LogicHub SIEM Architecture
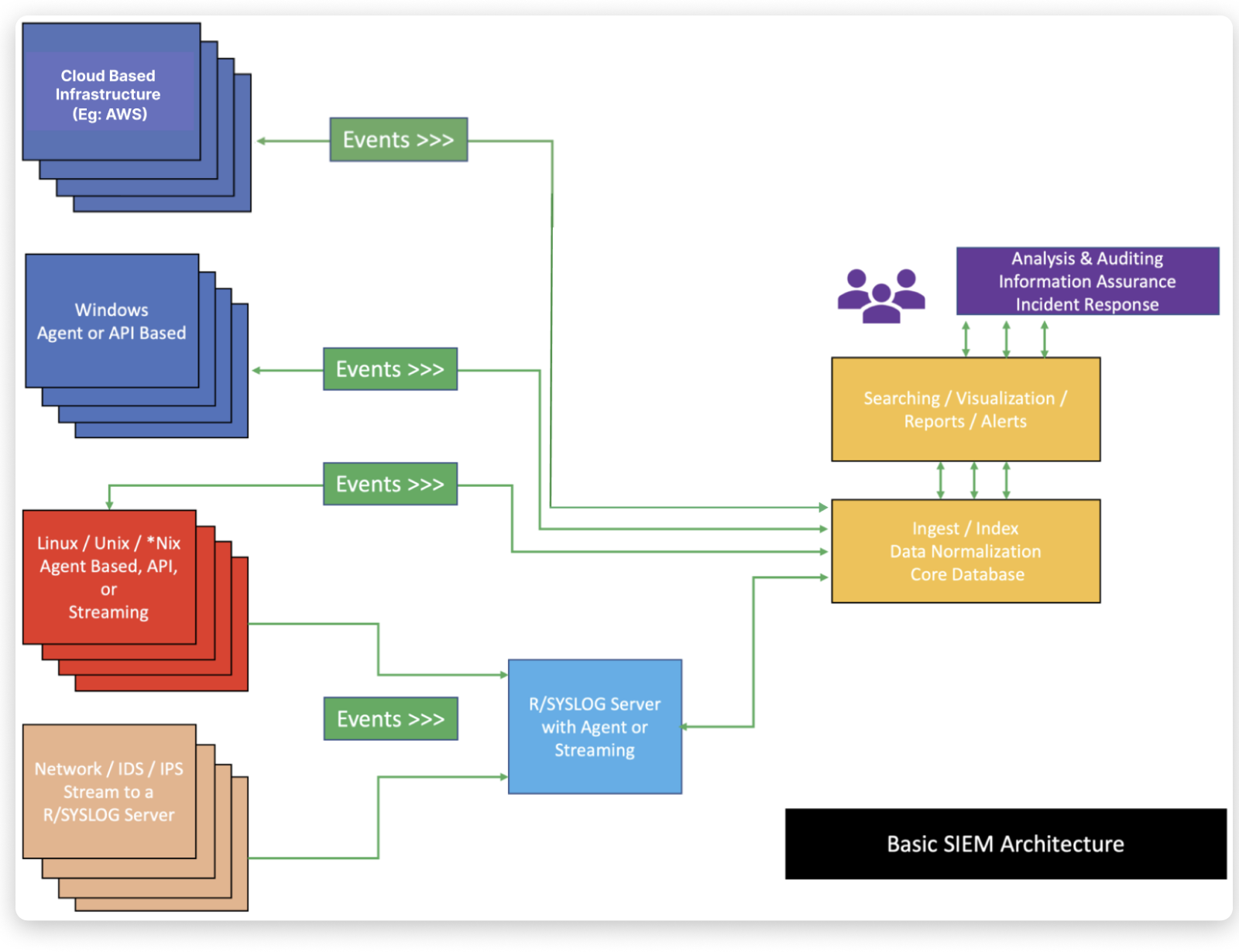
SIEM Architecture Components
The essential components of a SIEM are as follows:
- A data collector forwards selected audit logs from a host (agent-based or host-based log streaming into index and aggregation point).
- An ingest and indexing point aggregation point for parsing, correlation, and data normalization
- A search node that is used for visualization, queries, reports, and alerts (analysis takes place on a search node).
SIEM Architecture Objective
The main objectives of SIEM architecture are to maintain and manage system configuration changes, directory services, review and log auditing, and both service and user privileges with the inclusion of incident response. In addition, the applications related to Identity and Access Management (IAM) must be updated on a regular basis to bolster system security and eliminate external threats. Moreover, the SIEM architecture must provide the capabilities to present, analyze, and collect information from network and security devices.
LogicHub SIEM Architecture
LogicHub SIEM architecture is mainly built on top of data collection platform and Kibana/Elasticsearch.
Additional Information
LogicHub uses the Open Distro variant of Elasticsearch for additional convenience and ease of use.
Kibana Introduction
LogicHub makes use of Kibana as your window into Elastic Search.
Kibana
- Kibana enables you to give shape to your data and navigate the Elastic Stack. With Kibana, you can:
* Search, observe, and protect your data. From discovering documents to analyzing logs to finding security vulnerabilities, Kibana is your portal for accessing these capabilities and more.
* Analyze your data. Search for hidden insights, visualize what you’ve found in charts, gauges, maps, graphs, and more, and combine them in a dashboard.
* Manage, monitor, and secure the Elastic Stack. Manage your data, monitor the health of your Elastic Stack cluster, and control which users have access to which features.
Open Distro Introduction
Open Distro project bundled open source distributions of Elasticsearch and Kibana with Apache-2.0-licensed plugins that gave users enterprise-grade features, security, and analytics tools.
Open Distro in an Apache 2.0-licensed distribution of software that includes open-source Elasticsearch and Kibana packaged with a number of feature-adding plugins built by AWS. The open-source Elasticsearch and Kibana portions of the distribution come from the upstream downloadable artifacts ranging from versions 6.5.4 to 7.10.2. These Elasticsearch and Kibana artifacts are not forks and the current maintenance policy for upstream Elasticsearch outlines that the most recent minor release for the current major version and the most recent minor release of the previous major version will be maintained.
Open Distro Privileges
Open Distro for Elasticsearch provides several methods of authentication ranging from HTTP Basic authentication to Kerberos ticket-based authentication. Open Distro for Elasticsearch also provides a rich set of role-based access control (RBAC) features that allow locking down access to ingested log data at a very granular level. This makes securing our central logging platform very simple.
In addition, Open Distro for Elasticsearch provides SAML support for Kibana, the open source front-end UI for Elasticsearch. This SAML support allows for integrating the authentication with several Identity Providers such as AWS Single Sign-On or Okta. All communication to, from, and within the platform uses TLS encryption, which fulfills our encryption requirements as well.
Lastly, Open Distro for Elasticsearch offers alerting and monitoring services that allow setting up of custom security alerts and system health monitoring. Open Distro for Elasticsearch answered many of our needs for Ring’s Security Observability infrastructure.
Updated over 1 year ago