the page views in detail.
All Detections
The All Detections page contains a list of all the detections that LogicHub currently offers for use. On this page view, you cannot perform any actions. However, you can view the Details and Use Case of the detection on the right pane by clicking on the detection. This page allows you to filter by Category, Sub Category, Source, Status, Tactic, and Technique. Additionally, you may use the search field to perform a quick search of the detections.
All Use Cases
The All Use Cases page contains a list of all the available use cases, including MITRE-related use cases and ones that your organization has imported.
On this page, you can perform the following actions:
- Create a new use case by clicking on the New Use Case button.
- Import a use case in the following ways:
* Click on the **Available** use case and then click on the **Import** button in the right pane pop-up window.
* Select the use case by clicking on the checkbox and **Import Available** on the menu bar. You can also select multiple use cases and import in bulk.
- Additionally, click on the imported use case and choose to Edit or Publish Update.
This page allows you to filter by Category, Sub Category, Source, Status, Tactic, Technique, and MITRE Use Cases. Additionally, you may use the search field to perform a quick search of the use cases.
MITRE Coverage
MITRE ATT&CK is a standardized global knowledge base on adversary tactics and techniques derived from practical adversarial software observations made around the world. The ATT&CK knowledge base has been distilled into a series of specific threat models and methodologies used in many industries, including the cybersecurity product and service community. MITRE is a non-profit organization that maintains a catalog of tactics used by attackers to compromise computer security and network infrastructure.
MITRE helps bring communities together to solve problems and make the world safer through developing more effective tools that address real-world security problems. ATT&CK is open and available to everyone, and MITRE encourages security vendors to map their capabilities against this common framework in furtherance of improving our collective cyber-defense.
The MITRE ATT&CK architecture is used to automatically identify any tactics and techniques being deployed. Using the MITRE ATT&CK framework, we keep you protected around the clock by evaluating and probing any threats from any vector.
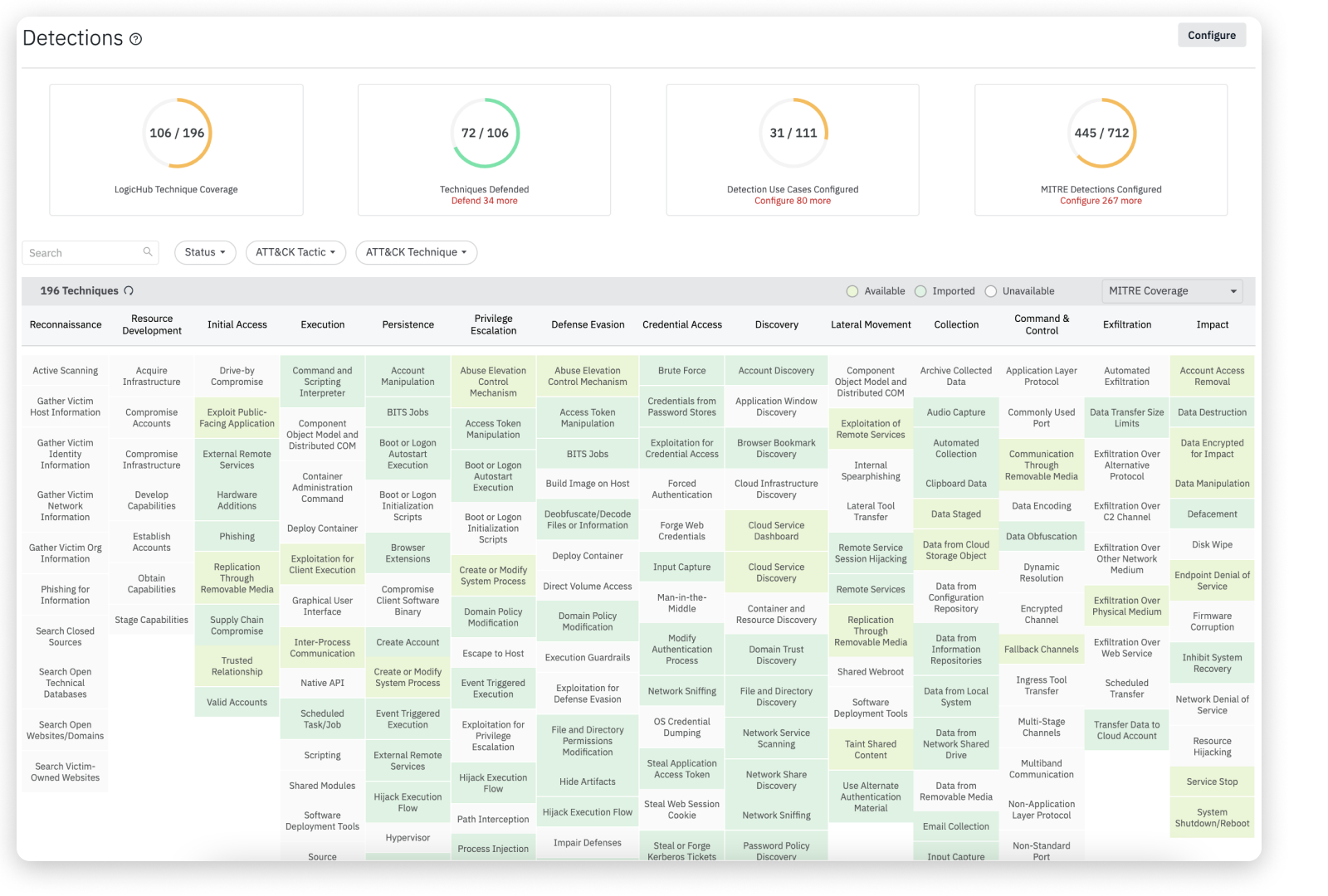
In LogicHub, the MITRE Coverage page contains a list of all the detection techniques in matrix form. The table is organized by MITRE categories, such as Initial Access and Execution and so on. Each color-coded cell represents a particular technique. The color codes for the MITRE Coverage cells are listed at the top bar:
- Available (Green): The techniques offered by LogicHub that are available for use.
- Imported (Yellowish Green): The use cases that you have imported.
- Unavailable (White): The use case is unavailable. Contact support to get more information based on your requirements.
This page allows you to filter by Tactic, Technique, and Status. Additionally, you may use the search field to perform a quick search of MITRE tactics and techniques.
Accessing Detections
- On the left navigation, click Detections to view and manage the MITRE tactics and techniques.
* The detections page provides a complete overview of the MITRE ATT&CK tactics and techniques.
The panels at the top provide a summary view of the following information:
| Techniques | Description |
|---|---|
| LogicHub Technique Coverage | Number of techniques for which LogicHub has at least one use case relative to the total number of available techniques. |
| Techniques Defended | Number of techniques for which your organization already has use cases relative to the total number of available techniques. |
| Use Cases Configured | Number of use cases that your organization has configured relative to the total number of use cases that LogicHub offers. This number is typically higher than the number of techniques defended because a technique can have multiple use cases. |
| MITRE Detections Configured | Number of MITRE use cases that your organization has configured relative to the total number of use cases that LogicHub offers. This number is typically higher than the number of techniques defended because a technique can have multiple use cases. |
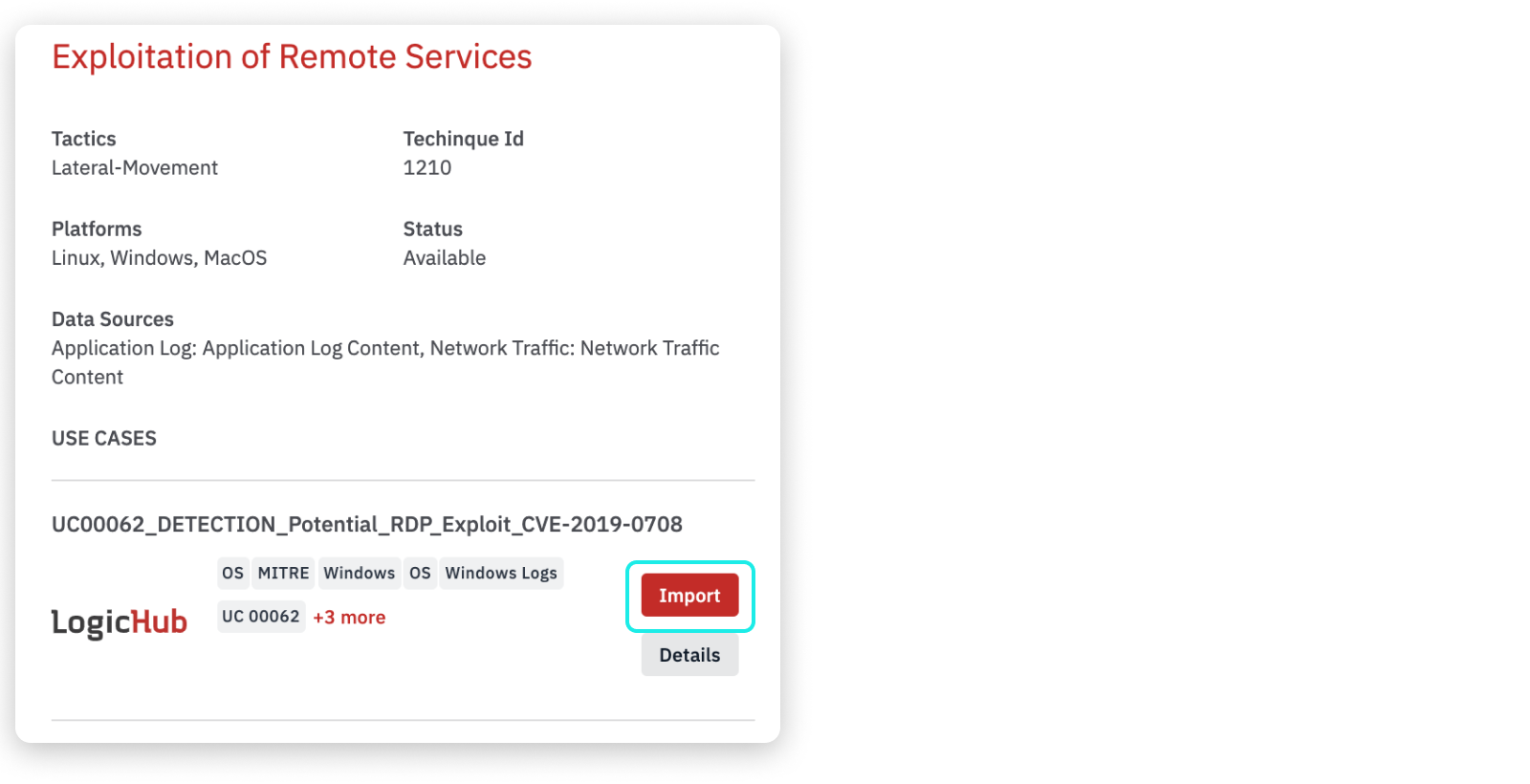
How to Import a Use Case
To import a use case into your environment:
- On the MITRE Coverage page, click on a technique to import a use case.
- The right pane opens to show details about the technique and the available use cases and suggested situations where the use case can be helpful.
- Click Import.
- The list of dependencies and conflicts for the use case is presented, along with options to resolve comments and rename items.
- When the import is complete, the Status shows as Imported in the details window, and the color will be in Yellowish Green for imported techniques in the detection page.
- After you import a use case, it will appear on your Playbooks page, where you can open and edit it just like any other playbook you created or the playbooks that are shared with you.
You can also import a use case from the use case page. To know more, see All Use Cases.
Updated over 2 years ago